 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
|
Erneut ist eine riesige Menge gehackter Nutzeraccounts ins Netz gelangt: Nach der Passwort-Sammlung "Collection #1" kursieren nun auch die Collections #2 bis #5.
Diese sind deutlich umfangreicher als Teil 1, einer ersten Einschätzung von heise Security zufolge sind sie insgesamt über 600 GByte groß. Nach Angaben des Hasso-Plattner-Institus kursieren durch die Collections #1 bis #5 nun rund 2,2 Milliarden Mail-Adressen und die dazugehörigen Passwörter.
Treffer, versenkt: Über den HPI Identity Leak Checker findet man heraus, ob sich die eigenen Mail-Adresse in den Collections #1-5 und weiteren Leaks befindet.
Die Daten sind offenbar nicht komplett neu, sondern stammen zu einem einem Großteil aus älteren Leaks. Dennoch dürfte durch die Zusammenstellung und erneute Veröffentlichung die Wahrscheinlichkeit steigern, dass die Zugansdaten von Cyber-Ganoven ausprobiert werden. Zunächst wurden die gigantischen Datenpakete in einem einschlägigen Online-Forum gehandelt, inzwischen sind sie auch über den Hoster Mega öffentlich zugänglich. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=DATA-BREACHES

|
Scooped by
Gust MEES
|
So praktisch SaaS ist. Das Konzept birgt auch große Risiken, wenn wie jetzt etwa Typeform ein SaaS-Provider das Opfer eines Datendiebstahls wird. Dann sind meist auch die Kunden des Anbieters betroffen.
Viele Unternehmen binden heutzutage immer wieder diverse Online-Umfragen in ihre Web-Seiten ein. Dabei greifen sie gerne auf vorgenerierte Formulare von externen Anbietern zu. Eines dieser Unternehmen, der spanische Software-as-a-Service-Spezialist (SaaS) Typeform, musste nun einen Datendiebstahl eingestehen, bei dem auch zahlreiche Datensätze von Kunden des Unternehmens geklaut worden sein sollen.
Der oder die Angreifer konnten sich laut Typeform Zugriff auf ein Backup von Anfang Mai dieses Jahres verschaffen. Darin enthalten waren API-Keys, Token zum Zugriff auf die von Typeform angebotenen Dienste und Zugangsdaten zu OAuth-Applikationen, aber auch Daten von Kunden, die Online-Formulare ausgefüllt hatten. Um welche Informationen es sich dabei genau handelte, teilte Typeform nicht mit. Laut Medienberichten meldeten sich aber bereits mehrere betroffene Unternehmen wie Fortnum & Mason.
Wie das Londoner Kaufhaus mitteilte, wurden ihm etwa 23.000 Datensätze gestohlen. Sie enthielten E-Mail-Adressen, Antworten auf Fragen und teilweise auch Postadressen sowie andere private Informationen der Nutzer. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=DATA-BREACHES

|
Scooped by
Gust MEES
|
A little-known, Florida-based marketing firm called Exactis may be responsible for a significant amount of personal data being exposed. According to a report from Wired, the firm left 340 million individual records on a publicly accessible server that any person could have gotten ahold of.
The leak was discovered earlier this month by security researcher Vinny Troia, founder of the New York-based security firm Night Lion Security. He reported his find to the FBI and Exactis earlier this week, and while the company has since protected the data, it’s unclear just how long it sat exposed.
So just how bad is the leak? It’s pretty bad! The data stored on the server amounts to about two terabytes worth of personal information.
Troia told Wired the database from Exactis appears to have data from “pretty much every US citizen” in it, with approximately 230 million records on American adults and 110 million records on US business contacts. That falls in line with Exactis’ own claim on its website that it has data on 218 million individuals. If the leak is truly as big as estimated, it would make for one of the largest exposures of personal information in recent memory. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=DATA-BREACHES

|
Scooped by
Gust MEES
|
Swiss telecoms giant Swisscom has admitted that it suffered a serious security breach in the autumn of 2017 that saw the theft of contact details of approximately 800,000 customers – most of whom were mobile subscribers.
Data exposed during the breach included:
Customers’ first and last names
Customers’ home addresses
Customers’ dates of birth
Customers’ telephone numbers
Interestingly, in a press release, Swisscom pointed a finger of blame at an unnamed third-party sales partner who had been granted “limited access” to the data in order that they could identify and advise customers approaching contract renewal.
That sales partner, Swisscom says, suffered its own security breach – somehow allowing its access keys to Swisscom to fall into criminal hands.
A routine check of Swisscom’s operational activities uncovered the unauthorised data access, and the offending partner’s access rights revoked.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=DATA-BREACHES

|
Scooped by
Gust MEES
|
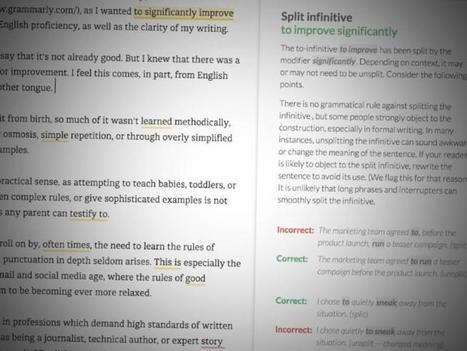
Grammarly has fixed a security bug in its Chrome extension that inadvertently allowed access to a user's account -- including their private documents and data.
Tavis Ormandy, a security researcher at Google's Project Zero who found the "high severity" vulnerability, said the browser extension exposed authentication tokens to all websites.
That means any website can access a user's documents, history, logs, and other data, the bug report said.
"I'm calling this a high severity bug, because it seems like a pretty severe violation of user expectations," said Ormandy, because "users would not expect that visiting a website gives it permission to access documents or data they've typed into other websites."
In proof-of-concept code, he explained how to trigger the bug in four lines of code.
More than 22 million users have installed the grammar-checking extension.
Ormandy filed his bug report Friday, subject to a 90-day disclosure deadline -- as is the industry standard. Grammarly issued an automatic update Monday to fix the issue.
Ormandy has in recent months examined several vulnerable web browser extensions. Earlier this year, he found a remote code execution flaw in the Cisco WebEx Chrome extension, and a data-stealing bug in the popular LastPass password manager.
A spokesperson for Grammarly did not immediately return a request for comment.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=DATA-BREACHES

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Uber sind bereits vor gut einem Jahr Daten von rund 50 Millionen Fahrgästen gestohlen worden. Der Fahrdienst-Vermittler informierte die Öffentlichkeit aber erst am Dienstag über den Vorfall.
Es gehe um Namen, E-Mail-Adressen und Telefonnummern von Nutzern rund um die Welt, erklärte Uber dem Finanzdienst Bloomberg. Außerdem hätten sich die Angreifer auch Zugriff auf Daten von etwa sieben Millionen Uber-Fahrern verschafft.
Es seien aber keine Kreditkarten-Daten oder Informationen zu Fahrten gestohlen worden, betonte die Firma.
Uber räumte nun ein, dass über die Attacke weder Behörden noch Betroffene informiert worden seien. Stattdessen seien den Hackern 100.000 Dollar (rund 85.000 Euro) bezahlt worden, damit sie die gestohlenen Daten vernichten.
„Nichts davon hätte passieren dürfen“
Uber gehe davon aus, dass die Informationen nicht verwendet worden seien, hieß es. Die Hacker seien durch eine schlecht geschützte Datenbank an die Daten gekommen. Der Uber-Sicherheitschef Joe Sullivan wurde diese Woche entlassen, wie Uber weiter mitteilte. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=DATA-BREACHES https://www.scoop.it/t/securite-pc-et-internet/?&tag=Uber

|
Scooped by
Gust MEES
|
Uber concealed a hack that affected 57 million customers and drivers, the company has confirmed.
The 2016 breach was hidden by the ride-sharing firm which paid hackers $100,000 (£75,000) to delete the data.
The company's former chief executive Travis Kalanick knew about the breach over a year ago, according to Bloomberg, which first broke the news.
The hackers found 57 million names, email addresses and mobile phone numbers, Uber said.
Within that number, 600,000 drivers had their names and license details exposed. A resource page for those affected has been set up.
Drivers have been offered free credit monitoring protection, but per Uber's statement, affected customers will not be given the same.
"While we have not seen evidence of fraud or misuse tied to the incident, we are monitoring the affected accounts and have flagged them for additional fraud protection," Uber's chief executive Dara Khosrowshahi said.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=DATA-BREACHES https://www.scoop.it/t/securite-pc-et-internet/?&tag=Uber

|
Scooped by
Gust MEES
|
(Reuters) - Microsoft Corp’s secret internal database for tracking bugs in its own software was broken into by a highly sophisticated hacking group more than four years ago, according to five former employees, in only the second known breach of such a corporate database.
The company did not disclose the extent of the attack to the public or its customers after its discovery in 2013, but the five former employees described it to Reuters in separate interviews. Microsoft declined to discuss the incident.
The database contained descriptions of critical and unfixed vulnerabilities in some of the most widely used software in the world, including the Windows operating system. Spies for governments around the globe and other hackers covet such information because it shows them how to create tools for electronic break-ins.
The Microsoft flaws were fixed likely within months of the hack, according to the former employees. Yet speaking out for the first time, these former employees as well as U.S. officials informed of the breach by Reuters said it alarmed them because the hackers could have used the data at the time to mount attacks elsewhere, spreading their reach into government and corporate networks. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=DATA-BREACHES

|
Scooped by
Gust MEES
|
Kundendaten von Deloitte offenbar gehackt
Eine der größten Unternehmens- und Buchhaltungsfirmen weltweit ist einem Bericht zufolge gehackt worden. Ein unzureichend gesicherter Admin-Account soll Zugriff auf mehrere Millionen E-Mails mit privaten Kundendaten ermöglicht haben.
Die Consulting- und Buchhaltungsberatungsfirma Deloitte ist offenbar gehackt worden. Nach Angaben des britischen Guardian ist es Angreifern gelungen, auf vertrauliche Informationen von Deloitte-Kunden zuzugreifen - wohl auch, weil das Unternehmen wichtige Accounts nicht per Zwei-Faktor-Authentifizierung abgesichert habe.
Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=DATA-BREACHES

|
Scooped by
Gust MEES
|
Le cabinet d’audit Deloitte a annoncé avoir été victime d’une attaque informatique ayant visé l’un des serveurs de mails utilisés pour échanger avec ses clients. Plus de 240.000 emails d’employés auraient été potentiellement affectés par l’attaque. Dans sa communication, la société confirme le piratage annoncé par le Guardian, mais explique que le nombre de victimes est une « fraction » des chiffres avancés dans les médias. Pour l’instant, la portée réelle de l’attaque et le nombre de sociétés touchées restent donc impossibles à déterminer : Deloitte doit sûrement avoir une petite idée, vu que ses équipes enquêtent discrètement sur l’affaire depuis maintenant six mois. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=DATA-BREACHES

|
Scooped by
Gust MEES
|
Auf den US-Finanzdienstleister Equifax ist ein Hackerangriff verübt worden, betroffen sind wohl 143 Millionen US-Bürger. In Hunderttausenden Fällen ging es um sensible Daten wie Sozialversicherungs- oder Kreditkartennummern. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=DATA-BREACHES
|

|
Scooped by
Gust MEES
|
According to the notice posted by T-Mobile on its website, the suspicious activity took place this Monday. Hackers managed to breach a database by exploiting a vulnerable API -- or application programming interface, which is a set of software building blocks that make it easier for developers to access data or technologies when creating an app.
T-Mobile cyber security staff detected the attack a short time after it began. In a statement to Motherboard, a T-Mobile spokesperson said that "less than 3%" of the company's roughly 76 million subscribers was accessed. Limiting the damage to such a small percentage is certainly a positive... but it still means that roughly 2 million T-Mobile customers were impacted.
The company's announcement states that customers' names, billing zip codes, phone numbers, email addresses and account numbers may have been exposed. The particular API that the hackers exploited was not, however, wired in to any payment card data. Social security numbers and passwords were also not accessible via the API. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=DATA-BREACHES

|
Scooped by
Gust MEES
|
Sportswear maker Adidas announced a data breach yesterday evening, which the company says it impacted shoppers who used its US website.
The company says it became aware of the breach on Tuesday, June 26, when it learned that an unauthorized party was claiming to have acquired the details of Adidas customers.
"According to the preliminary investigation, the limited data includes contact information, usernames and encrypted passwords," an Adidas spokesperson said.
"Adidas has no reason to believe that any credit card or fitness information of those consumers was impacted," he added.
The company said it's still investigating the breach with law enforcement and security firms.
A few millions impacted Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=DATA-BREACHES https://www.scoop.it/t/securite-pc-et-internet/?&tag=wearables

|
Scooped by
Gust MEES
|
A previously undisclosed flaw in Nike's website allowed anyone with a few lines of code to read server data like passwords, which could have provided greater access to the company's private systems.
An 18-year-old researcher Corben Leo discovered the flaw late last year and contacted Nike through the company's dedicated email address for reporting security flaws, which it advertises on its bug bounty page.
After hearing nothing back for more than three months, Leo contacted ZDNet, which also alerted the company to the vulnerability.
The bug exploited an out-of-band XML external entities (OOB-XXE) flaw that abused how Nike's website parses XML-based files, allowing the researcher to read files directly on the server. OOB-XXE flaws are widely seen as esoteric and difficult to carry out, but can be used to gain deep access to a server's internals. Gaining access to a server's files can disclose other avenues for exploitation, such as remote code execution or pivoting to other connected servers or databases. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=DATA-BREACHES https://www.scoop.it/t/securite-pc-et-internet/?&tag=wearables https://gustmees.wordpress.com/2013/12/21/privacy-in-the-digital-world-shouldnt-we-talk-about-it/

|
Scooped by
Gust MEES
|
Have you watched a YouTube video lately in a country where English is widely used?
If so, we’re willing to bet that you’ve seen an advert for Grammarly, an online spelling and grammar checker.
In fact, we’ll suggest you’ve seen the Grammarly ad many times, perhaps even very many times – we certainly have.
The ads seem to be working, with the product currently closing in on 1,000,000 installs in Firefox, and already claiming more than 10,000,000 in Chrome.
As the product pitch in the Firefox add-on store explains:
Once you register your new account, you will start to receive weekly emails with personalized insights and performance stats (one of our most popular new features). Working on a large project, an essay, or a blog post? No sweat. You can create and store all of your documents in your new online editor.
In other words, your Grammarly account ends up knowing a lot about you, and holding copies of a lot of what you’ve written.
A security hole in Grammarly could therefore tell crooks much more about you than you’d like them to know. Learn more / En savoir plus / Mehr erfahren. https://www.scoop.it/t/securite-pc-et-internet/?&tag=Grammarly

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
An Amazon Web Services (AWS) S3 cloud storage bucket containing information from data analytics firm Alteryx has been found publicly exposed, comprising the personal information of 123 million US households.
The S3 bucked, located at the subdomain "alteryxdownload", was found by Californian cybersecurity firm UpGuard, with its Cyber Risk Team discovering the leak on October 6, 2017.
According to UpGuard, exposed within the repository were datasets belonging to Alteryx partners, consumer credit reporting agency Experian, and the US Census Bureau.
Full datasets for both Experian's ConsumerView marketing database and the 2010 US Census were available. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Alteryx https://www.scoop.it/t/securite-pc-et-internet/?&tag=DATA-BREACHES

|
Scooped by
Gust MEES
|
Bloomberg reports on what seems to be a security scandal at Uber.
The ride-sharing firm concealed the theft of personal information related to 57 million customers and drivers, and rather than inform the concerned parties "paid hackers $100,000 to delete the data and keep the breach quiet."
The hack which Uber says is said to have happened in October 2016, and included the names, email addresses and phone numbers of 50 million Uber customers across the globe.
Bloomberg has the skinny on how the hack occurred, and it doesn't portray Uber in a good light, being the latest example of careless developers leaving internal login passwords lying around online:
Here’s how the hack went down: Two attackers accessed a private GitHub coding site used by Uber software engineers and then used login credentials they obtained there to access data stored on an Amazon Web Services account that handled computing tasks for the company. From there, the hackers discovered an archive of rider and driver information. Later, they emailed Uber asking for money, according to the company.
Joe Sullivan, Uber's chief security officer (and at one time the main security honcho at Facebook), spearheaded the company's response to the breach alongside one other employee. Both are said to have left their positions at Uber this week. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=DATA-BREACHES https://www.scoop.it/t/securite-pc-et-internet/?&tag=Uber

|
Scooped by
Gust MEES
|
Uber concealed a massive data breach for more than a year, according to a report by Bloomberg.
Hackers stole names, email addresses, and phone numbers of 57 million Uber riders around the world in a breach dating back to October 2016. Data on more than 7 million drivers was also stolen, including over 600,000 drivers' license records.
Trip records, location data, and social security numbers were not stolen in the breach, the company said.
But instead of alerting users of the breach, the company paid the hackers $100,000 to delete the data and to keep details of the breach quiet.
The company confirmed the breach, in a lengthy statement posted on Tuesday.
"As Uber's CEO, it's my job to set our course for the future, which begins with building a company that every Uber employee, partner and customer can be proud of," said Dara Khosrowshahi. "For that to happen, we have to be honest and transparent as we work to repair our past mistakes."
According to Bloomberg, two hackers broke into a private GitHub repo used by Uber software engineers, and were able to gain access to an Amazon Web Services account that handled and controlled tasks by the ride-sharing service. The hackers found a trove of rider and driver data, downloaded it, and reportedly emailed the company demanding money.
Uber has said, however, that individual riders do not need to take "any action," following the announcement. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=DATA-BREACHES https://www.scoop.it/t/securite-pc-et-internet/?&tag=Uber

|
Scooped by
Gust MEES
|
The Wild Neutron hacking group gained access to an internal database Microsoft uses to track software vulnerabilities.
David Bisson reports. On 17 October 2017, five former employees revealed that at the time of the breach Microsoft raised a number of internal alarms signaling that hackers had compromised the database it uses to track patches. The attack has been blamed on Wild Neutron, a sophisticating hacking group which has targeted Apple, Facebook, and a number of other multi-billion dollar companies. Even so, the former Microsoft workers said the database was poorly protected by just a single password. Concerned that the hacking group had stolen details on some of its open vulnerabilities for Windows and other software, Microsoft decided to look at other industry breaches and investigate the timing of those event with respect to when the flaws entered its database. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=DATA-BREACHES

|
Scooped by
Gust MEES
|
The largest hack in history just got three times worse for Yahoo. "Following an investigation with the assistance of outside forensic experts, [we believe] that all Yahoo user accounts were affected by the August 2013 theft," Suzanne Philion, an Oath spokeswoman, said in a statement Tuesday. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=DATA-BREACHES

|
Scooped by
Gust MEES
|
Deloitte, one of the world's biggest accounting, auditing, and corporate finance consulting firms, has suffered a data breach. Third hack at a financial institution this monthThe company is one of the so-called "Big Four" accounting firms, together with Ernst & Young, KPMG, and PricewaterhouseCoopers. The Big Four provide accounting and other financial services to almost all major businesses across the globe. The Deloitte hack is the third security breach at a major financial agency this month alone, after similar incidents at Equifax and the US Securities and Exchange Commission (SEC).

|
Scooped by
Gust MEES
|
Kreditkarten-, Sozialversicherungs- und Ausweisnummern von mehreren Hundert Millionen US-Amerikanern sind in falsche Hände gelangt, als Equifax monatelang gehackt war. Dazu kommen weitere Opfer in Kanada und dem Vereinigten Königreich. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=DATA-BREACHES
|



 Your new post is loading...
Your new post is loading...

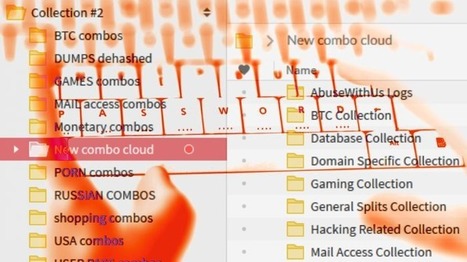




![Stolen California Voter Database Held for Bitcoin Ransom [Updated] | #CyberSecurity #DataBreaches #Ransomware #CryptoCurrency | ICT Security-Sécurité PC et Internet | Scoop.it](https://img.scoop.it/mgyGVgXn_QV_Fs7Qo01leTl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)






















Erneut ist eine riesige Menge gehackter Nutzeraccounts ins Netz gelangt: Nach der Passwort-Sammlung "Collection #1" kursieren nun auch die Collections #2 bis #5.
Diese sind deutlich umfangreicher als Teil 1, einer ersten Einschätzung von heise Security zufolge sind sie insgesamt über 600 GByte groß. Nach Angaben des Hasso-Plattner-Institus kursieren durch die Collections #1 bis #5 nun rund 2,2 Milliarden Mail-Adressen und die dazugehörigen Passwörter.
Treffer, versenkt: Über den HPI Identity Leak Checker findet man heraus, ob sich die eigenen Mail-Adresse in den Collections #1-5 und weiteren Leaks befindet.
Die Daten sind offenbar nicht komplett neu, sondern stammen zu einem einem Großteil aus älteren Leaks. Dennoch dürfte durch die Zusammenstellung und erneute Veröffentlichung die Wahrscheinlichkeit steigern, dass die Zugansdaten von Cyber-Ganoven ausprobiert werden. Zunächst wurden die gigantischen Datenpakete in einem einschlägigen Online-Forum gehandelt, inzwischen sind sie auch über den Hoster Mega öffentlich zugänglich.
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/t/securite-pc-et-internet/?&tag=DATA-BREACHES