10 janvier 2013: Publication intitiale
Description / Résumé
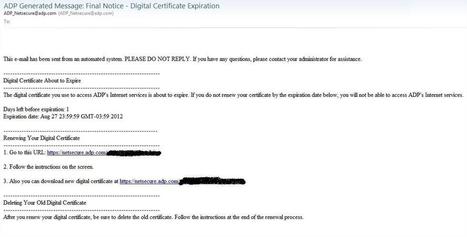
Une vulnérabilité extrêmement critique a été découverte dans le plugin Java pour votre navigateur. L'exploitation réussie de cette vulnérabilité autorise l'attaquant à prendre le contrôle de la machine victime.
La vulnérabilité a été introduite dans des kits d'exploitation communs, la rendant ainsi très répandue et de ce fait dangereuse. Le simple fait d'aller sur une page infectée peut mettre votre ordinateur en danger. Il est donc important d'éviter de cliquer sur des liens dans les e-mails.
Faites aussi attention aux publicités des sites légitimes qui pourraient être piégées.



 Your new post is loading...
Your new post is loading...














===> Be AWARE of the MALWARE! <===