 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
|
Over the past six months, a new Android malware strain has made a name for itself after popping up on the radar of several antivirus companies, and annoying users thanks to a self-reinstall mechanism that has made it near impossible to remove.
Named xHelper, this malware was first spotted back in March but slowly expanded to infect more than 32,000 devices by August (per Malwarebytes), eventually reaching a total of 45,000 infections this month (per Symantec).
The malware is on a clear upward trajectory. Symantec says the xHelper crew is making on average 131 new victims per day and around 2,400 new victims per month. Most of these infections have been spotted in India, the US, and Russia.
INSTALLED VIA THIRD-PARTY APPS
According to Malwarebytes, the source of these infections is "web redirects" that send users to web pages hosting Android apps. These sites instruct users on how to side-load unofficial Android apps from outside the Play Store. Code hidden in these apps downloads the xHelper trojan. Learn more / En savoir plus / Mehr erfahren: https://gustmees.wordpress.com/2014/03/05/often-asked-questions-are-there-cyber-security-dangers-with-apps-and-whats-about-privacy/ https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Android

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Whatsapp ist mit mehr als 1,5 Milliarden Nutzern einer der populärsten Messenger auf der Welt. Das macht die App zur Zielscheibe für Cyberkriminelle. Nun warnen Sicherheitsforscher der israelischen Firma Check Point vor einer neuen Android-Schadsoftware namens "Agent Smith", die sich in rasender Geschwindigkeit verbreitet.
Whatsapp wird durch Fake ersetzt
Den Experten zufolge tarnt sich die Schadsoftware häufig als harmlose App oder als kostenloses Spiel. Sobald sie heruntergeladen wurde, durchsucht sie das Gerät nach populären Apps wie Whatsapp oder MXPlayer und ersetzt diese heimlich durch Fake-Versionen. Dazu werden mehrere bereits bekannte Android-Schwachstellen ausgenutzt. In den manipulierten Apps bekommen die Nutzer dann betrügerische Anzeigen zu sehen.
Check Point zufolge ist der Virus auch in der Lage, die Nutzer zu belauschen und sich Zugriff auf deren Bankdaten zu verschaffen. Da die Software auf dem Gerät versteckt sei und sich als vertraute App tarnt, biete sie "unendlich viele Möglichkeiten", das Gerät des Nutzers zu beschädigen. Learn more / En savoir plus / Mehr erfahren: https://gustmees.wordpress.com/2014/03/05/often-asked-questions-are-there-cyber-security-dangers-with-apps-and-whats-about-privacy/ http://www.scoop.it/t/securite-pc-et-internet/?&tag=WhatsApp...

|
Scooped by
Gust MEES
|
Forscher der Sicherheitsfirma Appthority haben 2,7 Millionen Apps für Android und iOS untersucht, berichtet The Hacker News. Bei mehr als 3.000 Anwendungen stellten die Experten fest, dass die verwendeten Firebase-Datenbanken nicht geschützt waren. Über 80 Prozent der Apps gibt es für die Android-Plattform. Die Forscher spürten Tausende von Datenbanken mit mehr als 100 Millionen Datensätzen auf, darunter viele geheime Informationen wie Kennwörter, Standorte und sogar Gesundheitsdaten. COMPUTER BILD fasst die Fakten für Sie zusammen. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Apps

|
Scooped by
Gust MEES
|
Google says that it is getting better than ever at protecting Android users against bad apps and malicious developers.
In fact, in a recent post on the Android Developers blog, the company boasts that it removed a record number of malicious apps from the official Google Play store during 2017.
How many apps did Google remove from its app marketplace after finding they violated Google Play store policies? More than 700,000. That’s an impressive 2000 or so every day, and 70% more than the number of apps removed in 2016.
Furthermore, Google says it is getting better at proactively protecting Android users from the growing menace of mobile malware:
“Not only did we remove more bad apps, we were able to identify and action against them earlier. In fact, 99% of apps with abusive contents were identified and rejected before anyone could install them. This was possible through significant improvements in our ability to detect abuse – such as impersonation, inappropriate content, or malware – through new machine learning models and techniques.”
Furthermore, Google claims it banned more than 100,000 developer accounts controlled by “bad actors” who had attempted to create new accounts and publish yet more malicious apps. Learn more / En savoir plus / Mehr erfahren: https://gustmees.wordpress.com/2014/03/05/often-asked-questions-are-there-cyber-security-dangers-with-apps-and-whats-about-privacy/ https://www.scoop.it/t/securite-pc-et-internet/?&tag=Android

|
Scooped by
Gust MEES
|
Personal data belonging to over 31 million customers of a popular virtual keyboard app has leaked online, after the app's developer failed to secure the database's server.
The server is owned by Eitan Fitusi, co-founder of AI.type, a customizable and personalizable on-screen keyboard, which boasts more than 40 million users across the world.
But the server wasn't protected with a password, allowing anyone to access the company's database of user records, totaling more than 577 gigabytes of sensitive data.
The database appears to only contain records on the app's Android users.
The discovery was found by security researchers at the Kromtech Security Center, which posted details of the exposure alongside ZDNet. The data was only secured after several attempts to contact Fitusi, who acknowledged the security lapse this weekend. The server has since been secured, but Fitusi did not respond when we asked for comment.
ZDNet obtained a portion of the database to verify. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Mobile-Security https://gustmeesde.wordpress.com/2014/12/13/mobile-security-smartphones-sind-auch-mini-computer/

|
Scooped by
Gust MEES
|
The average home now has around three connected computers and four smart mobile devices. Hardly surprising, considering that 86 per cent of us check the Internet several times a day or more, and that’s outside of work. Chatting, shopping, banking, playing games, listening to music, booking travel and managing our increasingly connected homes. The risk of cyberattack can be the furthest thing from our mind. Every year, Kaspersky Lab’s experts look at the main cyberthreats facing connected businesses over the coming 12 months, based on the trends seen during the year. For 2018, we decided to extract some top predictions that also have big implications for everyday connected life. So what could the hackers be after in 2018? Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet

|
Scooped by
Gust MEES
|
Google’s July 2017 security fixes for Android are out.
As far as we can see, there are 138 bugs listed, each with its own CVE number, of which 18 are listed with the tag “RCE”.
RCE stands for Remote Code Execution, and denotes the sort of vulnerability that could be abused by a crook to run some sort of program sent in from outside – without any user interaction.
Generally speaking, RCE bugs give outsiders a sneaky chance to trigger the sort of insecure behaviour that would usually either pop up an obvious “Are you sure?” warning, or be blocked outright by the operating system.
In other words, RCEs can typically be used for so-called “drive-by” attacks, where just visiting a web page or looking at an email might leave you silently infected with malware.
Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=Android

|
Scooped by
Gust MEES
|
Two companies have discovered that someone had covertly installed malware on 38 devices used by their employees. According to security firm Check Point, the installation of the malicious apps took place somewhere along the supply chain, after phones left the manufacturer's factory and before they arrived at the two companies. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=Mobile-Security

|
Scooped by
Gust MEES
|
(AFP) Smartphones have become a mine of personal information, holding bank data, credit card information and addresses, making them the preferred target for cyber criminals, experts warn.
"Cyber criminals go where there is value, and they have understood that the smartphone has become the preferred terminal for online shopping and payment," said Tanguy de Coatpont, head of the French branch of international anti-virus firm Kaspersky Lab at the Mobile World Congress in Barcelona.
Ransom-ware, which seizes control of computers and demands money to unblock users' data, has already started to target smartphones.
Now the devices are also being sought after as a gateway to key information about its user, experts at the phone industry's largest annual trade fair said. Learn more / En savoir plus / Mehr erfahren: https://gustmees.wordpress.com/2014/03/05/often-asked-questions-are-there-cyber-security-dangers-with-apps-and-whats-about-privacy/ http://www.scoop.it/t/apps-for-any-use-mostly-for-education-and-free/?tag=Mobile+Security http://www.scoop.it/t/securite-pc-et-internet/

|
Scooped by
Gust MEES
|
Ein Android-Updater der eher unbekannten Firma Ragentek ist nicht nur extrem unsicher, er verhält sich auch wie ein Rootkit. Das Programm steckt in etlichen Smartphone-Modellen chinesischer Hersteller, welche auch auf dem hiesigen Markt vertreten sind.
Über 2,8 Millionen Geräte kontaktierten die falschen Update-Server. Die Forscher versuchten, die Gerätemodelle zu identifizieren und Herstellern zuzuordnen.
Bild: AnubisNetworks In zahlreichen Android-Smartphone chinesischer Hersteller steckt eine Backdoor, durch die der Hersteller – oder ein Angreifer – beliebige Befehle mit Root-Rechten ausführen kann. Für das Security-Debakel ist offenbar ein Update-Prozess verantwortlich, der gewährleisten soll, dass die Geräte-Software auf dem aktuellen Stand ist.
Sie stammt von Ragentek und kommt nicht nur auf Android-Geräten dieses Herstellers zum Einsatz sondern auch bei BLU, Infinix Mobility, Beeline, Doogee, IKO Mobile, Leagoo und XOLO.
2,8 Millionen Geräte kontaktieren falschen Update-Server!!! Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?tag=Android

|
Scooped by
Gust MEES
|
28. Oktober 2016 | Drei von vier Menschen (74,6%) speichern sensible Daten auf ihrem Smartphone ie private Bilder und Videos (57,8%) sowie Kontaktdaten von Dritten (47,9%). Zudem erlauben 29,8 Prozent der Nutzer den Direktzugriff ohne Passwortabfrage auf Nutzerkonten bei sozialen Netzwerken, E-Mail- sowie Cloud-Diensten. Fast jeder Fünfte (19,7%) hat auch Apps installiert, die persönliche Daten, etwa zur eigenen Gesundheit oder Fitness, speichern und auswerten. Gleichzeitig gaben fast 20 Prozent der Nutzer an, keinerlei Sicherheitsfunktionen zum Schutz dieser kritischen Informationen eingerichtet zu haben. Nicht einmal die Hälfte (46,3%) führt regelmäßige Software-Updates durch, um Sicherheitslücken zu schließen.
Zu diesen Ergebnissen kommt eine repräsentative Online-Befragung von TNS Infratest im Auftrag des BSI anlässlich des European Cyber Security Month (ECSM) unter dem Motto "Smartphone & Co – sicher mobil"
Weitere Informationen zum Rundum-Schutz für mobile Geräte können auf der Seite "Schutz für Smartphone und Co" nachgelesen werden.

|
Scooped by
Gust MEES
|
Google warnt vor einer Schwachstelle in Android , über die sich Schadcode auf Millionen Geräte einschleusen lässt. Im Google Play Store gab es bereits eine App, die sich die Sicherheitslücke zunutze machte. Betroffen seien alle Android-Geräte, die nach dem 18. März 2016 kein Update mehr erhalten haben. Die Schwachstelle erlaubt Apps annähernden Root-Zugriff und kann das gesamte Sicherheitskonzept von Android aushebeln. Ihren Ursprung hat die Lücke in einem Fehler im Kernel von Linux, der unter dem freien Betriebssystem bereits im April 2014 geschlossen wurde. In das auf Linux aufbauende Android wurde der Patch jedoch aus unbekannten Gründe nie integriert.
Offizielle Android-Sicherheitsexperten gehen davon aus, dass sich durch die Sicherheitslücke Malware über verseuchte Apps auf Smartphones und Tablets einschleusen lässt, die dann beliebig den Kernel verändert. Die als kritisch eingestufte Lücke kann zu einer permanenten Gefährdung der Geräte führen, die nur durch das erneute Aufspielen des Betriebssystems behoben werden kann.
Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?tag=Android
|

|
Scooped by
Gust MEES
|
According to German business news outfit Handelsblatt, a number banks – whether private, co-operative or public – have either stopped offering the option or are planning to remove it by the end of the year. Among these are Postbank, Berliner Sparkasse, Consorsbank, and others.
The reasons are mostly due to security and regulation compliance
Since a lot of people do their online banking via their mobile/smart phones, hackers need to compromise only this device to get all the information needed to perform a fraudulent transaction. Users can have also their online banking credentials compromised and be targeted with fake text messages purportedly coming from the bank.
It’s also becoming common for attackers to perform SIM swapping to impersonate the target’s phone and validate the fraudulent transaction. And, finally, there have been instances of criminals exploiting long-known security vulnerabilities in the SS7 protocols to bypass German banks’ two-factor authentication and drain their customers’ bank accounts. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Two-factor+authentication

|
Scooped by
Gust MEES
|
As many as 25 million Android phones have been hit with malware that replaces installed apps like WhatsApp with evil versions that serve up adverts, cybersecurity researchers warned Wednesday.
Dubbed Agent Smith, the malware abuses previously-known weaknesses in the Android operating system, making updating to the latest, patched version of Google's operating system a priority, Israeli security company Check Point said.
Most victims are based in India, where as many as 15 million were infected. But there are more than 300,000 in the U.S., with another 137,000 in the U.K., making this one of the more severe threats to have hit Google's operating system in recent memory. Learn more / En savoir plus / Mehr erfahren: https://gustmees.wordpress.com/2014/03/05/often-asked-questions-are-there-cyber-security-dangers-with-apps-and-whats-about-privacy/ http://www.scoop.it/t/securite-pc-et-internet/?&tag=WhatsApp...

|
Scooped by
Gust MEES
|
An Android banking trojan has returned with improvements which allow it to record the screens of infected devices while also adding new techniques that help the malware remain hidden from victims.
Can Google win its battle with Android malware?
Cybercriminals are sneaking malicious apps into Google's official app store. Can they be stopped?
First detailed by cybersecurity researchers at ThreatFabric in October last year, BianLian started life as a dropper for other forms of malware, most notably the Anubis banking malware, which has stolen funds from thousands of Android users around the globe.
But the cybercriminals behind BianLian soon changed their tactics, altering the code and re-purposing the malware into a banking trojan in its own right – repeatedly bypassing protections in the official Google Play app store as a means of distributing their malicious payload. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Android

|
Scooped by
Gust MEES
|
Android Google Playstore Trickbetrüger versuchen mit gefälschten Installationszahlen unwissende Smartphone User dazu zu animieren, fragwürdige Apps zu installieren. Wir zeigen, wie man den Schwindel aufdeckt. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Android

|
Scooped by
Gust MEES
|
Sicherheitsforscher warnen vor mehreren mit Schadcode verseuchten Spiele-Apps im offiziellen App Store von Google.
Offensichtlich haben die Sicherheitsmechanismen von Google Play versagt und 27 mit Schadcode verseuchte Spiele-Apps durchgelassen. Sicherheitsforschern von Dr. Web zufolge weisen die Apps insgesamt 4,5 Millionen Downloads auf.
In ihrer Warnung listen sie die Namen der Apps auf. Stichproben zeigen, dass ein Großteil bereits nicht mehr verfügbar ist. Wer davon Apps installiert hat, sollte diese schleunigst löschen.
SDK Wurzel des Bösen
Alle Apps wurden mit dem Ya Ya Yun SDK erstellt, das neben legitimen Funktionen eben auch Trojaner-Module mitbringt. Diese sollen nach dem ersten Start einer App vom Opfer unbemerkt Code herunterladen, der im Hintergrund heimlich Webseiten öffnet und auf Werbebanner klickt. Neben dem Klickbetrug könnten die Entwickler des SDKs wahrscheinlich noch weitere Angriffsmodule bereitstellen, vermuten die Sicherheitsforscher.
Unklar ist derzeit, ob die App-Entwickler die Trojaner-Module bewusst eingebaut haben oder ob letztlich die Macher des Ya Ya Yun SDK abkassieren. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Google-Play

|
Scooped by
Gust MEES
|
68 Prozent mehr mobile Cyberangriffe seit September 2014
Kaspersky-Studie zur mobilen Bedrohungslage für Deutschland zeigt auch signifikante Steigerung (77,8 Prozent) bei Angriffen auf mobil genutzte Finanzdaten
Moskau/lngolstadt, 30. November 2017 - Das Internet erleichtert den Alltag und Cyberkriminellen möglicherweise den Zugang zum Geldbeutel vieler Smartphone-Nutzer. So sehen die Experten von Kaspersky Lab seit September 2014 bis August 2017 einen Anstieg mobiler Cyberattacken gegen deutsche Nutzer um mehr als 68 Prozent. Zugleich haben immer mehr Schädlinge auf Smartphone und Co. verfügbare Finanzdaten im Visier – mit einem Zuwachs an Attacken durch mobile Banking-Trojaner gegen deutsche Nutzer um 77,8 Prozent (auch seit September 2014 bis August 2017). Die erstmals für Deutschland von Kaspersky Lab durchgeführte Studie ,Mobile Schadprogramme in Deutschland – Panikmache oder echte Gefahr?‘ [1] zeigt: Betrugsversuche über das mobile Web sind auch in Deutschland akut. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Mobile-Security https://gustmeesde.wordpress.com/2014/12/13/mobile-security-smartphones-sind-auch-mini-computer/

|
Scooped by
Gust MEES
|
HERE ARE FIVE OF THE BEST MOBILE VPN SERVICES.
F-Secure Freedome VPN: This is one of the few VPNs CSIRO mentioned with approval. Besides providing secure VPN, it also includes built-in third-party ads and trackers blocking functionality. F-Secure is available for both Android and iOS. It's unlimited data plan starts at $49.99 a year for up to three devices.
NordVPN: Besides being a great PC VPN, NordVPN does well for both Android and iOS devices. Unlike many Apple-approved VPNs, NordVPN supports OpenVPN services. This is a must if you're running your own OpenVPN servers. Its annual plan enables you to run six devices at a time for $69 a year.
KeepSolid VPN Unlimited: This program boasts it has no ads, no tracking, and no logs. Its client app works well on Android and iOS. VPN Unlimited lets you connect up to five devices at the same time for $39.99 a year. It also offers a lifetime plan for $449.99 (currently on sale for $149.99).
Private Internet Access: With thousands of VPN servers scattered across the globe, Private Internet Access offers Android and iOS users the widest choice of geographical locations of any VPN. This service costs $39.95 annually for up to five devices simultaneously.
TorGuard: Despite its name, TorGuard is not connected to the anonymous internet Tor Project. Instead, it refers to the fact that the Android and iOS apps support BitTorrent torrents. TorGuard, however, keeps no logs whatsoever. It also supports pretty much all VPN protocols. The program runs $59.99 per year for five clients.
Even if privacy isn't a top priority for you, I urge you to get a VPN for your smartphone or tablet. Unlike your home PC, you will be using public Wi-Fi access points from time to time -- whether it's at a restaurant, airport, or hotel. None of these are particularly trustworthy, and those that don't even require a password are wide-open for attackers. A mobile VPN isn't just a good idea, it's a necessity.
Learn more / En savoir plus / Mehr erfahren: https://gustmees.wordpress.com/2013/05/27/dangers-of-wifi-in-public-places/ https://www.scoop.it/t/21st-century-learning-and-teaching/?tag=VPN https://www.scoop.it/t/securite-pc-et-internet/?&tag=VPN

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
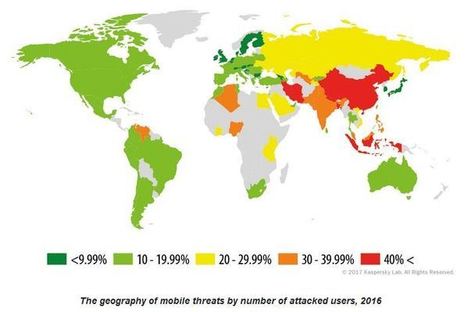
The number of malicious installation packages found striking mobile devices more than tripled in 2016 resulting in almost 40 million attacks by malicious mobile malware, according to Kaspersky Labs.
Kaspersky's Mobile Malware Evolution 2016 report noted several trends that exploded last year, including the overall growth of mobile malware with 8.5 million malicious installation packages detected and the continued rapid development of mobile banking trojans with 128,886 being spotted. In addition, there were 261,214 non-banking mobile trojans found.
“As a comparison, from 2004 to 2013 we detected over 10,000,000 malicious installation packages; in 2014 the figure was nearly 2.5 million,” said Kaspersky Labs researcher Roman Unuchek, noting the number of attacks increased dramatically staring in late June – a trend that lasted through the end of the year.
One reason behind the large number of attacks is the fact that most smart phones and other mobile devices either receive no or late operating system updates leaving the device vulnerable to attack, particularly to the number one threat of 2016, advertising trojans that exploit super-user rights.
Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=Mobile-Security

|
Scooped by
Gust MEES
|
Dead apps can be deadly
It’s not just apps live in app stores that represent a risk. Telemetry data collected by McAfee Labs shows that more than 500,000 devices still have dead apps installed and are actively used. With more than 2 million apps in each of the major app stores, malicious apps find ways through the store curators initial quality-control process.
In the past year, more than 4,000 apps were removed from Google Play, without notification to users. These users and the organisations they work for are still exposed to any vulnerabilities, privacy risks, or malware contained in these dead apps.
One recent example is a password stealer, distributed on Google Play as a variety of utilities and tools to acquire Instagram followers or analyse usage. The malware leads the user to a phishing website with a simple design that makes it difficult to distinguish between the legitimate and the fake, easily capturing users’ credentials. Learn more / En savoir plus / Mehr erfahren: https://gustmees.wordpress.com/2014/03/05/often-asked-questions-are-there-cyber-security-dangers-with-apps-and-whats-about-privacy/ http://www.scoop.it/t/apps-for-any-use-mostly-for-education-and-free/?tag=Mobile+Security

|
Scooped by
Gust MEES
|
More than a million users have downloaded a particularly sneaky Android trojan that's available on the official Google Play Store.
The Russian security firm Doctor Web found that the malware, known as Android.MulDrop.924, likes to disguise itself as games and other apps on Google Play Store and other app marketplaces.
One of its preferred masks is an app called "Multiple Accounts: 2 Accounts." It allows users to set up multiple accounts for games, email, messaging, and other software on their devices.
The app hasn't received too many bad reviews, either. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?tag=Android

|
Scooped by
Gust MEES
|
More than 100 million Android devices are vulnerable to identity theft and phishing attacks as a result of a recently discovered flaw in a phone call management app called Truecaller.
On Monday, security researchers at Cheetah Mobile published a blog post in which they discuss how the bug allows bad actors to steal users' personal information, which could open the door to subsequent attacks against the platform's users.
Truecaller is a service available for Android, iOS, and Symbian devices as well as Blackberry phones. It enables users to search for phone numbers, block incoming calls/text messages from spammers and telemarketers, as well as connect with friends. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?tag=Android
|



 Your new post is loading...
Your new post is loading...



























Over the past six months, a new Android malware strain has made a name for itself after popping up on the radar of several antivirus companies, and annoying users thanks to a self-reinstall mechanism that has made it near impossible to remove.
Named xHelper, this malware was first spotted back in March but slowly expanded to infect more than 32,000 devices by August (per Malwarebytes), eventually reaching a total of 45,000 infections this month (per Symantec).
The malware is on a clear upward trajectory. Symantec says the xHelper crew is making on average 131 new victims per day and around 2,400 new victims per month. Most of these infections have been spotted in India, the US, and Russia.
INSTALLED VIA THIRD-PARTY APPS
According to Malwarebytes, the source of these infections is "web redirects" that send users to web pages hosting Android apps. These sites instruct users on how to side-load unofficial Android apps from outside the Play Store. Code hidden in these apps downloads the xHelper trojan.
Learn more / En savoir plus / Mehr erfahren:
https://gustmees.wordpress.com/2014/03/05/often-asked-questions-are-there-cyber-security-dangers-with-apps-and-whats-about-privacy/
https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Android