Auction site confirms that hackers compromised an eBay database containing encrypted eBay passwords and other non-financial information.
Get Started for FREE
Sign up with Facebook Sign up with X
I don't have a Facebook or a X account

 Your new post is loading... Your new post is loading...
 Your new post is loading... Your new post is loading...
The "internet of things" (IoT) is becoming an increasingly growing topic of conversation both in the workplace and outside of it. It's a concept that not only has the potential to impact how we live but also how we work. But what exactly is the "internet of things" and what [...] The reality is that the IoT allows for virtually endless opportunities and connections to take place, many of which we can’t even think of or fully understand the impact of today. It’s not hard to see how and why the IoT is such a hot topic today, it certainly opens the door to a lot of opportunities but also to many challenges.
Security is big issues that is oftentimes brought up. With billions of devices being connect together what can people to do make sure that their information stays secure? Will someone be able to hack into your toaster and thereby get access to your entire network? The IoT also opens up companies all over the world to more security threats. Then we have the issue of privacy and data sharing. This is a hot button topic even today so one can only imagine how the conversation and concerns will escalate when we are talking about many billions of devices being connected. Learn more: - http://www.scoop.it/t/securite-pc-et-internet/?tag=Internet+of+things
Gust MEES's insight:
From
www
Selon des révélations de Snowden, la NSA aurait inséré des logiciels espions dans des équipements informatiques, en particulier réseau, destinés à l’exportation, mais sans a priori la collaboration des constructeurs. Learn more: - http://www.scoop.it/t/securite-pc-et-internet/?tag=NSA Via Frederic GOUTH
Gust MEES's insight:
From
www
Von selbst sollten sich die über Snapchat verschickten Fotos und Videos auflösen, und das innerhalb von zehn Sekunden. Am Wahrheitsgehalt dieses Versprechens schien bisher niemand zu zweifeln. Zu Unrecht, wie sich nun zeigte.
Gust MEES's insight:
Snapchat: Ortsdaten der User gespeichert
Un chercheur indique que près de 320 000 serveurs sont encore vulnérables à la faille Heartbleed. Pour trouver ce chiffre, il a scanné des millions de serveurs sur le port 443 qui est utilisé pour les communications TLS/SSL. A la découverte de la faille, plus de 600 000 serveurs étaient exposés. Robert Graham reste prudent sur ce chiffre de 320 000 en indiquant qu’il existe d’autres tests que le port 443 et qu’il peut donc y avoir plus de serveurs vulnérables. Learn more: - http://www.scoop.it/t/securite-pc-et-internet/?tag=Heartbleed
Gust MEES's insight:
Pour trouver ce chiffre, il a scanné des millions de serveurs sur le port 443 qui est utilisé pour les communications TLS/SSL. A la découverte de la faille, plus de 600 000 serveurs étaient exposés. Robert Graham reste prudent sur ce chiffre de 320 000 en indiquant qu’il existe d’autres tests que le port 443 et qu’il peut donc y avoir plus de serveurs vulnérables. Learn more: - http://www.scoop.it/t/securite-pc-et-internet/?tag=Heartbleed
The Reveton ransomware gang is selling a version of CryptoLocker that can infect Android devices. The version of the kit that’s being advertised by the Reveton gang has variants for victims in more than 30 countries, including the United States, UK, France, Germany, Australia and Spain.
Gust MEES's insight:
The version of the kit that’s being advertised by the Reveton gang has variants for victims in more than 30 countries, including the United States, UK, France, Germany, Australia and Spain.
From
www
Attackers can use the "Covert Redirect" vulnerability in both open-source log-in systems to steal your data and redirect you to unsafe sites.
Gust MEES's insight:
Attackers can use the "Covert Redirect" vulnerability in both open-source log-in systems to steal your data and redirect you to unsafe sites.
Research by McKinsey and the World Economic Forum points to a widening range of technology vulnerabilities and potentially huge losses in value tied to innovation. A McKinsey Quarterly article. According to McKinsey’s ongoing cyberrisk-maturity survey research, large companies reported cross-sector gaps in their risk-management capabilities. Ninety percent of those most recently surveyed had “nascent” or “developing” ones. Only 5 percent were rated “mature” overall across the practice areas studied (exhibit). Notably, we found no correlation between spending levels and risk-management maturity. Some companies spend little but do a comparatively good job of making risk-management decisions. Others spend vigorously, but without much sophistication. Even the largest firms had substantial room for improvement. In finance, for instance, senior nontechnical executives struggled to incorporate cyberrisk management into discussions on enterprise risk management and often couldn’t make informed decisions, because they lacked data.
Gust MEES's insight:
According to McKinsey’s ongoing cyberrisk-maturity survey research, large companies reported cross-sector gaps in their risk-management capabilities. Ninety percent of those most recently surveyed had “nascent” or “developing” ones. Only 5 percent were rated “mature” overall across the practice areas studied (exhibit).
Nations must be ready for a remote attack on critical infrastructure, including power and transport systems, says security expert. - Risk one: DDoS attack - Risk two: attacking critical data - Risk three: damaging infrastructure “In cyberspace there is almost no distance from espionage to cyberweapons because it is very easy to upgrade one to the other at the push of a button,” warned Kaspersky. Read more:
Gust MEES's insight:
“In cyberspace there is almost no distance from espionage to cyberweapons because it is very easy to upgrade one to the other at the push of a button,” warned Kaspersky. Read more: . 
Gust MEES's curator insight,
May 1, 2014 9:45 AM
“In cyberspace there is almost no distance from espionage to cyberweapons because it is very easy to upgrade one to the other at the push of a button,” warned Kaspersky. Read more: .
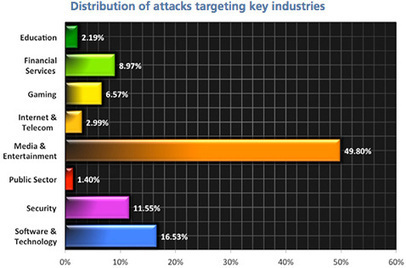
The number of bad bots has grown exponentially in recent years, driving poor internet performance for individuals and the loss of control over connected devices; wholesale theft of online intellectual property, content and data; unnecessarily high bandwidth fees; and compromised websites that are otherwise key to mission-critical functions. In fact, bad bots almost doubled as a percentage of all web traffic over the course of 2013, from 12.25% to 23.6%. And the number of mobile bots is up a staggering 1,000%. Learn more: - https://gustmees.wordpress.com/2012/07/07/bring-your-own-device-advantages-dangers-and-risks/ - http://www.scoop.it/t/securite-pc-et-internet/?tag=Botnet - http://www.scoop.it/t/securite-pc-et-internet/?tag=Mobile+Security
Akamai announced a new global DDoS attack report, which shows that in Q1, DDoS attackers relied less upon traditional botnet infection in fa...
A critical security vulnerability has been found in Adobe Reader Mobile, the version of the popular PDF Reader developed for the Android operating system, which [...] A critical security vulnerability has been found in Adobe Reader Mobile, the version of the popular PDF Reader developed for the Android operating system, which could lead to remote hackers compromising documents stored on your Android device and its SD memory card. If you were feeling smug that you had managed to avoid the Heartbleed flaw affecting up to 50 million Android users because you’re not running Android 4.1.1 of Jellybean, then perhaps you should wipe that smile off your face.
Gust MEES's insight:
A critical security vulnerability has been found in Adobe Reader Mobile, the version of the popular PDF Reader developed for the Android operating system, which could lead to remote hackers compromising documents stored on your Android device and its SD memory card. If you were feeling smug that you had managed to avoid the Heartbleed flaw affecting up to 50 million Android users because you’re not running Android 4.1.1 of Jellybean, then perhaps you should wipe that smile off your face. .
Salaries for that kind of talent are much higher in the private sector The Pentagon plans to triple its cybersecurity staff by 2016, U.S. Secretary of Defense Chuck Hagel announced recently. A few days later, FBI Supervisory Special Agent Charles Gilgen said at a conference on cybercrime that his agency’s cyber division plans to hire 1,000 agents and 1,000 analysts in the coming year. Just those two agencies are looking for 6,000 people with cybersecurity skills in the next two years. That’s a very tall order. A look at one way the government has tried to build and recruit such talent—offering university scholarships—shows why.
Gust MEES's insight:
The Pentagon plans to triple its cybersecurity staff by 2016, U.S. Secretary of Defense Chuck Hagel announced recently. A few days later, FBI Supervisory Special Agent Charles Gilgen said at a conference on cybercrime that his agency’s cyber division plans to hire 1,000 agents and 1,000 analysts in the coming year. Just those two agencies are looking for 6,000 people with cybersecurity skills in the next two years. That’s a very tall order. A look at one way the government has tried to build and recruit such talent—offering university scholarships—shows why. |
Today in a published excerpt of his forthcoming book, No Place to Hide,Glenn Greenwald reports, citing documents from 2010, that the NSA intercepts routers and servers being shipped from the United States overseas and compromises them.
Gust MEES's insight:
NSA intercepts routers and servers being shipped from the United States overseas and compromises them.
From
www
Bereits Anfang des Jahres hatte Jacob Appelbaum behauptet, die NSA fange per Post versandte Geräte ab, um darauf Spyware zu installieren. Nun untermauert Glenn Greenwald diese Anschuldigung: Betroffen seien unter anderem Router und Server von Cisco. Learn more: - http://www.scoop.it/t/securite-pc-et-internet/?tag=NSA
Gust MEES's insight:
We've recently found a vulnerability in certain Android apps that may leave user data at risk of being captured or being used to launch attacks.
Gust MEES's insight:
We’ve recently found a vulnerability in certain Android apps that may leave user data at risk of being captured or being used to launch attacks. The two affected apps we investigated are both highly popular...
Anti-malware researchers have turned the tables on cyber criminals by using the Heartbleed bug to gain access to online forums where hackers congregate. Learn more: - http://www.scoop.it/t/securite-pc-et-internet/?tag=Heartbleed
Gust MEES's insight:
Popular URL shortener Bitly is the latest cloud service to say, "Er, looks like crooks have been wandering around in our network." Learn more: - http://gustmees.wordpress.com/2013/06/23/ict-awareness-what-you-should-know/
Gust MEES's insight:
The Internet of Things (IoT) is a ubiquitous buzz-phrase these days. The idea is that just about everything we make or use could be connected, allowing anything to be remotely controlled or monitored, inspires excitement and trepidation in equal measure. The applications of a completely connected world are immense, letting us control all aspects of our lives and our environments from anywhere. =====> The dangers are similarly epic. <===== Learn more: - http://www.scoop.it/t/securite-pc-et-internet/?tag=Internet+of+things
Gust MEES's insight:
The applications of a completely connected world are immense, letting us control all aspects of our lives and our environments from anywhere. =====> The dangers are similarly epic. <===== Learn more: - http://www.scoop.it/t/securite-pc-et-internet/?tag=Internet+of+things
From
secunia
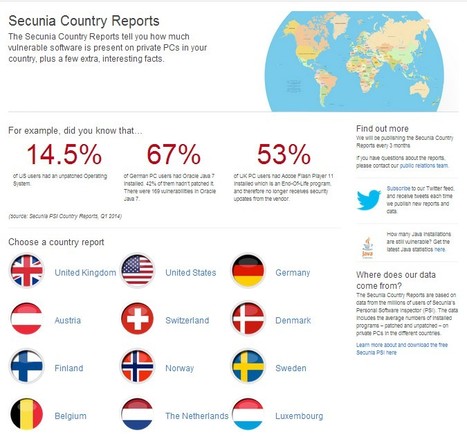
Secunia Country Reports tell the state of security among PC users by country. Read about vulnerabilities in software like Chrome, Java and Flash in your country Learn more: - http://gustmees.wordpress.com/2012/05/03/update-your-third-party-applications/ - http://gustmees.wordpress.com/2013/10/27/cyber-security-is-easy-get-the-right-reflexes/
Gust MEES's insight:
More and more organizations are transferring sensitive or confidential information to public cloud services even though more than a third expect a negative impact on security posture. In response, the use of encryption is increasing but more than half of respondents still admit their sensitive data goes unprotected when it is stored in the cloud, despite data security topping the global news agenda. Deployed correctly encryption can help organizations to migrate sensitive data and high risk applications to the cloud, allowing them to safely unlock the full potential for economic benefit the cloud can deliver.
Gust MEES's insight:
Deployed correctly encryption can help organizations to migrate sensitive data and high risk applications to the cloud, allowing them to safely unlock the full potential for economic benefit the cloud can deliver. .
Mets-en de côté, ça peut servir. La NSA ne dévoile pas toujours les failles qu'elle découvre. Il aurait fallu être naïf pour croire le contraire, et de nombreux indices et révélations vont dans ce sens depuis des années. Cela dit, que la Maison blanche l'admette et se fende d'un billet de blog pour détailler les procédures menant à la divulgation ou à la rétention de failles, c'est nouveau. Learn more: - http://www.scoop.it/t/securite-pc-et-internet/?tag=NSA
Gust MEES's insight:
La NSA ne dévoile pas toujours les failles qu'elle découvre. Il aurait fallu être naïf pour croire le contraire, et de nombreux indices et révélations vont dans ce sens depuis des années. Cela dit, que la Maison blanche l'admette et se fende d'un billet de blog pour détailler les procédures menant à la divulgation ou à la rétention de failles, c'est nouveau. Learn more: - http://www.scoop.it/t/securite-pc-et-internet/?tag=NSA 
Gust MEES's curator insight,
April 30, 2014 1:08 PM
La NSA ne dévoile pas toujours les failles qu'elle découvre. Il aurait fallu être naïf pour croire le contraire, et de nombreux indices et révélations vont dans ce sens depuis des années. Cela dit, que la Maison blanche l'admette et se fende d'un billet de blog pour détailler les procédures menant à la divulgation ou à la rétention de failles, c'est nouveau. .
Today European countries kick off the Cyber Europe 2014 (CE2014), a sophisticated cyber exercise, involving more than 600 security actors ac... More than 200 organizations and 400 cyber security professionals across Europe join forces. Twenty-nine EU and EFTA countries are participating.
Gust MEES's insight:
More than 200 organizations and 400 cyber security professionals across Europe join forces. Twenty-nine EU and EFTA countries are participating. .
A recent RAND Corporation report on the black market for hacks, cracks, data theft, botnets, and zero days tells us your hacked Amex Black fetches a decent price, but only if you're not an American. As RAND explained, the black market for cybercrime, once a "varied landscape of discrete, ad hoc networks of individuals motivated by ego and notoriety, has now become a burgeoning powerhouse of highly organized groups, often connected with traditional crime groups (e.g., drug cartels, mafias, terrorist cells) and nation-states." Learn more:
Gust MEES's insight:
The black market for cybercrime, once a "varied landscape of discrete, ad hoc networks of individuals motivated by ego and notoriety, has now become a burgeoning powerhouse of highly organized groups, often connected with traditional crime groups (e.g., drug cartels, mafias, terrorist cells) and nation-states." Learn more:
The FBI is building a massive facial recognition database that could contain as many as 52 million images by 2015, including 4.3 million non-criminal images, according to information obtained by th... Learn more:
Gust MEES's insight:
Learn more: |






























It seems that someone at eBay let the cat out of the bag earlier today, pre-releasing advice to users to change their passwords before the rest of the company was ready to make an announcement.
Well, now the company *has* made an official announcement.