WD-My-Cloud-NAS-Geräte kommen mit Backdoor-Account
Wer ein privates NAS aufsetzt, verspricht sich meist mehr Kontrolle über persönliche Daten als in der Cloud. Kritische Sicherheitslücken in Western-Digital-Geräten ermöglichen jedoch Angreifern, sich mit einem Backdoor-Account einzuloggen oder beliebig Dateien hochzuladen.
Einige NAS-Geräte für Heimanwender und KMU des bekannten Festplattenherstellers Western Digital werden mit einem Backdoor-Account an Kunden ausgeliefert. Der Zugang wurde mittlerweile über ein Update deaktiviert - Nutzer sollten die Geräte also dringend patchen, besonders wenn diese mit dem Internet verbunden sind.
Get Started for FREE
Sign up with Facebook Sign up with X
I don't have a Facebook or a X account

 Your new post is loading... Your new post is loading...
 Your new post is loading... Your new post is loading...
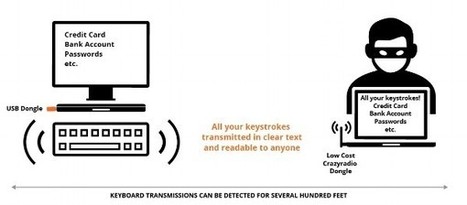
Millionen kabellose Tastaturen senden Daten im Klartext.
Kabellose Tastaturen sollten eigentlich so gebaut sein, dass die darauf getippten Informationen nur verschlüsselt übertragen werden. Millionen Geräte von mindestens acht großen Herstellern patzen dabei aber heftig, wie Forscher entdeckt haben. Selbst Laien werden vermutlich verständnislos mit dem Kopf schütteln, wenn Marc Newlin kommende Woche auf der Defcon-Konferenz in Las Vegas seinen neuen Angriff gegen regulär im Handel erhältliche Funktastaturen präsentiert. Der Mitarbeiter der IT-Sicherheitsfirma Bastille Networks und sein Team haben nach eigenen Angaben herausgefunden, dass preisgünstige kabellose Keyboards von mindestens acht großen Herstellern sämtliche auf ihnen getippten Informationen unverschlüsselt an ihren USB-Dongle senden.
Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/securite-pc-et-internet?q=cyberespionage
http://www.scoop.it/t/securite-pc-et-internet/?tag=Wireless+Mice+and+Keyboards+vulnerability
Gust MEES's insight:
Millionen kabellose Tastaturen senden Daten im Klartext.
Kabellose Tastaturen sollten eigentlich so gebaut sein, dass die darauf getippten Informationen nur verschlüsselt übertragen werden. Millionen Geräte von mindestens acht großen Herstellern patzen dabei aber heftig, wie Forscher entdeckt haben. Selbst Laien werden vermutlich verständnislos mit dem Kopf schütteln, wenn Marc Newlin kommende Woche auf der Defcon-Konferenz in Las Vegas seinen neuen Angriff gegen regulär im Handel erhältliche Funktastaturen präsentiert. Der Mitarbeiter der IT-Sicherheitsfirma Bastille Networks und sein Team haben nach eigenen Angaben herausgefunden, dass preisgünstige kabellose Keyboards von mindestens acht großen Herstellern sämtliche auf ihnen getippten Informationen unverschlüsselt an ihren USB-Dongle senden.
Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/securite-pc-et-internet?q=cyberespionage
http://www.scoop.it/t/securite-pc-et-internet/?tag=Wireless+Mice+and+Keyboards+vulnerability
Intel has fixed a major security vulnerability in a driver utility tool that could allow an attacker to remotely install malware. In a security advisory, the chipmaker confirmed that versions 2.0 to 2.3 put PCs at risk because they check Intel's servers over an unencrypted connection. An attacker could conduct a man-in-the-middle on the affected software. which could trick the software into downloading malware or other malicious files.
Gust MEES's insight:
Intel has fixed a major security vulnerability in a driver utility tool that could allow an attacker to remotely install malware. In a security advisory, the chipmaker confirmed that versions 2.0 to 2.3 put PCs at risk because they check Intel's servers over an unencrypted connection. An attacker could conduct a man-in-the-middle on the affected software. which could trick the software into downloading malware or other malicious files.
Add mice and keyboards to the list of UBS-based peripherals now suspect in any corporate environment, especially if your company or industry is targeted for an attack.
|
A security vulnerability in Intel's Active Management Technology (AMT) remote access monitoring and maintenance platform could allow attackers to bypass logins and place a backdoor on a laptop, enabling remote access and operation of the machine.
"We appreciate the security research community calling attention to the fact that some system manufacturers have not configured their systems to protect Intel Management Engine BIOS Extension (MEBx)," an Intel spokesperson told ZDNet.
"We issued guidance on best configuration practices in 2015 and updated it in November 2017, and we strongly urge OEMs to configure their systems to maximize security. Those best configuration practices include running with the least privileged access, keeping firmware, security software and operating systems up to date."
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/t/securite-pc-et-internet/?&tag=intel
Gust MEES's insight:
A security vulnerability in Intel's Active Management Technology (AMT) remote access monitoring and maintenance platform could allow attackers to bypass logins and place a backdoor on a laptop, enabling remote access and operation of the machine.
"We appreciate the security research community calling attention to the fact that some system manufacturers have not configured their systems to protect Intel Management Engine BIOS Extension (MEBx)," an Intel spokesperson told ZDNet.
"We issued guidance on best configuration practices in 2015 and updated it in November 2017, and we strongly urge OEMs to configure their systems to maximize security. Those best configuration practices include running with the least privileged access, keeping firmware, security software and operating systems up to date."
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/t/securite-pc-et-internet/?&tag=intel
Haben Sie sich jemals gefragt, was Sie tun würden, wenn Ihnen Ihr Laptop, Tablet oder Smartphone gestohlen wird? Sicher verwenden Sie Sicherheitssoftware zum Schutz vor Online-Bedrohungen. Doch wie sieht es mit den Gefahren für Ihre Hardware aus?
Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/free-tutorials-in-en-fr-de/?tag=Encryption
http://www.scoop.it/t/securite-pc-et-internet/?tag=ENCRYPTION
Gust MEES's insight:
Haben Sie sich jemals gefragt, was Sie tun würden, wenn Ihnen Ihr Laptop, Tablet oder Smartphone gestohlen wird? Sicher verwenden Sie Sicherheitssoftware zum Schutz vor Online-Bedrohungen. Doch wie sieht es mit den Gefahren für Ihre Hardware aus?
Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/free-tutorials-in-en-fr-de/?tag=Encryption
http://www.scoop.it/t/securite-pc-et-internet/?tag=ENCRYPTION
Based on internal NSA documents, Der Spiegel reveals that the spy agency planted backdoors to access computers, hard drives, routers, and other devices from companies such as Cisco, Dell, Western Digital, Seagate, Maxtor and Samsung.
According to the report, the NSA has planted back doors to access computers, hard drives, routers and other devices from companies such as Cisco, Dell, Western Digital, Seagate, Maxtor, Samsung and Huawei. The report describes a 50-page product catalog of tools and techniques that an NSA division called ANT, which stands for Advanced or Access Network Technology, uses to gain access to devices.
This follows a report that the security firm RSA intentionally allowed the NSA to create a backdoor into its encryption tokens.
Gust MEES's insight:
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=ANT
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Privacy
- http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=NSA
- http://www.scoop.it/t/securite-pc-et-internet?tag=Infographic
Looks like George ORWELL was right...
- https://en.wikipedia.org/wiki/Big_Brother_(Nineteen_Eighty-Four)
Forget PRISM, the recent NSA leaks are plain: Digital privacy doesn’t exist...
|