Mit dem Schweizer Verschlüsselungs-Token IndependenceKey lassen sich ganze Festplatten chiffrieren - und das ohne Hintertüren. Sogar sichere VoIP-Gespräche sollen damit möglich sein.
Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/securite-pc-et-internet/?tag=Cryptography
http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=Cryptography



 Your new post is loading...
Your new post is loading...





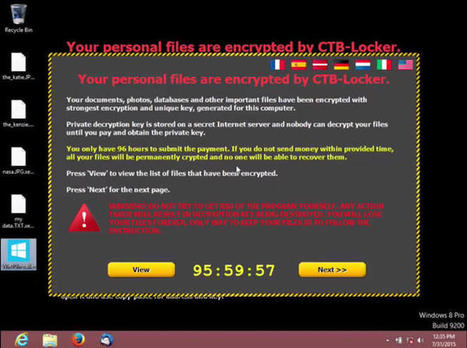









Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/securite-pc-et-internet/?tag=Cryptography
http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=Cryptography