Google has removed 89 malicious extensions from the Chrome Web Store that have been installed on over 420,000 browsers, turning them into Monero-mining slaves and loading a tool to record and replay what their owners do on every website they visit.
Researchers at Trend Micro dubbed the family of malicious extensions Droidclub and discovered they included a software library with so-called "session-replay scripts" used by online analytics firms.
Princeton's Center for Information Technology in November drew attention to the increasing use of session-replay scripts by third-party analytics firms on high-traffic websites.
The study looked at replay services from Yandex, FullStory, Hotjar, UserReplay, Smartlook, Clicktale, and SessionCam, which were found on nearly 500 popular sites.
The scripts allow a site owner to essentially shoulder-surf their visitors by recording and replaying your "keystrokes, mouse movements, and scrolling behavior, along with the entire contents of the pages you visit".
But instead of allowing a site owner to record and play back what users do on one site, Droidclub extensions allow the attacker to see what victims do on every single site they visit.
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/t/securite-pc-et-internet/?&tag=Cyberespionage
https://www.scoop.it/t/securite-pc-et-internet/?&tag=Privacy
https://gustmees.wordpress.com/2013/12/21/privacy-in-the-digital-world-shouldnt-we-talk-about-it/
https://www.scoop.it/t/securite-pc-et-internet/?&tag=Session-Replay+Scripts



 Your new post is loading...
Your new post is loading...

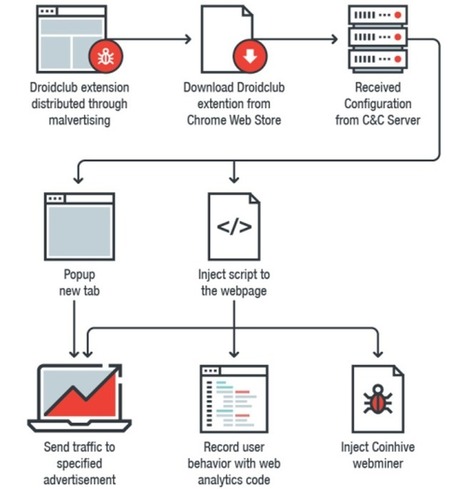











Google has removed 89 malicious extensions from the Chrome Web Store that have been installed on over 420,000 browsers, turning them into Monero-mining slaves and loading a tool to record and replay what their owners do on every website they visit.
Researchers at Trend Micro dubbed the family of malicious extensions Droidclub and discovered they included a software library with so-called "session-replay scripts" used by online analytics firms.
Princeton's Center for Information Technology in November drew attention to the increasing use of session-replay scripts by third-party analytics firms on high-traffic websites.
The study looked at replay services from Yandex, FullStory, Hotjar, UserReplay, Smartlook, Clicktale, and SessionCam, which were found on nearly 500 popular sites.
The scripts allow a site owner to essentially shoulder-surf their visitors by recording and replaying your "keystrokes, mouse movements, and scrolling behavior, along with the entire contents of the pages you visit".
But instead of allowing a site owner to record and play back what users do on one site, Droidclub extensions allow the attacker to see what victims do on every single site they visit.
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/t/securite-pc-et-internet/?&tag=Cyberespionage
https://www.scoop.it/t/securite-pc-et-internet/?&tag=Privacy
https://gustmees.wordpress.com/2013/12/21/privacy-in-the-digital-world-shouldnt-we-talk-about-it/
https://www.scoop.it/t/securite-pc-et-internet/?&tag=Session-Replay+Scripts