 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
|
Zyxel has released a patch to address a critical vulnerability in its firmware concerning a hardcoded undocumented secret account that could be abused by an attacker to login with administrative privileges and compromise its networking devices.
The flaw, tracked as CVE-2020-29583 (CVSS score 7.8), affects version 4.60 present in wide-range of Zyxel devices, including Unified Security Gateway (USG), USG FLEX, ATP, and VPN firewall products. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Backdoor

|
Scooped by
Gust MEES
|
Researchers discovered multiple flaws in more than 40 device drivers from at least 20 different vendors that could to install a persistent backdoor on Windows PCs.
Experts at firmware security firm Eclypsium have conducted a study on the device drivers from major vendors and discovered serious issues in over 40 drivers from 20 companies.
The researchers warn that the vulnerabilities that can be exploited by attackers to deploy persistent backdoor on vulnerable systems.
Flawed drivers were developed by several major vendors, including ASUS, Toshiba, Intel, NVIDIA, and Huawei, below the complete list: Learn more / En savooir plus / Mehr erfahren: https://www.scoop.it/topic/securite-pc-et-internet

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Neue Malware installiert Hintertüren auf Macs
Malware gibt es auch für Mac-Nutzer. Kaspersky hat die OS-X-Variante einer Backdoor-Software entdeckt, die auch für Windows und Linux existiert. Angreifer können damit Tastaturanschläge protokollieren und gezielt nach Dateien suchen.
Eine neue Malware für OS X installiert eine Hintertür auf dem Rechner der Nutzer, wie Kaspersky schreibt. Die Software mit dem Namen OSX.Mokes wurde im Januar dieses Jahres bereits in Versionen für Linux und Windows entdeckt.
Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?tag=cross-platform http://www.scoop.it/t/securite-pc-et-internet

|
Scooped by
Gust MEES
|
Security researchers with Russian anti-virus company Doctor Web have examined a complex, multi-purpose backdoor for Linux. This malicious program can execute various commands issued by intruders such as to mount DDoS attacks and to perform a wide range of other malicious tasks.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Linux

|
Scooped by
Gust MEES
|
Bei einer Analyse eines sich seltsam verhaltenden Domain Controllers entdeckten Sicherheitsspezialisten eine ganz besondere Hintertür: Einbrecher hatten die Windows Server so manipuliert, dass ein Master-Passwort universellen Zugang gewährte.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Skeleton-Key

|
Scooped by
Gust MEES
|
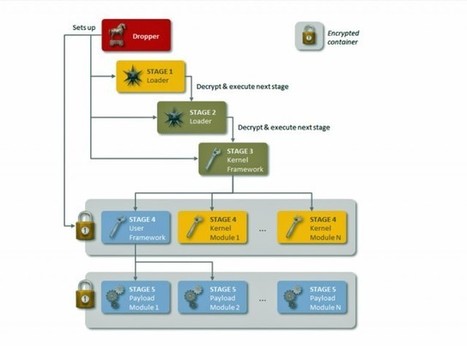
Researchers have unearthed highly advanced malware they believe was developed by a wealthy nation-state to spy on a wide range of international targets in diverse industries, including hospitality, energy, airline, and research.
Backdoor Regin, as researchers at security firm Symantec are referring to the trojan, bears some resemblance to previously discovered state-sponsored malware, including the espionage trojans known as Flame and Duqu, as well as Stuxnet, the computer worm and trojan that was programmed to disrupt Iran's nuclear program. Regin likely required months or years to be completed and contains dozens of individual modules that allowed its operators to tailor the malware to individual targets.
To remain stealthy, the malware is organized into five stages, each of which is encrypted except for the first one. Executing the first stage triggers a domino chain in which the second stage is decrypted and executed, and that in turn decrypts the third stage, and so on. Analyzing and understanding the malware requires researchers to acquire all five stages. Regin contains dozens of payloads, including code for capturing screenshots, seizing control of an infected computer's mouse, stealing passwords, monitoring network traffic, and recovering deleted files. Other modules appear to be tailored to specific targets. One such payload included code for monitoring the traffic of a Microsoft IIS server. Another sniffed the traffic of mobile telephone base station controllers.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=REGIN
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Warriorpride
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Quantum
- http://www.scoop.it/t/securite-pc-et-internet/?tag=cyberwar
- http://www.scoop.it/t/securite-pc-et-internet/?tag=NSA
- http://www.scoop.it/t/securite-pc-et-internet/?tag=TAO
- https://gustmees.wordpress.com/2012/05/21/visual-it-securitypart2-your-computer-as-a-possible-cyber-weapon/
Bösartige Angreifer kapern Apache-Webserver und leiten deren Besucher auf Schad-Websites um. Die Tarnung der Malware ist fast perfekt. Eine Hintertür, die von Administratoren nur schwer bemerkt werden kann, sorgt dafür, dass Internet-Anfragen an Apache-Server nicht in Logs aufgenommen werden. Die gesendeten http-Anfragen, die in Wirklichkeit einen Trojaner steuern, sind nicht ersichtlich. Der Rest des Angriffs läuft im Speicher ab, Bugfixes gibt es noch nicht. 29. April 2013 von Manfred Kohlen 0
Die Malware Linux/Cdorked.A ist eine raffinierte Hintertür, die alles tut, um den Internetverkehr auf schädliche Webseiten umzuleiten, schreibt Sicherheitsanbieter Eset in einer aktuellen Warnung. Der Schädling sei so gut, dass er laut eigener Analysen schon hunderte von Webservern unter seine Kontrolle gebracht habe.
|

|
Scooped by
Gust MEES
|
Security researchers have found another instance of a malware strain abusing the Windows Background Intelligent Transfer Service (BITS).
The malware appears to be the work of a state-sponsored cyber-espionage group that researchers have been tracking for years under the name of Stealth Falcon.
The first and only report on this hacking group has been published in 2016 by Citizen Lab, a non-profit organization focusing on security and human rights.
According to the Citizen Lab report, the Stealth Falcon group has been in operation since 2012 and was seen targeting United Arab Emirates (UAE) dissidents. Previous tools included a very stealthy backdoor written in PowerShell. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Cyberespionage

|
Scooped by
Gust MEES
|
Zyklon, a fully featured backdoor, is making the rounds using recently patched vulnerabilities in Microsoft Office.
The dismally named code has been around since early 2016; it’s an HTTP malware with a wide range of capabilities, including keylogging, password harvesting, downloading and executing additional plugins, conducting distributed denial-of-service (DDoS) attacks and self-updating and self-removing. FireEye researchers, who uncovered this latest wave of attacks, said that it also can download several plugins from browsers and email software, some of which include features such as cryptocurrency mining and password recovery. Additionally, Zyklon has a mechanism to monitor the spread and impact of its activities and uses the Tor anonymity network to communicate with its command-and-control (C2) server.
In an analysis, FireEye found that Zyklon is being delivered primarily through spam emails with an attached malicious Word document, targeting telecommunications, insurance and financial services. It’s using two Microsoft vulnerabilities: CVE-2017-8759, which was discovered by FireEye in September 2017, and CVE-2017-11882, a remote code execution bug.
CVE-2017-8759 is a .NET framework issue patched by Microsoft in October. An exploit allows attackers to install programs, manipulate data and create new privileged accounts. The second vulnerability was patched in November – though it was found to have existed for 17 years.
The threat actors are banking on administrators taking their time patching – a common tactic. Users should, of course, update their systems as soon as possible, given Zyklon’s virulent abilities. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet

|
Scooped by
Gust MEES
|
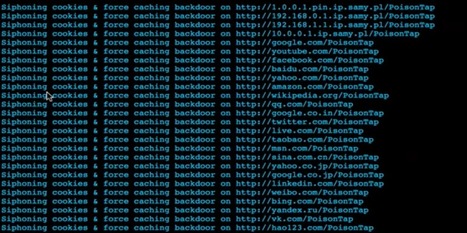
Even the strongest passwords are fallible, and as Samy Kamkar demonstrates, sometimes it doesn’t take much. Kamkar’s new exploit, PoisonTap, uses free software and a $5 Raspberry Pi Zero microcomputer. After attaching the Raspberry Pi to a USB adapter and plugging it in, the device goes to work. In all of 30 seconds, it bypasses your …

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Security researchers have released a report examining a social engineering operation designed to trick admins into installing backdoor malware called CrytoPHP by way of of tainted CMS plugins and themes for WordPress, Joomla and Drupal.
The attackers lure targets into publishing the pirated themes and plugins by providing them for free, offerings that usually incur a fee for use.
“After being installed on a webserver the backdoor has several options of being controlled which include command and control server communication, mail communication as well as manual control,” the researchers revealed.
Many poorly-secured company servers are exposed online, offering attackers ready made backdoors to wipe or steal data Moore’s scan found 308,000 BMCs that used the problem protocol identified by Farmer. A total of 53,000 of them were configured in a way that allows access without a password; 195,000 stored passwords and other credentials unencrypted; 99,000 exposed encoded passwords that could be cracked by an attacker (Moore says that he unscrambled 10 percent in a preliminary test); 35,000 had vulnerabilities in the Universal Plug and Play protocol that Moore’s previous Internet scan highlighted.
|



 Your new post is loading...
Your new post is loading...




















Zyxel has released a patch to address a critical vulnerability in its firmware concerning a hardcoded undocumented secret account that could be abused by an attacker to login with administrative privileges and compromise its networking devices.
The flaw, tracked as CVE-2020-29583 (CVSS score 7.8), affects version 4.60 present in wide-range of Zyxel devices, including Unified Security Gateway (USG), USG FLEX, ATP, and VPN firewall products.
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/t/securite-pc-et-internet/?&tag=Backdoor