 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
|
F5 Networks announced the findings of its 2013 RSA Security Trends Survey, which revealed that organizations are struggling to keep pace with the changing face of security. Respondents were RSA attendees with IT responsibilities over planning, management, oversight, or implementation of security.
BYOD is seen as critical in an organization’s ability to achieve the level of security it desires, yet a sizeable number of organizations are not taking the appropriate steps to address it. Most (75%) see BYOD as being prevalent in their organization.Furthermore, two-thirds (66%) see BYOD as having a somewhat to extremely high impact on security.Despite this, one-third (35%) say they are not prepared to provide adequate security to protect against threats associated with BYOD.
Spoofing, banking attacks, authentication flaws, and more top the list of 2012's biggest mobile security headaches

|
Scooped by
Gust MEES
|
An infographic from security-testing company Veracode explores the rise of data breaches and what it could mean for businesses and consumers.

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
While mobile device management will always be in use in the enterprise, thankfully, a better option exists. In fact, it seems the only group not excited about BYOD is IT – the ones who have to figure out how to keep sensitive corporate information safe. IT's consternation over BYOD is made worse by the fact that many think mobile device management (MDM) is the only tool available to contain the risks associated with BYOD, which is not the case. MDM will always have a place in the enterprise because BYOD will simply never be the right approach for every employee. However, when it comes to BYOD implementations, MDM is not ideal. Thankfully, a better option exists. Mobile application management (MAM) presents an intriguing option for preparing for and avoiding the hazards of BYOD. Read more, a MUST: http://www.scmarketscope.com/mdm-and-byod-a-square-peg-for-a-round-hole/article/260623/

|
Scooped by
Gust MEES
|
Antivirus app for Android expected to be integrated into Sophos mobile-device management...

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
As BYOD Trend Grows So Do Malware Attacks
The report found that the majority of employee’s devices did not have any form of security software loaded nor were company materials protected. The BYOD concept has been a growing trend for some years now as employees become more accustomed to using their own mobile computing devices in their jobs, and accessing corporate assets. The rapid adoption of high end smartphones and tablets including iPhones, iPads and Android devices along with the number of easily accessible apps is driving this concept forward. Cloud based services, accessible from almost anywhere, are also a key factor. The ‘Mobile Security Strategies: Threats, Solutions & Market Forecasts 2012-2017’ report report from Juniper found that while this trend can bring productivity benefits to businesses, it also poses potential security risks. In particular, the report found that the majority of employee’s phones and smart devices did not have any form of security software loaded nor were company materials protected. The new report provides detailed assessments of the mobile security threat and the growing market for security solutions. The war on cybercrime therefore continues for many organizations and especially their IT departments and CISOs. The total number of Computer viruses, trojans and web attacks is growing at their fastest pace in four years. Read more, a MUST: http://www.infosecisland.com/blogview/22364-As-BYOD-Trend-Grows-So-Do-Malware-Attacks.html?utm_source=dlvr.it&utm_medium=twitter

|
Scooped by
Gust MEES
|
Katy Independent School District (ISD) has a student population of 63,000 students and 56 schools – elementary, middle and high schools. There are 83 languages spoken by students in the district and 31 percent of the student population is on free or reduced lunch programs.
In 2009, Katy began a three-year plan to change instruction in the school district by promoting a standardized toolbox of web-based tools dubbed “Web 2.0.” They also set out guidelines for behavior in the digital space called “Digital Citizenship,” in the hopes that the school would not just teach kids math and reading, but also how to behave in a public digital world. Gust MEES: while using "Bring Your Own Device" (Hashtag on Twitter = #BYOD) you must also take care about IT-Security and Privacy! Check my FREE course who explains in detail: - http://gustmees.wordpress.com/2012/07/07/bring-your-own-device-advantages-dangers-and-risks/ Read more: http://knolinfos.visibli.com/share/ZcOoM3

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Bring your own device (BYOD) has become increasingly more prevalent in businesses with over 71% of companies planning, tolerating or supporting its infiltration into normal corporate work practices, according to an infograph published by Matrix 42. According to the below infograph the most common devices being utilised by employees via BYOD for work are laptops, PDA’s, mobile devices, and tablet computers. The Matrix 42 infograph was developed after the company completed a survey of 600 enterprise IT professionals and was published via Visual.ly. Top Ten tips for mobile security... Read moree, a MUST: http://www.certificationeurope.com/blog/byod-is-becoming-a-prevalent-information-security-and-it-management-focus/

|
Scooped by
Gust MEES
|
|
People may think their shiny new smartphones and tablets are safe from hackers and malicious software, but that isn't the case, Internet security

|
Scooped by
Gust MEES
|
With a new year come new challenges. But while many see bringyourowndevice gaining momentum, more organizations may be ready to issue their own handhelds to employees.

|
Scooped by
Gust MEES
|
Mobile Device Security: What Senior Managers Should Know
Next-generation mobile devices like iPads and Android phones can do wonders for mobile workers and drive productivity and innovation in business. However, new devices bring increased cost of administration, risk of data loss and reputation damage if they aren’t managed correctly.
This article provides clear, practical guidance on how you can make sure mobile ===> devices are a benefit rather than a risk for your organization. <=== Read more, a MUST: http://www.sophos.com/en-us/security-news-trends/security-hubs/mobile-security/mobile-security-101.aspx

|
Scooped by
Gust MEES
|
The BYOD trend will make cyber security more complex Of the tips put forward by IDC, the first one is perhaps the most obvious and perhaps the reasons why the BYOD trend has caused so many headaches. “The consensus is that BYOD is now a given. Whether you want it or not, employees will do your work on their own devices,” says Infosec commentator Stilgherrian. “So your choice is whether to have a policy that acknowledges that and lays out the ground rules, or try to ban it and end up with an infestation of unknown and uncontrolled devices.” However, as many enterprises are currently finding out, controlling and securing data on multiple devices is a lot easier said than done. Read more, a MUST: http://technologyspectator.com.au/byod-security-commandments

|
Scooped by
Gust MEES
|
Is IT becoming a consumer product?... Most people are participating in rogue IT without even realizing it. By definition, rogue IT is the unmanaged hardware and software that employees bring into their offices, connect to employers’ networks and use for professional productivity on personal time. At first, it doesn’t sound so bad. By allowing employees to connect to the Wi-Fi with their own devices, companies avoid the cost of providing the hardware. But as we learned from the BYOD toolkit from CIO.gov, BYOD programs aren’t profitable if they are uncontrolled, because problems, like the ones we’ll discuss below, arise. ===> Rogue IT is innovative and efficient for workers, but it’s becoming a real problem for IT managers. Here are four trends that are shaking up IT: <=== Gust MEES: check out also my FREE course about it here - http://gustmees.wordpress.com/2012/07/07/bring-your-own-device-advantages-dangers-and-risks/ Read more: http://www.statetechmagazine.com/article/2012/09/4-rogue-it-trends-watch-out

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
(Phys.org)—Spyware sold legally can infect BlackBerrys, iPhones, and other mobile devices, according to a study from two security researchers at the University of Toronto Munk School of Global Affairs' Citizen Lab. Gust MEES: NOBODY IS PERFECT! Read more: http://phys.org/news/2012-09-toronto-mobile-spyware-shadow.html

|
Scooped by
Gust MEES
|
By Jim Finkle LAS VEGAS (Reuters) - Hacking experts have demonstrated ways to attack Android smartphones using methods they said work on virtually all such devices in use today, despite recent efforts by search engine giant Google to...
|



 Your new post is loading...
Your new post is loading...





![Why You Should Care About Mobile Security [INFOGRAPHIC] | ICT Security-Sécurité PC et Internet | Scoop.it](https://img.scoop.it/bCDzCBQu4qMgWJAbygdm2jl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)
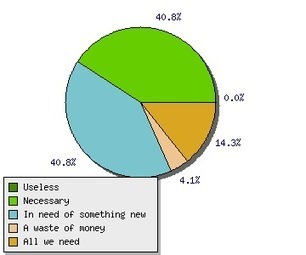


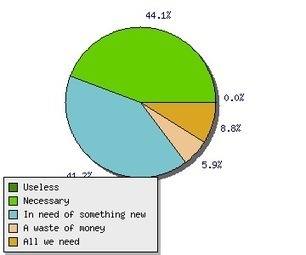


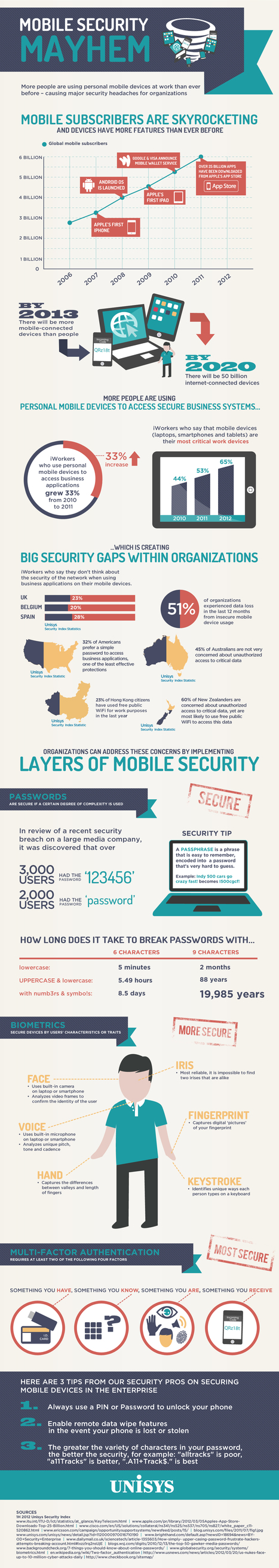
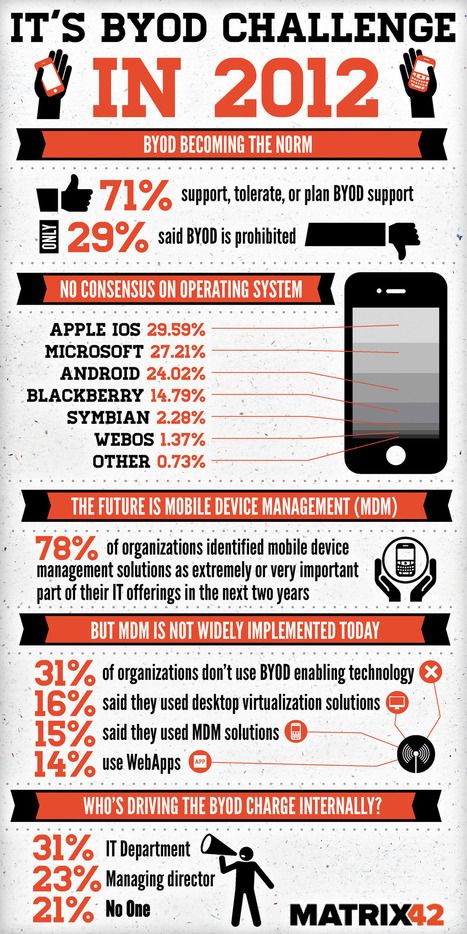



















Check also:
- http://gustmees.wordpress.com/2012/07/07/bring-your-own-device-advantages-dangers-and-risks/