 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
|
Another day, another Linux community with malware woes.
Last time it was Gentoo, a hard-core, source-based Linux distribution that is popular with techies who like to spend hours tweaking their entire operating sytem and rebuilding all their software from scratch to wring a few percentage points of performance out of it.
That sort of thing isn’t for everyone, but it’s harmless fun and it does give you loads of insight into how everything fits together.
That sets it apart from distros such as ElementaryOS and Mint, which rival and even exceed Windows and macOS for ease of installation and use, but don’t leave you with much of a sense of how it all actually works.
This time, the malware poisoning happened to Arch Linux, another distro we’d characterise as hard-core, though very much more widely used than Gentoo.
Three downloadable software packages in the AUR, short for Arch User Respository, were found to have been rebuilt so they contained what you might (perhaps slightly unkindly) refer to as zombie downloader robot overlord malware.
Bots or zombies are malware programs that call home to fetch instructions from the crooks on what to do next.

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Another flimsy justification for mass surveillance bites the dust— the Second Circuit court ruled today that Section 215 of the Patriot Act does not give the National Security Agency any authority to collect metadata. In other words: the NSA’s phone snooping program is straight-up unlawful.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=NSA

|
Scooped by
Gust MEES
|
Ein Rootkit, das unabhängig vom Betriebssystem operiert, sämtlichen Speicher auslesen kann und durch den Tausch der Festplatte im System nicht gestoppt wird – was klingt wie eine IT-Gruselgeschichte haben zwei Forscher nun öffentlich präsentiert.

|
Scooped by
Gust MEES
|
Die Bürgerrechtsorganisation American Civil Liberties Union (ACLU) hat im Namen der Wikimedia Foundation und weiteren US-Organisationen Klage gegen die NSA eingereicht. Die Bürgerrechtler bezweifeln, dass die massenhafte Speicherung von Kommunikationsdaten verfassungskonform ist.

|
Scooped by
Gust MEES
|
3 million strong RAMNIT botnet taken down
Posted on 25.02.2015
The National Crime Agency’s National Cyber Crime Unit (NCCU) worked with law enforcement colleagues in the Netherlands, Italy and Germany, co-ordinated through Europol’s European Cybercrime Centre (EC3), to shut down command and control servers used by the RAMNIT botnet.
RAMNIT spread malware via seemingly trustworthy links sent out on phishing emails or social networking websites. If users running Windows clicked on the links, the malware would be installed, infecting the computer. Infected computers would then be under the control of criminals, enabling them to access personal or banking information, steal passwords and disable antivirus protection.
Investigators believe that RAMNIT may have infected over three million computers worldwide, with around 33,000 of those being in the UK. It has so far largely been used to attempt to take money from bank accounts. Analysis is now taking place on the servers and an investigation is ongoing.

|
Scooped by
Gust MEES
|
Über eine gravierende Sicherheitslücke in alten Versionen des CMS Typo3 kann sich jeder authentifizieren, der nur den Namen eines registrierten Benutzers kennt. Es gibt Updates und einen Patch.

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Die Geheimdienste der USA und Großbritanniens können offenbar die SIM-Karten in Mobiltelefonen entschlüsseln. Das berichtet die Internetseite "The Intercept". Handys seien somit unauffällig anzapfbar. Der Bericht bezieht sich auf ein Snowden-Papier.
===> Der gläserne Surfer!!! <===
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=SIM-Cards

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Last week, user Virgil Griffith went onto the Tor-talk mailing list and announced Onion City, a Dark Web search engine that allows regular web users to delve into the Dark Web.
The search engine delves into the anonymous Tor network, finds .onion sites and makes them available to regular users on the ordinary World Wide Web.
Up to now the best way to search for .onion sites has been to get on the Tor network using something like the Tor browser, but Onion City effectively does that bit for you so you can search from the comfort of your favourite, insecure web browser.
|

|
Scooped by
Gust MEES
|
Early Monday morning, the websites for about 800 US schools and school districts were hijacked and replaced with an image of Saddam Hussein on a black background, a recruitment video in Arabic and the statement “I Love Islamic State” in English, according Jim Brogan, director of technology services for schools in Gloucester County, Virginia.
This should all ring a bell, given that hackers going by the same name have been more or less making the same defacements for years. Namely, a photo of Hussein accompanied by an Arabic message seen on an IS flag that reportedly reads “There is no god but Allah” and “Mohammed is the Messenger of God.”
According to the International Business Times, the web hosting company that services the sites – SchoolDesk, in Atlanta – confirmed the attack and said that a group going by the name “Team System DZ” claimed responsibility.
SchoolDesk’s statement:
Our technical staff discovered that a small file had been injected into the root of one of the SchoolDesk websites, redirecting approximately 800 school and district websites to an iFramed YouTube page containing an audible Arabic message, unknown writing and a picture of Saddam Hussein. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=US

|
Scooped by
Gust MEES
|
University of Washington researchers mount cyberattacks on surgical robot, exposing vulnerabilities.
Security vulnerabilities in surgical robots have been exposed by researchers, who hacked next generation systems to prove that they could be hijacked remotely. Researchers from the University of Washington (UW) carried out a series of cyberattacks on teleoperated (remotely operated) surgical robots using non-private networks. Various attack techniques were utilised, including a denial-of-service (DoS) attack that overloaded the robot with useless data and made it difficult to operate. A "man in the middle" attack succeeded in altering the commands sent from the operator to the robot, disrupting a wide range of the machine's functions.

|
Scooped by
Gust MEES
|
Ein US-Berufungsgericht hat entschieden, dass die Überwachung aller US-Telefonate nicht durch den dafür herangezogenen Patriot Act legitimiert ist. Wie sich die Entscheidung auf die derzeit verhandelte Verlängerung des Patriot Act auswirkt, ist unklar.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=NSA

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
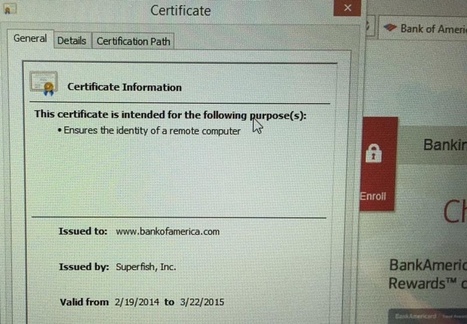
Lenovo simply can't catch a break. After the massive negative attention it received for their ill-advised decision to ship some of its notebooks with pre-installed adware that also uses MITM SSL certificates, for a short time on Wednesday their main domain - Lenovo.com - has been hijacked and effectively defaced by the hacker collective Lizard Squad.
The defaced page showed a slideshow of photos of two youngsters - according to Brian Krebs, they are Ryan King (aka “Starfall”) and Rory Andrew Godfrey (“KMS”), two former members of the hacker collective Hack The Planet - accompanied with music. The reason for the defacement is purportedly Lenovo's Superfish blunder.
The defaced page pointed to Lizard Squad's Twitter feed and served as an advertisement for its LizardStresser DoS service.
The hackers didn't compromise Lenovo's servers. Instead, they (apparently) compromised those of Web Commerce Communications (Webnic.cc), a popular Malaysia-based Internet registrar with whom the Lenovo domain is registered.
Learn more:
- http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=LENOVO
- http://www.scoop.it/t/securite-pc-et-internet/?tag=LENOVO

|
Scooped by
Gust MEES
|
This report was prepared by INSS and CSFI to create better cyber situational awareness of the nature and scope of threats to national security worldwide in the domains of cyberspace and open source intelligence. It is provided to Federal, State, Local, Tribal, Territorial and private sector officials to aid in the identification and development of appropriate actions, priorities and follow-up measures.

|
Scooped by
Gust MEES
|
Symantec Intelligence Report January 2015 [pdf] | CyberSecurity

|
Scooped by
Gust MEES
|
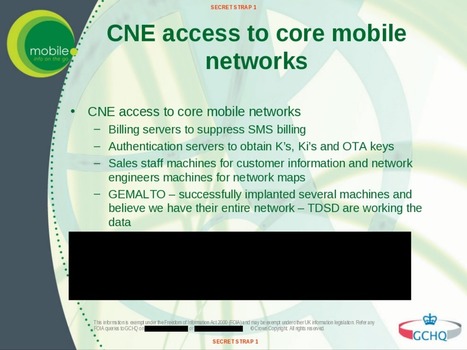
CyberespionageIn einem der folgenreichsten Hacks der IT-Geschichte verschafften sich amerikanischer und britischer Geheimdienst Zugang zum größten Handy-SIM-Karten-Hersteller der Welt und klauten dort die Verschlüsselungskeys, mit denen nahezu jede SIM weltweit gesichert ist. Damit haben NSA und GCHQ seit 2010 Zugriff auf Telefonate, SMS und mobile Internet-Verbindungen.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=SIM-Cards

|
Scooped by
Gust MEES
|
Seit Jahren kopieren NSA und GCHQ bei den Herstellern von SIM-Karten und Smart Cards die zugehörigen Schlüssel ab. Damit können sie die übertragenen Informationen mitlesen und manipulieren. Auch die Rechnungssysteme vieler Mobilfunker sind unterwandert.
Der britische Geheimdienst GCHQ und die US-amerikanische NSA haben schon vor Jahren die Sicherheitsvorkehrungen der Chiphersteller ausgehebelt. Also sind SIM-Karten, elektronische Reisepässe, Kredit- und Debitkarten, elektronische Türöffner, TAN-Generatoren und so weiter unsicher. Den darin verbauten Chips und den mit ihnen fix verbundenen Schlüsseln kann nicht mehr vertraut werden. Die Dienste können beispielsweise mobile Übertragungen einfach mitlesen oder rückwirkend entschlüsseln. Und es ist schlimmer.
SIM Cards Have Finally Been Hacked, And The Flaw Could Affect Millions Of Phones
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=SIM-Cards

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
|



 Your new post is loading...
Your new post is loading...




























Another day, another Linux community with malware woes.
Last time it was Gentoo, a hard-core, source-based Linux distribution that is popular with techies who like to spend hours tweaking their entire operating sytem and rebuilding all their software from scratch to wring a few percentage points of performance out of it.
That sort of thing isn’t for everyone, but it’s harmless fun and it does give you loads of insight into how everything fits together.
That sets it apart from distros such as ElementaryOS and Mint, which rival and even exceed Windows and macOS for ease of installation and use, but don’t leave you with much of a sense of how it all actually works.
This time, the malware poisoning happened to Arch Linux, another distro we’d characterise as hard-core, though very much more widely used than Gentoo.
Three downloadable software packages in the AUR, short for Arch User Respository, were found to have been rebuilt so they contained what you might (perhaps slightly unkindly) refer to as zombie downloader robot overlord malware.
Bots or zombies are malware programs that call home to fetch instructions from the crooks on what to do next.
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/t/securite-pc-et-internet/?&tag=Linux