 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
|
Luxembourg, a tiny country with ONLY 590.667 inhabitants (January 2017) in the heart of Europe and one of the smallest countries in the world, WHERE MOST persons don’t even know where to find it on the map, shows up as an international country well known and recognized for its Cyber Security knowledge, as well as its skills in ICT. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/luxembourg-europe/?tag=Digital+L%C3%ABtzebuerg

|
Scooped by
Gust MEES
|
Ever felt like you were being watched online? You know, like when you read something about New York, and the next site you visit shows you ads for New York hotels? As it turns out, on my computer, there were more than 130 companies tracking my every move (check yours here, then install this plug-in).
These companies are basically engaging in mass surveillance. Just as governments justify tracking us to prevent terrorist attacks, these companies are tracking us online, without our consent, because a marginal 0.7 percent of the population clicks on their ads.
And it’s not just online advertisers. From e-commerce websites to physical retail stores, everyone is now racing to capture more data about us. Don’t be surprised if your insurance company starts charging you more because of how it thinks you should live your life!
Don’t get me wrong, I use Facebook, Google and all those other services. I use them because I find them useful, fun or because I don’t have an alternative. But I do it knowing very well that I am partly giving away my right to privacy. Learn more / En savoir plus / Mehr erfahren: https://gustmees.wordpress.com/2013/12/21/privacy-in-the-digital-world-shouldnt-we-talk-about-it/

|
Scooped by
Gust MEES
|
Anybody who walks or drives past new tracking billboards with a mobile phone in their pocket can be spied on without their knowledge or consent: a potential invasion of privacy that US Senator Charles E. Schumer wants the US Federal Trace Commission (FTC) to investigate.
Schumer, a Democrat from New York, delivered a briefing in Times Square on Sunday, electronic billboards blinking and scrolling behind him.
From his remarks:
A person’s cell phone should not become a James Bond-like personal tracking device for a corporation to gather information about consumers without their consent.
No one wants to be followed or tracked throughout their day, electronically or otherwise.
These new “spying” billboards raise serious questions about privacy, Schumer said. They should be investigated by the feds, and the companies behind them should be required to offer an opt-out option for consumers who feel that they violate their privacy. Learn more / En savoir plus / Mehr erfahren: https://gustmees.wordpress.com/2013/12/21/privacy-in-the-digital-world-shouldnt-we-talk-about-it/ https://gustmees.wordpress.com/2014/03/05/often-asked-questions-are-there-cyber-security-dangers-with-apps-and-whats-about-privacy/

|
Scooped by
Gust MEES
|
LinuxCon 2015 Security guru Bruce Schneier says there's a kind of cold war now being waged in cyberspace, only the trouble is we don't always know who we're waging it against.
Schneier appeared onscreen via Google Hangouts at the LinuxCon/CloudOpen/Containercon conference in Seattle on Tuesday to warn attendees that the modern security landscape is becoming increasingly complex and dangerous.
"We know, on the internet today, that attackers have the advantage," Schneier said. "A sufficiently funded, skilled, motivated adversary will get in. And we have figure out how to deal with that."
Using the example of last November's crippling online attack against Sony Pictures, Schneier said it was clear that many of these new attacks were the work of well-funded nation-states.
"Many of us, including myself, were skeptical for several months. By now it does seem obvious that it was North Korea, as amazing as that sounds," he said.
But what's troubling about many of these new attacks, he added, is that they can be hard to spot when they don't come in the form that security experts typically expect.
Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/securite-pc-et-internet/?tag=Cyberattack
http://www.scoop.it/t/securite-pc-et-internet

|
Scooped by
Gust MEES
|
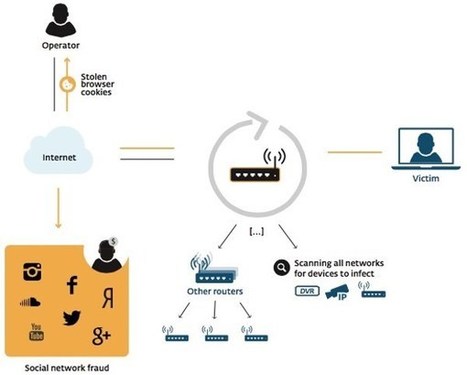
ESET researchers have issued a technical paper today, analysing a new worm that is infecting routers in order to commit social networking fraud, hijacking victims’ internet connections in order to “like” posts and pages, “view” videos and “follow” other accounts.
The malware, dubbed Linux/Moose by researchers Olivier Bilodeau and Thomas Dupuy, infects Linux-based routers and other Linux-based devices, eradicating existing malware infections it might find competing for the router’s limited resources, and automatically finding other routers to infect.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Router

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
3 million strong RAMNIT botnet taken down
Posted on 25.02.2015
The National Crime Agency’s National Cyber Crime Unit (NCCU) worked with law enforcement colleagues in the Netherlands, Italy and Germany, co-ordinated through Europol’s European Cybercrime Centre (EC3), to shut down command and control servers used by the RAMNIT botnet.
RAMNIT spread malware via seemingly trustworthy links sent out on phishing emails or social networking websites. If users running Windows clicked on the links, the malware would be installed, infecting the computer. Infected computers would then be under the control of criminals, enabling them to access personal or banking information, steal passwords and disable antivirus protection.
Investigators believe that RAMNIT may have infected over three million computers worldwide, with around 33,000 of those being in the UK. It has so far largely been used to attempt to take money from bank accounts. Analysis is now taking place on the servers and an investigation is ongoing.

|
Scooped by
Gust MEES
|
Über eine gravierende Sicherheitslücke in alten Versionen des CMS Typo3 kann sich jeder authentifizieren, der nur den Namen eines registrierten Benutzers kennt. Es gibt Updates und einen Patch.

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Seit Jahren kopieren NSA und GCHQ bei den Herstellern von SIM-Karten und Smart Cards die zugehörigen Schlüssel ab. Damit können sie die übertragenen Informationen mitlesen und manipulieren. Auch die Rechnungssysteme vieler Mobilfunker sind unterwandert.
Der britische Geheimdienst GCHQ und die US-amerikanische NSA haben schon vor Jahren die Sicherheitsvorkehrungen der Chiphersteller ausgehebelt. Also sind SIM-Karten, elektronische Reisepässe, Kredit- und Debitkarten, elektronische Türöffner, TAN-Generatoren und so weiter unsicher. Den darin verbauten Chips und den mit ihnen fix verbundenen Schlüsseln kann nicht mehr vertraut werden. Die Dienste können beispielsweise mobile Übertragungen einfach mitlesen oder rückwirkend entschlüsseln. Und es ist schlimmer.
SIM Cards Have Finally Been Hacked, And The Flaw Could Affect Millions Of Phones
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=SIM-Cards

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Moskau/lngolstadt, 17. Februar 2015 Kaspersky Lab enttarnt die Cyberspionagegruppe „Desert Falcons“, die sich gegen verschiedene hochrangige Organisationen und Einzelpersonen im Nahen Osten richtet [1]. Damit konnten die IT-Sicherheitsexperten erstmals eine Gruppe von Cybersöldnern aus dem arabischen Raum enttarnen, die offenbar über das komplette Spektrum von Cyberspionagemitteln verfügt.
Die Gruppe startete ihre Aktivitäten bereits im Jahr 2011, seit dem Jahr 2013 werden Rechner infiziert. Den Experten von Kaspersky Lab zufolge erreichte die Kampagne ihren Höhepunkt zu Beginn des Jahres 2015 [2].
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Who Will Own Your Data If the Tech Bubble Bursts?
Corporations, data brokers, and even criminals might buy failed companies just for their users’ personal information. Desperate companies will resort, if they can, to selling the detailed data they’ve meticulously collected about their users—whether it’s personally identifiable information, data about preferences, habits, and hobbies, or national-security files. That data, formerly walled-off and spoon-fed only to paying advertisers, would be attractive to both licit and criminal buyers. Easily searchable datasets could generate new innovations and investments—but it would be difficult to know who’s buying up sensitive datasets, and why. If contracts and privacy policies prevent a floundering company from selling user data, there’s still another way to profit. Most privacy policies that promise not to sell user data include a caveat in case of bankruptcy or sale. In fact, a New York Times analysis of the top 100 websites in the U.S. last year found that 85 of them include clauses in their privacy policies like this one from Facebook: If the ownership or control of all or part of our Services or their assets changes, we may transfer your information to the new owner.
Learn more / En savoir plus / Mehr erfahren: https://gustmees.wordpress.com/2013/12/21/privacy-in-the-digital-world-shouldnt-we-talk-about-it/

|
Scooped by
Gust MEES
|
Password Day is a day for "taking our passwords to the next level" - here are five traditions the crooks really don't want us to start.

|
Scooped by
Gust MEES
|
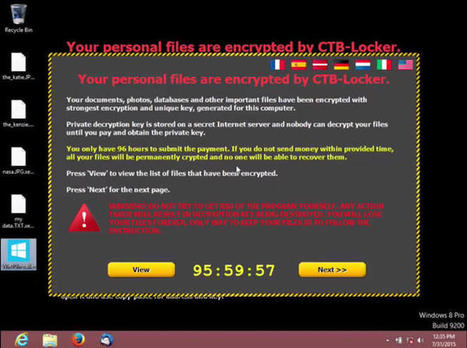
Just days after Microsoft released its latest operating system, hackers have begun targeting soon-to-be Windows 10 users with an emerging kind of malware.
Cisco security researchers are warning users against opening email attachments purporting to be from the software giant. The "ransomware" malware, which encrypts files until a ransom is paid, is being sent as part of an email spam campaign.

|
Scooped by
Gust MEES
|
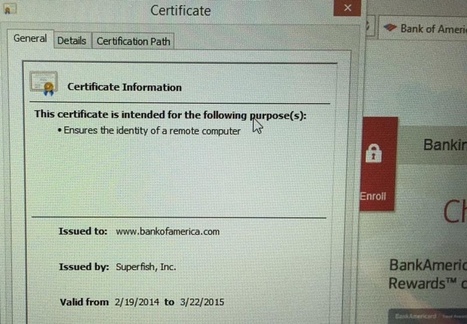
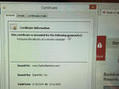
Lenovo simply can't catch a break. After the massive negative attention it received for their ill-advised decision to ship some of its notebooks with pre-installed adware that also uses MITM SSL certificates, for a short time on Wednesday their main domain - Lenovo.com - has been hijacked and effectively defaced by the hacker collective Lizard Squad.
The defaced page showed a slideshow of photos of two youngsters - according to Brian Krebs, they are Ryan King (aka “Starfall”) and Rory Andrew Godfrey (“KMS”), two former members of the hacker collective Hack The Planet - accompanied with music. The reason for the defacement is purportedly Lenovo's Superfish blunder.
The defaced page pointed to Lizard Squad's Twitter feed and served as an advertisement for its LizardStresser DoS service.
The hackers didn't compromise Lenovo's servers. Instead, they (apparently) compromised those of Web Commerce Communications (Webnic.cc), a popular Malaysia-based Internet registrar with whom the Lenovo domain is registered.
Learn more:
- http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=LENOVO
- http://www.scoop.it/t/securite-pc-et-internet/?tag=LENOVO

|
Scooped by
Gust MEES
|
This report was prepared by INSS and CSFI to create better cyber situational awareness of the nature and scope of threats to national security worldwide in the domains of cyberspace and open source intelligence. It is provided to Federal, State, Local, Tribal, Territorial and private sector officials to aid in the identification and development of appropriate actions, priorities and follow-up measures.

|
Scooped by
Gust MEES
|
Symantec Intelligence Report January 2015 [pdf] | CyberSecurity

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Die Geheimdienste der USA und Großbritanniens können offenbar die SIM-Karten in Mobiltelefonen entschlüsseln. Das berichtet die Internetseite "The Intercept". Handys seien somit unauffällig anzapfbar. Der Bericht bezieht sich auf ein Snowden-Papier.
===> Der gläserne Surfer!!! <===
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=SIM-Cards

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
|



 Your new post is loading...
Your new post is loading...


























Luxembourg, a tiny country with ONLY 590.667 inhabitants (January 2017) in the heart of Europe and one of the smallest countries in the world, WHERE MOST persons don’t even know where to find it on the map, shows up as an international country well known and recognized for its Cyber Security knowledge, as well as its skills in ICT.
Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/luxembourg-europe/?tag=Digital+L%C3%ABtzebuerg