 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
|
What could be more horrifying than knowing that a hacker can trick the plane's electronic systems into displaying false flight data to the pilot, which could eventually result in loss of control?
Of course, the attacker would never wish to be on the same flight, so in this article, we are going to talk about a potential loophole that could allow an attacker to exploit a vulnerability with some level of "unsupervised" physical access to a small aircraft before the plane takes off.
The United States Department of Homeland Security's (DHS) has issued an alert for the same, warning owners of small aircraft to be on guard against a vulnerability that could enable attackers to easily hack the plane's CAN bus and take control of key navigation systems.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Airlines

|
Scooped by
Gust MEES
|
MyHeritage, an Israeli DNA, and genealogy website has suffered a massive data breach in which email accounts and hashed passwords of 92 million users (92,283,889) who signed up to the service up to October 26, 2017, have been stolen.
The compromised MyHeritage data was discovered by a security researcher on a private server outside of MyHeritage and reported the incident to the company who after an in-depth analysis acknowledged the breach and published an official statement on June 4, 2018. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Cyber-Attacks

|
Scooped by
Gust MEES
|
Vulnerable in-vehicle infotainment systems have left some Volkswagen cars open to remote hacking, researchers warn. Over the last few years, automakers like Ford, Jeep, Nissan and Toyota have all suffered car-hacking vulnerabilities in their vehicles. Now, it looks like Volkswagen has been pulled into the mix after researchers discovered that in-vehicle infotainment (IVI) systems in certain Volkswagen-manufactured cars could be remotely hacked. Not only that, but it’s possible to pivot to more critical systems. Related PostsApril 25, 2018 , 11:30 am April 25, 2018 , 9:30 am April 19, 2018 , 1:17 pm The vulnerability was discovered in the Volkswagen Golf GTE and an Audi3 Sportback e-tron, which were both manufactured in 2015. Computest researchers Daan Keuper and Thijs Alkemade, who discovered the flaw, said that under certain conditions the IVI vulnerability could enable attackers to commandeer the on-board microphone to listen in on the conversations of the driver, turn the microphone on and off, and access the system’s complete address book and the conversation history. There is also a possibility of hackers tracking the car through the navigation system at any given time, they said. A Volkswagen spokesperson told Threatpost that the vehicles impacted are those produced with Discover Pro infotainment systems – Golf GTE and Audi A3 e-tron. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Cars https://www.scoop.it/t/securite-pc-et-internet/?&tag=iot

|
Scooped by
Gust MEES
|
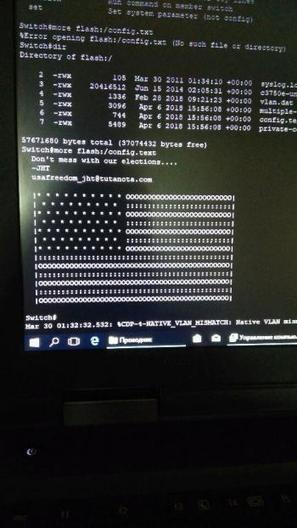
Unbekannte haben eine Sicherheitslücke in Cisco-Routern ausgenutzt und auf Systemen in Russland und Iran eine politische Botschaft hinterlassen. In westlichen Ländern hingegen schlossen sie die Lücke - behauptet zumindest eine anonyme E-Mail.
Hacker mit Sympathie für die USA nehmen für sich in Anspruch, am vergangenen Freitag zahlreiche Computersysteme in Russland und dem Iran über eine Sicherheitslücke gekapert und eine Abbildung der amerikanischen Flagge hinterlassen zu haben – zusammen mit dem Warnhinweis: "Don't mess with our elections..." (zu deutsch etwa: Mischt euch nicht in unsere Wahlen ein). Das meldet das Online-Magazin Motherboard.
"Don't mess with our elections..." Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Cyberattacks

|
Scooped by
Gust MEES
|
BUNDESHACK:
Hack auf Bundesregierung erfolgte über Lernplattform Ilias
Die Bundesregierung wurde über die Lernplattform Ilias gehackt, die an der Hochschule des Bundes zu Weiterbildungszwecken genutzt wird. Die Einrichtung nutzte eine alte Version mit zahlreichen Sicherheitslücken.
Eine Exklusivmeldung von Hauke Gierow und Hanno Böck
Unter lernplattform-bakoev.bund.de können Mitarbeiter des Bundes Weiterbildungsangebote der Bundesakademie für Öffentliche Verwaltung wahrnehmen - eigentlich. Denn die von der Hochschule des Bundes betriebene Webseite ist derzeit nicht erreichbar. Wer sie besuchen will, bekommt nur die Fehlermeldung: "Die Lernplattform Ilias ist zurzeit nicht erreichbar. Sie wurde auf Empfehlung des BSI vorsorglich vom Netz genommen." Über diese Plattform soll der Hack auf die Bundesregierung abgelaufen sein. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Cyberattacks

|
Scooped by
Gust MEES
|
Hackers -- possibly Russian -- have reportedly had access to the German government's secure network for over a year.
As first revealed by German news agency DPA, the hackers were able to steal data in the intrusion, which was apparently spotted in December.
The report quoted unnamed sources as saying the chief suspect is the notorious APT28 or Fancy Bear group, which was reportedly behind the German parliament's big 2015 hacking and, months later, the Democratic National Committee (DNC) compromise in the US.
Fancy Bear is widely believed to be under the Kremlin's control. Apart from the Bundestag and DNC, its targets have included everyone from the Ukrainian military and US defense contractors, to Russian opposition parliamentarians and the Putin-critical punk group Pussy Riot.
The group's previous German hack involved the Bundestag's regular network. This time it's the secure Berlin-Bonn Information Network (IVBB), an intranet run by the Interior Ministry that comes with higher usage restrictions for users and is supposed to be firewalled to the gills. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Cyberattacks

|
Scooped by
Gust MEES
|
Over the weekend, officials from the Winter Olympics taking place in South Korea confirmed a cyberattack hit systems helping run the event during the opening ceremony. They didn't provide much detail, though the attack coincided with 12 hours of downtime on the official website, the collapse of Wi-Fi in the Pyeonchang Olympic stadium and the failure of televisions and internet in media rooms, according to reports.
Researchers from Cisco's Talos cybersecurity unit now believe with "moderate" confidence they've found the malware responsible. They've suitably named it Olympic Destroyer, for its main focus is taking down systems and wiping data, rather than stealing information. More specifically, it deletes files and their copies, as well as event logs, whilst using legitimate features on Windows computers to move around targeted networks.
For the latter, the malware tries to use PsExec and Windows Management Instrumentation, both used by network administrators to access and carry out actions on other users' PCs. Both were used by the NotPetya ransomware in 2017. Whilst no one has attributed the Olympics attacks, Ukraine blamed Russia for NotPetya and suspicions the latter would target the event via digital means have been rife. Russia, meanwhile, has told media it was not responsible.
"We know that Western media are planning pseudo-investigations on the theme of 'Russian fingerprints' in hacking attacks on information resources related to the hosting of the Winter Olympic Games in the Republic of Korea," the foreign ministry said, according to the BBC. "Of course, no evidence will be presented to the world." Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Das Risiko von Cyber-Angriffen auf wichtige Infrastruktur-Einrichtungen wird nach Ansicht von Vertretern sowohl aus Politik als auch aus der Wirtschaft immer realistischer. Insgesamt drei Viertel der Befragten einer Trendstudie sehen eine große Gefahr durch Angriffe etwa auf das Stromnetz oder auf Krankenhäuser. Das ergab eine Untersuchung, die das Beratungshaus Deloitte am Donnerstag gemeinsam mit dem Allensbach-Institut in Berlin vorstellte.
Im vergangenen Jahr stuften demnach nur 27 Prozent der Entscheider einen Zusammenbruch des Stromnetzes als großes Risiko für die Menschen ein. "Die Digitalisierung bringt unzählige und unschätzbare Vorteile, aber sie macht auch verwundbar", sagte Peter Wirnsperger, Partner von Deloitte. Die Akteure schätzten die Situation jedoch überwiegend realistisch ein. "Die Digitalisierung steht bei unseren CEOs ganz oben auf der Agenda." Viele hätten große Erwartungen an die Politik, doch eine Seite allein könne "diesem Sturm nicht widerstehen". Ziel sei es, mit dem aktuellen Report die Diskussion zu befeuern.
Große Gefahr durch den Diebstahl privater Daten
Ebenfalls als großes Risiko wird der Missbrauch persönlicher Daten gewertet. Demnach gaben jeweils zwei Drittel der Befragten an, eine große Gefahr durch Diebstahl privater Daten, Datenbetrug im Internet oder missbräuchliche Nutzung eigener Daten in sozialen Netzwerken zu sehen. Bemerkenswerterweise habe eine hohe Risiko-Einschätzung jedoch keine Auswirkungen auf das eigene konkrete Verhalten, sagte Renate Köcher vom Allensbach Institut.
Nur eine kleine Minderheit der Entscheider aus Politik und Wirtschaft sei überzeugt, dass Deutschland so gut wie möglich auf Cyber-Angriffe vorbereitet sei, sagte Köcher. Demnach glauben fast zwei Drittel der Politiker und knapp drei Viertel der Führungskräfte nicht, dass der aktuelle Status Quo ausreiche.
Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet

|
Scooped by
Gust MEES
|
Symantec has warned of a new attack campaign targeting energy firms, which may have already given the hackers access to operational systems in the US and Europe.
The security giant claimed the Dragonfly threat group is behind the new round of attacks, ongoing since December 2015.
Organizations in the US, Turkey and Switzerland were identified as targets for a range of tools and techniques including malicious emails, watering hole attacks and trojanized software.
Emails with content specific to the energy sector were designed to socially engineer the recipients into opening a malicious attachment. If opened, they would steal the victims' network credentials.
Watering hole attacks were also used to harvest credentials, with the hackers booby-trapping sites likely to be visited by energy sector workers.
The stolen credentials were then typically used in follow-on attacks designed to install backdoors to provide remote access and give the hackers the option of installing additional tools. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=GRID http://www.scoop.it/t/securite-pc-et-internet/?&tag=Dragonfly

|
Scooped by
Gust MEES
|
Einer aktuellen Bitkom-Studie zufolge sind nur vier von zehn Unternehmen auf Cyberangriffe vorbereitet. Gerade kleinere Unternehmen haben nicht mal einen Notfallplan für Sicherheitsvorfälle. Auch Betreiber kritischer Infrastrukturen seien kaum besser gerüstet, so der Digitalverband. Learn more / En savoir plus / Mehr erfahren: https://www.cases.lu/de/homede.html

|
Scooped by
Gust MEES
|
Unidentified hackers have been targeting the networks of companies responsible for operating nuclear power plants in the US for the last two months, according to The New York Times. Citing a joint report issued by both the Department of Homeland Security and the FBI some time last week, The Times’ story identifies one target as the Wolf Creek Nuclear Operating Corporation, a facility responsible for overseeing the operation of a nuclear power plant outside Burlington, Kansas. The report also states that energy companies and manufacturing plants are also being targeted, yet none are identified by name. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=Cyberattacks

|
Scooped by
Gust MEES
|
In einem NSA-Bericht werden russische Militärhacker beschuldigt, vor den US-Wahlen dortige Wahlbehörden und deren Lieferanten angegriffen zu haben. Der streng geheime Bericht wurde dem Internetmagazin The Intercept zugespielt und hat bereits Konsequenzen.
Das Wappen des russischen Militärgeheimdienstes GRU Hacker des Militärnachrichtendienstes der Russischen Föderation (GRU) sollen vor den US-Wahlen vom November 2016 zumindest versucht haben, in die Systeme von US-Wahlbehörden und Dienstleistern einzudringen. Das geht aus einem geheimen Bericht der NSA hervor, der von The Intercept veröffentlicht wurde. Er dreht sich in erster Linie um einen mehrstufigen Spearphishing-Angriff, hält sich bei der Beurteilung eines etwaigen Erfolgs aber bedeckt.
Das Dokument ist als "Top Secret" gekennzeichnet und wurde offenbar in der ersten Maiwoche erstellt. Es enthält eine Zusammenfassung von Ermittlungsergebnissen, aber keine Rohdaten. Offen bleibt, auf welcher Grundlage der GRU beschuldigt wird. Berichtet wird über drei verschiedene, dem GRU zugeschriebene Anläufe im Zeitraum von August bis November 2016. Von dem schwerwiegendsten der drei Fälle hat die NSA laut ihrem Bericht erst am 27. April erfahren. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=NSA
|

|
Scooped by
Gust MEES
|
Artificial intelligence has the potential to bring a select set of advanced techniques to the table when it comes to cyber offense, researchers say.
On Thursday, researchers from Darktrace (.PDF) said that the current threat landscape is full of everything from script kiddies and opportunistic attacks to advanced, state-sponsored assaults, and in the latter sense, attacks continue to evolve.
However, for each sophisticated attack currently in use, there is the potential for further development through the future use of AI.
Within the report, the cybersecurity firm documented three active threats in the wild which have been detected within the past 12 months. Analysis of these attacks -- and a little imagination -- has led the team to create scenarios using AI which could one day become reality.
"We expect AI-driven malware to start mimicking behavior that is usually attributed to human operators by leveraging contextualization," said Max Heinemeyer, Director of Threat Hunting at Darktrace. "But we also anticipate the opposite; advanced human attacker groups utilizing AI-driven implants to improve their attacks and enable them to scale better. Learn more / En svoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=AI

|
Scooped by
Gust MEES
|
VW bugs: "Unpatchable" remote code pwnage
Two security researchers have excoriated Volkswagen Group for selling insecure cars. As in: hackable-over-the-internet insecure.
They broke into a recent-model VW and an Audi, via the cars’ internet connections, and were able to jump from system to system, running arbitrary code. Worryingly, they fully pwned the unauthenticated control bus connected to some safety-critical systems—such as the cruise control.
But VW has no way to push updates to its cars, and won’t alert owners to visit a dealer for an update.
Yes, it’s the internet of **** again: Potentially safety-critical bugs caused by the conflict between convenience and security. In this week’s Security Blogwatch, we prefer classic, analog vehicles.
Your humble blogwatcher curated these bloggy bits for your entertainment. Not to mention: Globfinity War…
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Cars https://www.scoop.it/t/securite-pc-et-internet/?&tag=iot

|
Scooped by
Gust MEES
|
Selon Threat Post, deux chercheurs en sécurité de l'entreprise hollandaise Computest, Daan Keuper et Thijs Alkemade, ont découvert des vulnérabilités dans le logiciel embarqué de la Volkswagen Golf GTE et de l'Audi3 Sportback e-tron
Ces vulnérabilités offrent pas mal d'amusements aux pirates : ouvrir le microphone pour écouter les conversation à l'intérieur du véhicule, accéder au carnet d'adresses complet, à l'historique des conversations, tracer le véhicule à travers son système de navigation, modifier l'affichage de l'écran du système..
Ce n'est pas tout... Poussant leurs investigations, les chercheurs ont constaté qu'il est possible de lire n'importe quel fichier sur le disque du système et même d'exécuter du code arbitraire à distance.
Volswagen commente l'affaire ainsi auprès de Threatpost : "Nous sommes en contact avec Computest depuis la mi-2017", la correction de bugs - en d'autres termes, l'élimination de la vulnérabilité - avait déjà eu lieu début mai 2016."
Fort bien... Toutefois en ce qui concerne les corrections des bugs, les chercheurs sont beaucoup plus nuancés : "Le système que nous avons étudié ne peut pas être mis à jour par l'utilisateur final, un utilisateur doit se rendre chez un revendeur officiel pour recevoir une mise à jour. Cependant, d'après notre expérience, il semble que les voitures qui ont été produites auparavant ne sont pas automatiquement mises à jour lorsqu'elles sont réparées chez un concessionnaire, elles sont donc toujours vulnérables à l'attaque décrite. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Cars https://www.scoop.it/t/securite-pc-et-internet/?&tag=iot

|
Scooped by
Gust MEES
|
Nation-state attackers are attempting to undermine trust in critical services -- so how do we go about stopping them?
While cyber-attacks focusing on stealing email or other data are still very much part of the threat landscape, some of the most advanced hacking operations are focusing on grander goals.
Some of these groups -- almost all nation-state backed -- are turning their attention to critical infrastructure including utilities firms and power plants, while others are attempting to manipulate public attitudes and even elections through the use of fake news and other social media propaganda.
"It's not so much an attack on critical infrastructure, but rather an attack on the confidence and psychology of a nation," said Chris Inglis, former deputy director of the National Security Agency, speaking at World Cyber Security Congress event in London.
Attacking critical infrastructure and spreading disinformation is a powerful combination: after all, the reason that governments exist is to make sure the citizens of a country remain safe. Such tactics have been tried out in Ukraine over the last few years. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Cyberattacks

|
Scooped by
Gust MEES
|
In a growing sign of the increased sophistication of both cyber attacks and defenses, GitHub has revealed that this week it weathered the largest-known DDoS attack in history.
DDoS — or distributed denial of service in full — is a cyber attack that aims to bring websites and web-based services down by bombarding them with so much traffic that their services and infrastructure are unable to handle it all. It’s a fairly common tactic used to force targets offline.
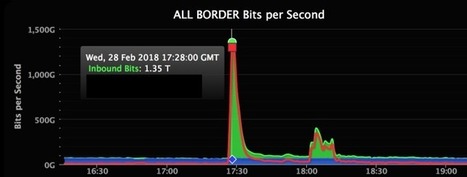
GitHub is a common target — the Chinese government was widely suspected to be behind a five-day-long attack in 2015 — and this newest assault tipped the scales at an incredible 1.35Tbps at peak.
In a blog post retelling the incident, GitHub said the attackers hijacked something called “memcaching” — a distributed memory system known for high-performance and demand — to massively amplify the traffic volumes that were being fired at GitHub. To do that, they initially spoofed GitHub’s IP address and took control of memcached instances that GitHub said are “inadvertently accessible on the public internet.”
The result was a huge influx of traffic. Wired reports that, in this instance, the memcached systems used amplified the data volumes by around 50 times. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=DDos

|
Scooped by
Gust MEES
|
GitHub has revealed it was hit with what may be the largest-ever distributed denial of service (DDoS) attack.
The first portion of the attack against the developer platform peaked at 1.35Tbps, and there was a second 400Gbps spike later. This would make it the biggest DDoS attack recorded so far. Until now, the biggest clocked in at around 1.1Tbps.
In a post on its engineering blog, the developer platform said that, on Feb. 28, GitHub.com was unavailable from 17:21 to 17:26 UTC and intermittently unavailable from 17:26 to 17:30 UTC due to the DDoS attack.
Github said that at no point "was the confidentiality or integrity of your data at risk. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Cyberattacks

|
Scooped by
Gust MEES
|
Ransomware-Attacke: 4000 Server und 45.000 PCs neu installiert
In zehn Tagen erneuerte Møller-Maersk seine gesamte IT-Infrastruktur. Die Folgekosten von Petya/NotPetya beziffert der Reederei-Konzern mit 250 bis 300 Millionen Dollar. Er strebt jetzt mehr Cybersicherheit als Wettbewerbsvorteil an.
Der Reederei-Konzern Møller-Maersk hat durch die Ransomware Petya/NotPetya einen Schaden zwischen 250 und 300 Millionen Dollar erlitten. Es gelang ihm jedoch, innerhalb von zehn Tagen 4000 Server, 45.000 PCs und 2500 Anwendungen neu zu installieren. Das berichtete auf dem Weltwirtschaftsgipfel in Davos Jim Hagemann Snabe, Chairman von Møller-Maersk.
„Stellen Sie sich ein Unternehmen vor, bei dem alle 15 Minuten ein Schiff mit 10.000 bis 20.000 Containern in einen Hafen einläuft, und Sie haben zehn Tage lang keine IT“, sagte Hagemann. „Man kann sich das fast gar nicht vorstellen.“ Der Maersk-Chef attestierte den Mitarbeitern und Partnern eine „heroische Leistung“ für die schnelle Erneuerung der IT-Infrastruktur. Der dänische Konzern hat Niederlassungen in 130 Ländern und fast 90.000 Mitarbeiter. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=RANSOMWARE https://www.scoop.it/t/securite-pc-et-internet/?&tag=Costs-of-Cybercirme

|
Scooped by
Gust MEES
|
Phishing, Trojans, Ransomware and Viruses: Hardly a day goes by without hacker attacks against companies or private individuals. This huge LUCY Infographic shows the explosion of internet crime State of Cyber Crime 2018 – Numbers in detail In the United States by Internet crime caused damage in 2001:17.8 million USD. In the United …

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Hackers who hit American utilities this summer had the power to cause blackouts, Symantec says. And yes, most signs point to Russia. IN AN ERA of hacker attacks on critical infrastructure, even a run-of-the-mill malware infection on an electric utility’s network is enough to raise alarm bells. But the latest collection of power grid penetrations went far deeper: Security firm Symantec is warning that a series of recent hacker attacks not only compromised energy companies in the US and Europe but also resulted in the intruders gaining hands-on access to power grid operations—enough control that they could have induced blackouts on American soil at will.
Symantec on Wednesday revealed a new campaign of attacks by a group it is calling Dragonfly 2.0, which it says targeted dozens of energy companies in the spring and summer of this year. In more than 20 cases, Symantec says the hackers successfully gained access to the target companies’ networks. And at a handful of US power firms and at least one company in Turkey—none of which Symantec will name—their forensic analysis found that the hackers obtained what they call operational access: control of the interfaces power company engineers use to send actual commands to equipment like circuit breakers, giving them the ability to stop the flow of electricity into US homes and businesses.
Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=GRID

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
A number of firms around the world are reporting that they have been impacted by a major cyber attack which the UK's cyber security agency is describing as a "global ransomware incident."
Many of the initial reports of organisations affected came from Ukraine, including banks, energy companies and even Kiev's main airport. But since then more incidents have been reported across Europe, indicating the incident is affecting more organisations more widely. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=RANSOMWARE http://www.scoop.it/t/securite-pc-et-internet/?&tag=Petya
|



 Your new post is loading...
Your new post is loading...




















![State of Cyber Attacks 2018 – A big Overview about Cybercrime [Infographic] - LUCY Phishing, Social Hacking and Security Awareness | #CyberSecurity | ICT Security-Sécurité PC et Internet | Scoop.it](https://img.scoop.it/dH0qjTsuLei_pVSG-kbkczl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)








What could be more horrifying than knowing that a hacker can trick the plane's electronic systems into displaying false flight data to the pilot, which could eventually result in loss of control?
Of course, the attacker would never wish to be on the same flight, so in this article, we are going to talk about a potential loophole that could allow an attacker to exploit a vulnerability with some level of "unsupervised" physical access to a small aircraft before the plane takes off.
The United States Department of Homeland Security's (DHS) has issued an alert for the same, warning owners of small aircraft to be on guard against a vulnerability that could enable attackers to easily hack the plane's CAN bus and take control of key navigation systems.
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Airlines