 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
|
La mise à jour à mi-année s’intéresse aux tendances observées entre janvier et juin 2018. Parmi les enseignements les plus significatifs, le remplacement des ransomwares comme outil de cybercriminalité de choix par les logiciels de minage de cryptomonnaie. Au cours des six derniers mois de 2017, les ransomwares représentaient 32% des attaques, alors que les attaques de minage de cryptomonnaie ne représentaient, elles, que 7%. Au premier semestre 2018, les chiffres se sont presque exactement inversés : les attaques de minage de cryptomonnaie représentent 32% des attaques, contre 8% pour les ransomwares. «Ces dernières années, les ransomwares étaient pour les cybercriminels le moyen par excellence de gagner de l’argent rapidement », déclare Karl Buffin, Directeur des Ventes Europe du Sud chez Skybox Security. « Ce genre de programmes ne nécessitent pas d’exfiltrer des données, il suffit d’utiliser le cryptage / chiffrement pour retenir en otage les données et une note explicative indiquant à la victime comment elle peut payer la rançon. Dans le cas du minage de cryptomonnaie, les criminels peuvent aller directement à la source et miner des cryptomonnaies eux-mêmes. Il n’est plus question de savoir s’ils seront payés ou pas. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Crypto+Mining https://www.scoop.it/t/securite-pc-et-internet/?&tag=RANSOMWARE

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Cyber thugs have been exploiting a zero-day flaw in the Telegram Messenger desktop app in order to mine for cryptocurrencies or to install a backdoor to remotely control victims’ computers.
Kaspersky Lab discovered “in the wild” attacks on Telegram Messenger’s Windows desktop client back in October 2017. The vulnerability in the popular Telegram app had been actively exploited since March 2017 to mine a variety of cryptocurrencies, such as Monero, Zcash, Fantomcoin and others. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Telegram

|
Scooped by
Gust MEES
|
Sicherheitsexperten von Proofpoint untersuchten das Mining-Botnet Smominru, das auf mehr als 500.000 Windows-Maschinen die Kryptowährung Minero schürft.
Nach Erkenntnissen von Sicherheitsexperten der Firma Proofpoint missbrauchen Kriminelle die Rechenleistung von mehr als einer halben Million Windows-Systemen, um die Kryptowährung Minero zu "schürfen". Laut Proofpoint handelt es sich bei den befallenen Maschinen vor allem um Windows-Server, von denen viele in Russland, Indien, Taiwan und der Ukraine laufen. Im Beobachtungszeitraum von Mai 2017 bis Januar 2018 hätten die Angreifer Mineros im Wert von rund 3,6 Millionen US-Dollar ergattert.
Server unbrauchbar
Auf den Stromkosten bleiben die Geschädigten sitzen, außerdem vermuten die Sicherheitsforscher, dass viele der befallenen Server wegen der zusätzlichen Rechenlast nur noch eingeschränkt funktionieren. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency https://www.scoop.it/t/securite-pc-et-internet/?&tag=cryptojacking

|
Scooped by
Gust MEES
|
Ransomware has caused little more than heartache and disruption for the enterprise and consumers alike, but it may soon lose its lucrative appeal in favor of cryptocurrency miners.
Over the last few years, ransomware, which targets systems, encrypts files, and demands a blackmail payment in return for a potential decryption key, has hit the spotlight time and time again.
The UK's National Health Service (NHS), major shipping companies, utilities, private businesses, and consumers at large have all fallen prey to variants including Petya, WannaCry, GoldenEye, and CryptoLocker.
This type of malware capitalizes on unpatched PCs, legacy operating systems, and vulnerabilities both old and new.
However, according to Cisco Talos researchers, cryptocurrency miners may soon take the top spot as a way for fraudsters to generate income. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Coinhive https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency https://www.scoop.it/t/securite-pc-et-internet/?&tag=cryptojacking

|
Scooped by
Gust MEES
|
Zum heimlichen Krypto-Mining im Browser hat sich jüngst eine neue Masche gesellt: Kriminelle schleusen Open-Source-Mining-Tools auf fremde PCs, um dauerhaft von deren Rechenleistung zu profitieren. Millionen von Nutzern sollen betroffen sein.
Eine aktuelle Malware-Kampagne missbraucht das quelloffene Krypto-Mining-Tool XMRig, um auf fremden Rechnern die Kryptowährung Monero zu scheffeln. Sicherheitsforscher von Palo Alto Networks beobachten die auf Windows-Systeme abzielende Schadcode-Verbreitung bereits seit über vier Monaten. Ihren Auswertungen zufolge sollen weltweit mindestens 15 Millionen Rechner mit der Mining-Malware infiziert sein – über 6.5 Millionen davon stehen in Thailand, Vietnam und Ägypten.
Anders als frühere Kryptomining-Kampagnen, die auf JavaScript-Code im Browser setzen, nistet sich der Schadcode im aktuellen Fall dauerhaft auf den Rechnern ein – der Mining-Prozess ist damit zeitlich nicht mehr auf das Surfen im Internet beschränkt. Die Malware nutzt zwei Visual-Basic-Skripte (VBS), die zunächst ermitteln, ob es sich beim Betriebssystem des Zielrechners um eine 32- oder 64-Bit-Windows-Version handelt. Anschließend laden sie aus dem Internet die geeignete XMRig-Version nach, starten diese und beginnen mit dem heimlichen Mining. Die Erträge fließen in die digitalen Geldbeutel der Malware-Macher. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Crypto+Mining https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
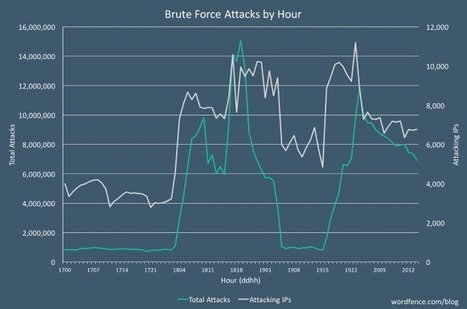
Over the course of the current week, WordPress sites around the globe have been the targets of a massive brute-force campaign during which hackers attempted to guess admin account logins in order to install a Monero miner on compromised sites.
The brute-force attack started on Monday morning, 03:00 AM UTC and is still going strong at the time of writing.
Brute-force attack targets over 190,000 WordPress sites/hour
To get an idea of the size of the campaign, WordPress security firm Wordfence says this was the biggest brute-force attack the company was forced to mitigate since its birth in 2012. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=WordPress

|
Scooped by
Gust MEES
|
Webseitenbesucher für Crypto-Mining missbraucht
Der Boom um Kryptowährungen hält weiter an. Um an der zunehmenden Wertsteigerung teilzuhaben, missbrauchen manche Webseitenbetreiber sogar die Rechenleistung ihrer Nutzer für das Mining.
Die Anzahl der Webseiten mit Coinhive-Skript ist besonders in den letzten Monaten geradezu sprunghaft angestiegen.
(Quelle: Sophos )
Blockchain-basierte Währungen wie Bitcoin werden immer beliebter. Mehr und mehr Menschen wollen am enormen Wertanstieg der Digitaldevisen mitverdienen; und das auch mit teilweise fragwürdigen Mitteln. Relativ neu ist etwa das Ausnutzen der Rechenleistung von Webseiten-Besuchern zum Mining, also zum Generieren von Kryptowährungen.
Wie die Experten von Sophos beschreiben, ist dazu lediglich eine in JavaScript geschriebene Anwendung des Anbieters Coinhive notwendig. Ist diese in die Webseite integriert, wird das Tool beim Aufruf der Seite automatisch heruntergeladen. Und schon beginnt der Computer im Hintergrund die Kryptowährung Monero zu schürfen.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency
|

|
Scooped by
Gust MEES
|
A new form of cryptocurrency mining malware uses a leaked NSA-exploit to spread itself to vulnerable Windows machines, while also disabling security software and leaving the infected computer open to future attacks.
The Python-based malicious Monero miner has been uncovered by researchers at security company Fortinet who've dubbed it PyRoMine. It first appeared this month and spreads using EternalRomance, a leaked NSA-exploit which takes advantage of what until a year ago had been an undisclosed SMB vulnerability to self-propagate through networks.
EternalRomance helped spread BadRabbit ransomware and is similar in many ways to EternalBlue, a second leaked NSA exploit which helped fuel WannaCry and NotPetya. Both exploits look for public-facing SMB ports, allowing them to deliver malware to networks.
Researchers discovered the malware was downloadable from a particular web address as a zip file, bundled with Pyinstaller, a program which packages programs written in Python into stand alone executables, meaning there's no need for Python to be installed on the compromised machine.
The malicious code behind PyRoMine appears to have been directly copied from a publicly shared EternalRomance implementation. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency

|
Scooped by
Gust MEES
|
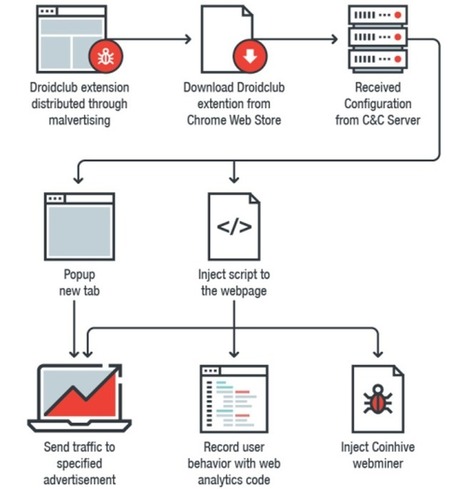
Google has removed 89 malicious extensions from the Chrome Web Store that have been installed on over 420,000 browsers, turning them into Monero-mining slaves and loading a tool to record and replay what their owners do on every website they visit.
Researchers at Trend Micro dubbed the family of malicious extensions Droidclub and discovered they included a software library with so-called "session-replay scripts" used by online analytics firms.
Princeton's Center for Information Technology in November drew attention to the increasing use of session-replay scripts by third-party analytics firms on high-traffic websites.
The study looked at replay services from Yandex, FullStory, Hotjar, UserReplay, Smartlook, Clicktale, and SessionCam, which were found on nearly 500 popular sites.
The scripts allow a site owner to essentially shoulder-surf their visitors by recording and replaying your "keystrokes, mouse movements, and scrolling behavior, along with the entire contents of the pages you visit".
But instead of allowing a site owner to record and play back what users do on one site, Droidclub extensions allow the attacker to see what victims do on every single site they visit. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Cyberespionage https://www.scoop.it/t/securite-pc-et-internet/?&tag=Privacy https://gustmees.wordpress.com/2013/12/21/privacy-in-the-digital-world-shouldnt-we-talk-about-it/ https://www.scoop.it/t/securite-pc-et-internet/?&tag=Session-Replay+Scripts

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Why go to all the bother of writing ransomware that demands victims pay a Bitcoin ransom? If all you want is cryptocurrency, why not use the infected computers to mine the crypto coins themselves?
That way you don’t have to rely on a human victim buying some Bitcoin, and nervously making their way onto the dark web to make their ransom payment.
According to security researchers at Proofpoint, that’s exactly the reasoning shown by online criminals who are moving from regular ransomware to cryptomining.
A Monero-mining botnet called Smominru is said to have infected 526,000 Windows PCs since May 2017 – mostly in Russia, India, and Taiwan – and is earning millions of dollars for its operators. In fact, the biggest clue that most users will have that their computers may be affected by a cryptominer is if they found the PC is slowing down, its battery running out at a quicker rate, or the fan blowing at full blast. Don’t make the mistake of thinking that this is a victimless crime. If your computers get recruited into a cryptomining botnet like Smominru, it’s your electricity and computer power that is being stolen. Keep your computers up-to-date with security patches, defended with layered security solutions, and your wits about you. Learn more / En savoir plus / mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Coinhive https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency https://www.scoop.it/t/securite-pc-et-internet/?&tag=cryptojacking

|
Scooped by
Gust MEES
|
As Ars Technica reports, YouTube has been spotted pushing ads onto users.
That, in itself, isn't newsworthy of course. But these ads are surreptitiously stealing resources from visiting computers to mine for cryptocurrencies:
On Friday, researchers with antivirus provider Trend Micro said the ads helped drive a more than three-fold spike in Web miner detections. They said the attackers behind the ads were abusing Google's DoubleClick ad platform to display them to YouTube visitors in select countries, including Japan, France, Taiwan, Italy, and Spain.
The ads contain JavaScript that mines the digital coin known as Monero. In nine out of 10 cases, the ads will use publicly available JavaScript provided by Coinhive, a cryptocurrency-mining service that's controversial because it allows subscribers to profit by surreptitiously using other people's computers. The remaining 10 percent of the time, the YouTube ads use private mining JavaScript that saves the attackers the 30 percent cut Coinhive takes. Both scripts are programmed to consume 80 percent of a visitor's CPU, leaving just barely enough resources for it to function.
You should run an ad blocker when you surf the web.
================================================== Not just because ads are invariably ugly and ruin the user experience. Not just because you don't want ads tracking your online behaviour. Not just because ads slow down your online experience and gobble up your bandwidth. Not just because ads can infect your computer with malware, or be secretly sapping your computer resources by mining for cryptocurrencies in the background. ==================================================
But because even Google, one of the world's largest advertising companies (with its own considerable security prowess), seems to be incapable of guaranteeing a stream of safe ads. What hope for the other advertising networks if Google can't get it right? Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Coinhive https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency https://www.scoop.it/t/securite-pc-et-internet/?&tag=cryptojacking

|
Scooped by
Gust MEES
|
Stealth cryptocurrency mining in one’s browser, without the user’s permission, is one of our least-favorite trends of the past six months. While there were always questions about whether cryptocurrency mining in-browser could serve as an alternate revenue stream for websites, there was at least an idea that some kind of alternate funding system might emerge — hopefully putting an end to the eternal cycle of invasive ads driving users to deploy ad blockers, which then drives websites to adopt more invasive ads.
But instead of an informed approach in which end users consented to such mining, we’ve seen stealth operations popping up everywhere that steal CPU cycles from users, particularly if more than one crypto mining malware is running simultaneously. While most of these plugins are written to only put a light load on user’s CPUs, that’s only if the miner is running in a single browser instance, and only if it’s running on a single site. Our tests back in 2017 showed that using different browsers can defeat this dubious attempt to sandbox the performance impact. And, of course, even running one site will still drain battery life more quickly than having the CPU properly idled.
It’s like someone figured out how to monetize the awful Flash ads everyone used to hate for eating CPU cycles. A true win-win! And now it’s even hitting YouTube.
TrendMicro has released an updated report, showing a sharp rise in ads served by Google’s DoubleClick service being infested with mining software. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Coinhive https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency https://www.scoop.it/t/securite-pc-et-internet/?&tag=cryptojacking

|
Scooped by
Gust MEES
|
Cryptocurrency miners are a new scourge on the web. Web pages can now embed JavaScript code that runs in your web browser to mine themselves Bitcoin or other cryptocurrencies using your computer. The website keeps the cryptocurrency, and you get higher electric bills, 100% CPU usage that drags down your computer, and reduced battery life. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency https://www.scoop.it/t/ict-security-tools/?&tag=Coin+Miners

|
Scooped by
Gust MEES
|
What would you like with your latte? Cocoa? Cinnamon? Sprinkle of cryptocurrency mining piggybacking off your free Wi-Fi?
Recent visitors to a Buenos Aires Starbucks didn’t actually have a choice: instead, a 10-second delay was foisted on them when they connected to the coffee shop’s “free” Wi-Fi, as their laptops’ power secretly went to mine cryptocoins (of which the Starbucks customers received nary one slim dime, of course).
The mining was noticed by Stensul CEO Noah Dinkin, who took to Twitter on 2 December to ask Starbucks if it was aware of what was going on. He included a screenshot of the code.
Dinkin said in his tweet that the code was mining bitcoins, but it was actually CoinHive code, which offers a JavaScript miner for generating a cryptocurrency called Monero that’s an alternative to Bitcoin. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency

|
Scooped by
Gust MEES
|
Eine Schule im Brandenburger Land, The Pirate Bay und etliche Webseiten aus der Alexa-Top-1-Million-Liste schürfen ungefragt Kryptowährungen auf den Rechnern der Nutzer. Der Anbieter Coinhive will das Verfahren künftig anpassen, damit es weniger Ärger gibt.
Immer mehr Webseiten schürfen ungefragt und ohne Kennzeichnung auf Kosten der Nutzer Kryptowährungen wie Monero. Nach einem Testlauf bei der Torrent-Seite The Pirate Bay verschwand der entsprechende Code des Anbieters Coinhive kurzzeitig wieder aus dem Quelltext der Seite, ist aber mittlerweile wieder integriert. Außerdem gibt es zahlreiche Nachahmer. Richtig lohnen dürfte sich das allerdings nur für die wenigsten Seitenbetreiber - den Verlust an Reputation bei den Besuchern dürfte es kaum wiedergutmachen, wenn diese davon Kenntnis erlangen. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency http://www.scoop.it/t/securite-pc-et-internet/?&tag=cryptocurrency+mining
|



 Your new post is loading...
Your new post is loading...













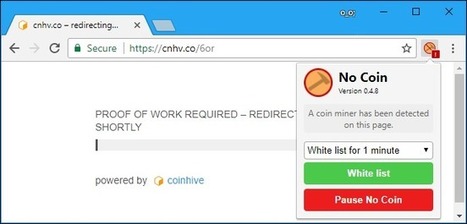

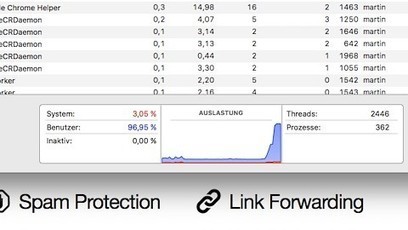





La mise à jour à mi-année s’intéresse aux tendances observées entre janvier et juin 2018. Parmi les enseignements les plus significatifs, le remplacement des ransomwares comme outil de cybercriminalité de choix par les logiciels de minage de cryptomonnaie. Au cours des six derniers mois de 2017, les ransomwares représentaient 32% des attaques, alors que les attaques de minage de cryptomonnaie ne représentaient, elles, que 7%. Au premier semestre 2018, les chiffres se sont presque exactement inversés : les attaques de minage de cryptomonnaie représentent 32% des attaques, contre 8% pour les ransomwares.
«Ces dernières années, les ransomwares étaient pour les cybercriminels le moyen par excellence de gagner de l’argent rapidement », déclare Karl Buffin, Directeur des Ventes Europe du Sud chez Skybox Security. « Ce genre de programmes ne nécessitent pas d’exfiltrer des données, il suffit d’utiliser le cryptage / chiffrement pour retenir en otage les données et une note explicative indiquant à la victime comment elle peut payer la rançon. Dans le cas du minage de cryptomonnaie, les criminels peuvent aller directement à la source et miner des cryptomonnaies eux-mêmes. Il n’est plus question de savoir s’ils seront payés ou pas.
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/t/securite-pc-et-internet/?&tag=Crypto+Mining
https://www.scoop.it/t/securite-pc-et-internet/?&tag=RANSOMWARE