Symantec has warned of a new attack campaign targeting energy firms, which may have already given the hackers access to operational systems in the US and Europe.
The security giant claimed the Dragonfly threat group is behind the new round of attacks, ongoing since December 2015.
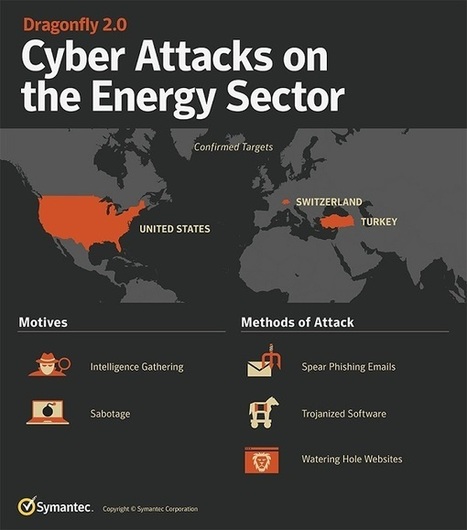
Organizations in the US, Turkey and Switzerland were identified as targets for a range of tools and techniques including malicious emails, watering hole attacks and trojanized software.
Emails with content specific to the energy sector were designed to socially engineer the recipients into opening a malicious attachment. If opened, they would steal the victims' network credentials.
Watering hole attacks were also used to harvest credentials, with the hackers booby-trapping sites likely to be visited by energy sector workers.
The stolen credentials were then typically used in follow-on attacks designed to install backdoors to provide remote access and give the hackers the option of installing additional tools.
Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/securite-pc-et-internet/?&tag=GRID
http://www.scoop.it/t/securite-pc-et-internet/?&tag=Dragonfly



 Your new post is loading...
Your new post is loading...










Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/securite-pc-et-internet/?&tag=GRID
http://www.scoop.it/t/securite-pc-et-internet/?&tag=Dragonfly