When news of the Shellshock vulnerability broke out at the end of September, we spotted several attacks that leveraged the said vulnerability, thus manifesting the prevalence or even evolution on how attackers used the exploit. For instance, attackers used Shellshock to target SMTP servers, launch botnet attacks, and even to download KAITEN source code among others.
Research and publish the best content.
Get Started for FREE
Sign up with Facebook Sign up with X
I don't have a Facebook or a X account
Already have an account: Login
ICT Security + Privacy + Piracy + Data Protection - Censorship - Des cours et infos gratuites sur la"Sécurité PC et Internet" pour usage non-commercial... (FR, EN+DE)...
Curated by
Gust MEES
 Your new post is loading... Your new post is loading...
 Your new post is loading... Your new post is loading...
|




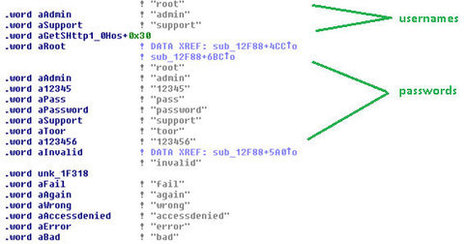






When news of the Shellshock vulnerability broke out at the end of September, we spotted several attacks that leveraged the said vulnerability, thus manifesting the prevalence or even evolution on how attackers used the exploit. For instance, attackers used Shellshock to target SMTP servers, launch botnet attacks, and even to download KAITEN source code among others.