 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
|
Data breaches are always bad news, and this one is peculiarly bad.
Gentoo, a popular distribution of Linux, has had its GitHub repository hacked.
Hacked, as in “totally pwned”, taken over, and modified; so far, no one seems to be sure quite how or why.
That’s the bad news.
Fortunately (we like to find silver linings here at Naked Security):
The Gentoo team didn’t beat around the bush, and quickly published an unequivocal statement about the breach.
The Gentoo GitHub repository is only a secondary copy of the main Gentoo source code.
The main Gentoo repository is intact.
All changes in the main Gentoo repository are digitally signed and can therefore be verified.
As far as we know, the main Gentoo signing key is safe, so the digital signatures are reliable.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Linux

|
Scooped by
Gust MEES
|
A new form of cryptocurrency mining malware uses a leaked NSA-exploit to spread itself to vulnerable Windows machines, while also disabling security software and leaving the infected computer open to future attacks.
The Python-based malicious Monero miner has been uncovered by researchers at security company Fortinet who've dubbed it PyRoMine. It first appeared this month and spreads using EternalRomance, a leaked NSA-exploit which takes advantage of what until a year ago had been an undisclosed SMB vulnerability to self-propagate through networks.
EternalRomance helped spread BadRabbit ransomware and is similar in many ways to EternalBlue, a second leaked NSA exploit which helped fuel WannaCry and NotPetya. Both exploits look for public-facing SMB ports, allowing them to deliver malware to networks.
Researchers discovered the malware was downloadable from a particular web address as a zip file, bundled with Pyinstaller, a program which packages programs written in Python into stand alone executables, meaning there's no need for Python to be installed on the compromised machine.
The malicious code behind PyRoMine appears to have been directly copied from a publicly shared EternalRomance implementation. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency

|
Scooped by
Gust MEES
|
Around 20% of today's top VPN solutions are leaking the customer's IP address via a WebRTC bug known since January 2015, and which apparently some VPN providers have never heard of.
The discovery belongs to Paolo Stagno, a security researcher who goes by the pseudonym of VoidSec, and who recently audited 83 VPN apps on this old WebRTC IP leak.
Stagno says he found that 17 VPN clients were leaking the user's IP address while surfing the web via a browser.
The researcher published his results in a Google Docs spreadsheet. The audit list is incomplete because Stagno didn't have the financial resources to test all commercial VPN clients.
The researcher is now asking the community to test their own VPN clients and send him the results. For this, he set up a demo web page that users must access in their browser with their VPN client enabled. The code running on this page is also available on GitHub, if users want to test the leak locally, without exposing their IP on somebody else's server.
WebRTC leak known since 2015
Stagno's code is based on the WebRTC bug discovered in January 2015 by security researcher Daniel Roesler. Back then, Roesler found that WebRTC STUN servers, which intermediate WebRTC connections, will keep records of the user's public IP address, along with his private IP address, if the client is behind-NAT network, proxy, or VPN client.
The problem was that STUN servers would disclose this information to websites that had already negotiated an WebRTC connection with a user's browser.
Since then, many advertisers and law enforcement agencies have used this WebRTC-related bug to acquire a site's visitor's IP address. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=VPN

|
Scooped by
Gust MEES
|
The average home now has around three connected computers and four smart mobile devices. Hardly surprising, considering that 86 per cent of us check the Internet several times a day or more, and that’s outside of work. Chatting, shopping, banking, playing games, listening to music, booking travel and managing our increasingly connected homes. The risk of cyberattack can be the furthest thing from our mind. Every year, Kaspersky Lab’s experts look at the main cyberthreats facing connected businesses over the coming 12 months, based on the trends seen during the year. For 2018, we decided to extract some top predictions that also have big implications for everyday connected life. So what could the hackers be after in 2018? Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet

|
Scooped by
Gust MEES
|
Hundreds of websites record your scrolling behavior, clicks and movements according to a study recently carried out at Princeton University. Among these are The Guardian, Reuters, Samsung, AlJazeera and WordPress.com.
Most of us are aware that our searches, page views and even page scrolls are documented, but the report sheds light on how intricate that tracking can be. Using something called “session replays,” they record keystrokes and movements a user makes while they navigate a page — basically “looking over your shoulder,” but virtually.
The study, carried out by Princeton’s Center for Information Technology Policy, focused on some of the main companies that offer session replay services: SessionCam, UserReplay, FullStory, Clicktale, Yandex, Smartlook, and Hotjar.
It’s important to understand why this is dangerous — apart from straight-up invading your privacy. The report pointed out that most of these services directly exclude password input fields from recordings, but a lot of the time mobile-friendly forms are not redacted on the recordings, and end up revealing sensitive information, including passwords, credit card numbers, and even credit card security codes.
The report explains, “All of the companies studied offer some mitigation through automated redaction, but the coverage offered varies greatly by provider. UserReplay and SessionCam replace all user input with an equivalent length masking text, while FullStory, Hotjar, and Smartlook exclude specific input fields by type.”
This kind of information is usually shared when a user is signing up for a service or making a payment, and is expected to be completely confidential. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Session-Replay+Scripts https://www.scoop.it/t/securite-pc-et-internet/?&tag=Cyberespionage https://www.scoop.it/t/securite-pc-et-internet/?&tag=Privacy https://gustmees.wordpress.com/2013/12/21/privacy-in-the-digital-world-shouldnt-we-talk-about-it/

|
Scooped by
Gust MEES
|
The account details of millions of subscribers to the education platform Edmodo have not only been stolen but witnessed to be for sale on the dark web, according to a post on Motherboard. The platform is used by more than 78 million teachers, students and parents to compose lesson plans, make homework assignments and other tasks.
Breach notification website LeakBase provided Motherboard with a sample of more than two million records, which included usernames, email addresses and hashed passwords.
The good news is that the passwords apparently are hashed with the stealthy bcrypt algorithm, and a string of random characters known as a salt, which likely will make it more difficult for hackers to obtain users' login credentials. And, when staffers at Motherboard attempted to open Edmodo accounts using some of the purloined data, they were unsuccessful as the address was already linked to an Edmodo account, the report explained.
The bad news is that at least a portion of the database is up for sale on the dark web marketplace Hansa for $1,000. The seller, going under the name nclay, said s/he was in possession of 77 million accounts. LeakBase reported that 40 million of those come with an email address.
Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=DATA-BREACHES http://www.scoop.it/t/securite-pc-et-internet/?&tag=Edmodo+Insecurity

|
Scooped by
Gust MEES
|
Ever felt like you were being watched online? You know, like when you read something about New York, and the next site you visit shows you ads for New York hotels? As it turns out, on my computer, there were more than 130 companies tracking my every move (check yours here, then install this plug-in).
These companies are basically engaging in mass surveillance. Just as governments justify tracking us to prevent terrorist attacks, these companies are tracking us online, without our consent, because a marginal 0.7 percent of the population clicks on their ads.
And it’s not just online advertisers. From e-commerce websites to physical retail stores, everyone is now racing to capture more data about us. Don’t be surprised if your insurance company starts charging you more because of how it thinks you should live your life!
Don’t get me wrong, I use Facebook, Google and all those other services. I use them because I find them useful, fun or because I don’t have an alternative. But I do it knowing very well that I am partly giving away my right to privacy. Learn more / En savoir plus / Mehr erfahren: https://gustmees.wordpress.com/2013/12/21/privacy-in-the-digital-world-shouldnt-we-talk-about-it/

|
Scooped by
Gust MEES
|
Anybody who walks or drives past new tracking billboards with a mobile phone in their pocket can be spied on without their knowledge or consent: a potential invasion of privacy that US Senator Charles E. Schumer wants the US Federal Trace Commission (FTC) to investigate.
Schumer, a Democrat from New York, delivered a briefing in Times Square on Sunday, electronic billboards blinking and scrolling behind him.
From his remarks:
A person’s cell phone should not become a James Bond-like personal tracking device for a corporation to gather information about consumers without their consent.
No one wants to be followed or tracked throughout their day, electronically or otherwise.
These new “spying” billboards raise serious questions about privacy, Schumer said. They should be investigated by the feds, and the companies behind them should be required to offer an opt-out option for consumers who feel that they violate their privacy. Learn more / En savoir plus / Mehr erfahren: https://gustmees.wordpress.com/2013/12/21/privacy-in-the-digital-world-shouldnt-we-talk-about-it/ https://gustmees.wordpress.com/2014/03/05/often-asked-questions-are-there-cyber-security-dangers-with-apps-and-whats-about-privacy/

|
Scooped by
Gust MEES
|
Yup, I get it: The cloud computing train has left the station and there’s no stopping it now, but it certainly won’t reach Eurostar speeds if there aren’t enough cybersecurity professionals with the right cloud computing knowledge to support this transition.
Given this imbalance, what can CISOs do to support cloud computing business initiatives AND mitigate risk appropriately? Learn more /En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?tag=Cloud-Security

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
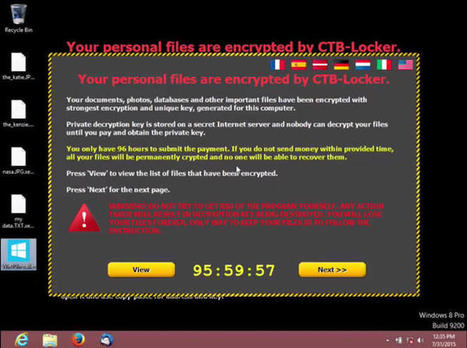
Just days after Microsoft released its latest operating system, hackers have begun targeting soon-to-be Windows 10 users with an emerging kind of malware.
Cisco security researchers are warning users against opening email attachments purporting to be from the software giant. The "ransomware" malware, which encrypts files until a ransom is paid, is being sent as part of an email spam campaign.
Stop trying to control everything. Learners know best.
The learners know more than you do about what learning experiences are right for them. I don’t think we should necessarily build our own versions of YouTube, Pinterest, Twitter etc either, we just need to be the champions of these tools for learning. In someways, L&D’s job should be much easier than we’re making it and in other ways, with the entrenched spoon-feeding learners have come to expect from corporate training, it’s much harder then it seems. What I’d hope you take away from this post is that there is a new way, and it’s your job (if you work in learning) to explain this to decision-makers who don’t know any better. . Learn more: . .
Via juandoming
|

|
Scooped by
Gust MEES
|
Over a million fiber routers can be remotely accessed, thanks to an authentication bypass bug that's easily exploited by modifying the URL in the browser's address bar.
The bug lets anyone bypass the router's login page and access pages within -- simply by adding "?images/" to the end of the web address on any of the router's configuration pages, giving an attacker near complete access to the router. Because the ping and traceroute commands on the device's diagnostic page are running at "root" level, other commands can be remotely run on the device, too.
The findings, published Monday, say the bug is found in routers used for fiber connections. These routers are central in bringing high-speed fiber internet to people's homes.
At the time of writing, about 1.06 million routers marked were listed on Shodan, the search engine for unprotected devices and databases. Half the vulnerable routers are located on the Telmex network in Mexico, and the rest are found on in Kazakhstan and Vietnam. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Router

|
Scooped by
Gust MEES
|
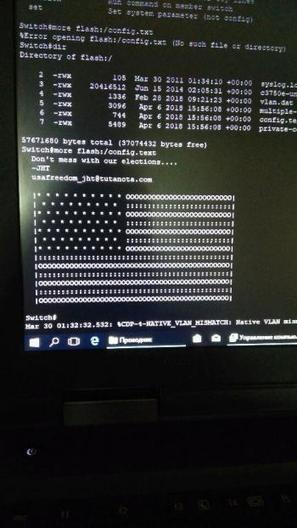
Unbekannte haben eine Sicherheitslücke in Cisco-Routern ausgenutzt und auf Systemen in Russland und Iran eine politische Botschaft hinterlassen. In westlichen Ländern hingegen schlossen sie die Lücke - behauptet zumindest eine anonyme E-Mail.
Hacker mit Sympathie für die USA nehmen für sich in Anspruch, am vergangenen Freitag zahlreiche Computersysteme in Russland und dem Iran über eine Sicherheitslücke gekapert und eine Abbildung der amerikanischen Flagge hinterlassen zu haben – zusammen mit dem Warnhinweis: "Don't mess with our elections..." (zu deutsch etwa: Mischt euch nicht in unsere Wahlen ein). Das meldet das Online-Magazin Motherboard.
"Don't mess with our elections..." Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Cyberattacks

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Luxembourg, a tiny country with ONLY 590.667 inhabitants (January 2017) in the heart of Europe and one of the smallest countries in the world, WHERE MOST persons don’t even know where to find it on the map, shows up as an international country well known and recognized for its Cyber Security knowledge, as well as its skills in ICT. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/luxembourg-europe/?tag=Digital+L%C3%ABtzebuerg

|
Scooped by
Gust MEES
|
Twitter’s been combatting harassment for years. The latest effort: quelling its horde of anonymous, hostile egg accounts. But for many users, Twitter’s abuse problem has long since undermined its value as a platform for creative communication. That’s what makes Mastodon—a free, open-source, and increasingly popular six-month-old Twitter alternative—so intriguing.
Mastodon has created a diverse yet welcoming online environment by doing exactly what Twitter won’t: letting its community make the rules. The platform consists of various user-created networks, called instances, each of which determines its own laws. One instance could ban sexist jokes and Nazi logos, while another might practice radically free speech. (In this way, Mastodon is not unlike a network of discretely moderated message boards crossed with a Tweetdeck-like interface.) Users choose for themselves which instance they want to join and select from a host of privacy and anti-harassment settings. Oh, and the character limit is 500, not 140. In essence, Mastodon is an experiment in whether individually moderated communities can make a social network like Twitter more civil. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/social-media-and-its-influence/?&tag=Mastodon

|
Scooped by
Gust MEES
|
Who Will Own Your Data If the Tech Bubble Bursts?
Corporations, data brokers, and even criminals might buy failed companies just for their users’ personal information. Desperate companies will resort, if they can, to selling the detailed data they’ve meticulously collected about their users—whether it’s personally identifiable information, data about preferences, habits, and hobbies, or national-security files. That data, formerly walled-off and spoon-fed only to paying advertisers, would be attractive to both licit and criminal buyers. Easily searchable datasets could generate new innovations and investments—but it would be difficult to know who’s buying up sensitive datasets, and why. If contracts and privacy policies prevent a floundering company from selling user data, there’s still another way to profit. Most privacy policies that promise not to sell user data include a caveat in case of bankruptcy or sale. In fact, a New York Times analysis of the top 100 websites in the U.S. last year found that 85 of them include clauses in their privacy policies like this one from Facebook: If the ownership or control of all or part of our Services or their assets changes, we may transfer your information to the new owner.
Learn more / En savoir plus / Mehr erfahren: https://gustmees.wordpress.com/2013/12/21/privacy-in-the-digital-world-shouldnt-we-talk-about-it/

|
Scooped by
Gust MEES
|
Password Day is a day for "taking our passwords to the next level" - here are five traditions the crooks really don't want us to start.

|
Scooped by
Gust MEES
|
Intel has fixed a major security vulnerability in a driver utility tool that could allow an attacker to remotely install malware.
The company has advised those who use the Intel Driver Update Utility to download an updated version of the software, which mitigates a vulnerability in how the software requests new drivers from Intel's servers.
In a security advisory, the chipmaker confirmed that versions 2.0 to 2.3 put PCs at risk because they check Intel's servers over an unencrypted connection. An attacker could conduct a man-in-the-middle on the affected software. which could trick the software into downloading malware or other malicious files.

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
What about malware on Linux?
Here's how the argument might go if you were to ask that question:
Malware is impossible on Linux because Linux is secure by design, unlike Windows.
Even if Linux malware were possible, users would have to agree to run it, so that wouldn't count.
Even if users agreed to run it, they wouldn't be root, so that wouldn't count.
Even if they were root, who cares? There isn't any malware for Linux, so there.
The simple truth, of course, is that Linux is much more similar to Windows – in design, implementation and real-world security – than it is different.
As a result: there is malware for Linux; it can do plenty of harm even if you aren't root; and it may be able to infect without you realising.
Just like on Windows.
For all that, the "malware scene" on Linux simply never unfolded like it did on Windows, because the vast
Learn more:
http://www.scoop.it/t/securite-pc-et-internet/?tag=Linux

|
Scooped by
Gust MEES
|
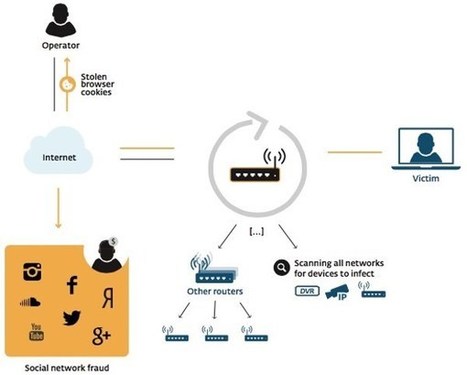
ESET researchers have issued a technical paper today, analysing a new worm that is infecting routers in order to commit social networking fraud, hijacking victims’ internet connections in order to “like” posts and pages, “view” videos and “follow” other accounts.
The malware, dubbed Linux/Moose by researchers Olivier Bilodeau and Thomas Dupuy, infects Linux-based routers and other Linux-based devices, eradicating existing malware infections it might find competing for the router’s limited resources, and automatically finding other routers to infect.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Router
|



 Your new post is loading...
Your new post is loading...


























Data breaches are always bad news, and this one is peculiarly bad.
Gentoo, a popular distribution of Linux, has had its GitHub repository hacked.
Hacked, as in “totally pwned”, taken over, and modified; so far, no one seems to be sure quite how or why.
That’s the bad news.
Fortunately (we like to find silver linings here at Naked Security):
The Gentoo team didn’t beat around the bush, and quickly published an unequivocal statement about the breach.
The Gentoo GitHub repository is only a secondary copy of the main Gentoo source code.
The main Gentoo repository is intact.
All changes in the main Gentoo repository are digitally signed and can therefore be verified.
As far as we know, the main Gentoo signing key is safe, so the digital signatures are reliable.
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/t/securite-pc-et-internet/?&tag=Linux