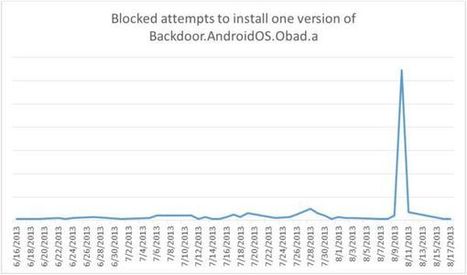
We've recently found a vulnerability in certain Android apps that may leave user data at risk of being captured or being used to launch attacks.
Get Started for FREE
Sign up with Facebook Sign up with X
I don't have a Facebook or a X account
 Your new post is loading... Your new post is loading...
 Your new post is loading... Your new post is loading...

malek's curator insight,
September 17, 2013 8:23 AM
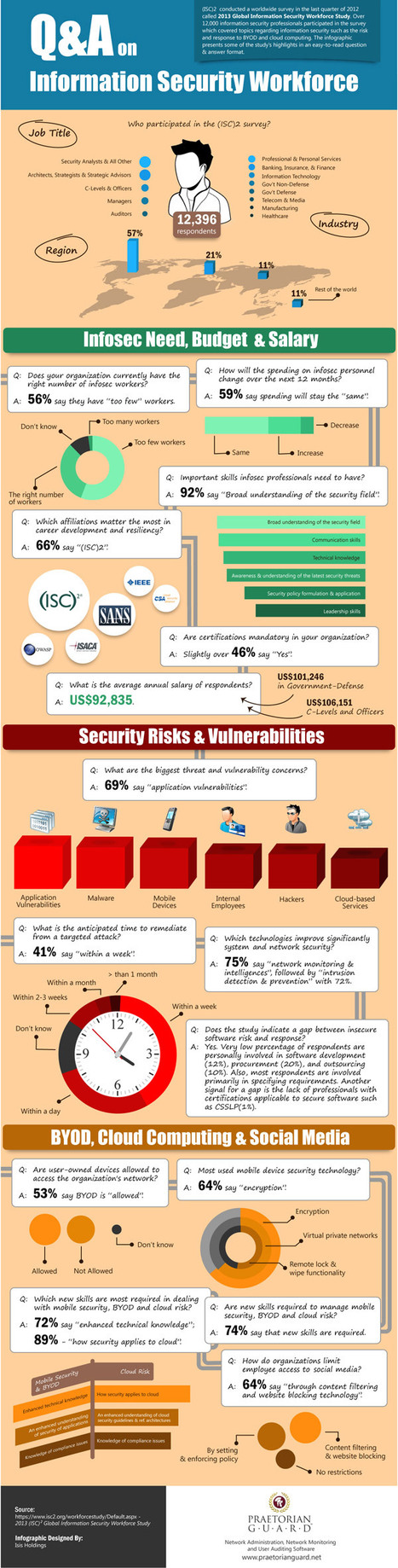
A myriad of threats: * Employers often cannot assess data breach exposure on unmanaged BYODs *Lost or stolen BYODs that contain sensitive data, with less than 1 in 4 can be remotely wiped. * When BYODs bypass inbound filters normally applied to corporate devices, they’re vulnerable to malware and the list goes on and on 
TheSoulfulEMU's curator insight,
September 24, 2013 10:12 AM
Now that you know it, so DONT- BYOD!!! Got it?

Gust MEES's curator insight,
July 30, 2013 4:45 PM
===> Think you're safe because you use OS X or Linux? Think again! There are devices being marketed that claim to be able to get infiltrate these operating systems too. <===
Nobody Is Perfect!!!

Gust MEES's curator insight,
July 18, 2013 4:31 AM
Meanwhile, nearly 80 per cent of respondents said they haven’t educated staff on the risks of BYOD. Learn more: - http://gustmees.wordpress.com/2012/07/07/bring-your-own-device-advantages-dangers-and-risks/

Zhao KQiang's curator insight,
March 28, 2014 6:24 AM
consider about free wifi is security or not, when you start to connect it ,just takes few seconds to check the security setting

Gust MEES's curator insight,
June 19, 2013 12:03 PM
For the first time, mobile spammers can use such information as the subscriber’s first name, zip code, income level, and ethnicity to make attacks personalized and more effective. A MUST read!!!

Gust MEES's curator insight,
May 14, 2013 5:07 PM
Read the full article to understand really...
Learn more:
- http://gustmees.wordpress.com/2013/05/13/visual-cyber-security-see-attacks-on-real-time/

asma jmari 's comment,
May 20, 2013 6:34 AM
believe it or not they do and hacking is more like a hobby some do it for fun and some just dedicate themselves to it and make it a job
|

Gust MEES's curator insight,
June 25, 2013 9:35 AM
Naturally Hamada advises using Norton Mobile Security for protection. PCMag's own Editors' Choice in this area Bitdefender Mobile Security and Antivirus 1.2.3; Lookout Mobile Security Premium held the Editors' Choice honor previously.
===> Whichever you choose, it does seem you'd be wise to protect your Android phone. <===
|









![BYOD Security Issues [Infographic] | ICT Security-Sécurité PC et Internet | Scoop.it](https://img.scoop.it/CaiNaHRcRGZDVZM2V3tufTl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)












![Mobile Threat in Action [INFOGRAPHIC] | ICT Security-Sécurité PC et Internet | Scoop.it](https://img.scoop.it/cJttrx6XoZpu_ERcpy9jUjl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)





We’ve recently found a vulnerability in certain Android apps that may leave user data at risk of being captured or being used to launch attacks. The two affected apps we investigated are both highly popular...