A total of 1,000,000 Android device users around the world encountered dangerous software between August 2013 and July 2014, according to the results of a survey carried out by Kaspersky Lab and INTERPOL. In fact, this period was the peak of cyber attacks registered in recent years.
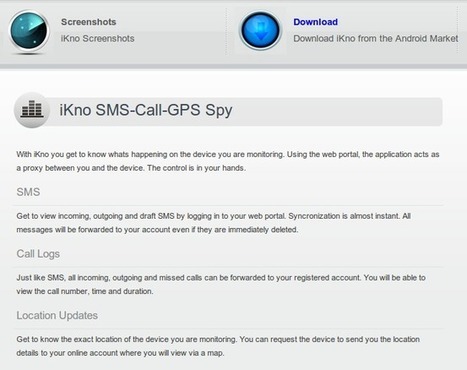
The most popular malicious programs are SMS Trojans that send messages to premium rate numbers without the owner’s awareness.
Research and publish the best content.
Get Started for FREE
Sign up with Facebook Sign up with X
I don't have a Facebook or a X account
Already have an account: Login
ICT Security + Privacy + Piracy + Data Protection - Censorship - Des cours et infos gratuites sur la"Sécurité PC et Internet" pour usage non-commercial... (FR, EN+DE)...
Curated by
Gust MEES
 Your new post is loading... Your new post is loading...
 Your new post is loading... Your new post is loading...
|
|




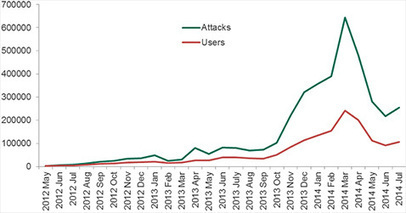




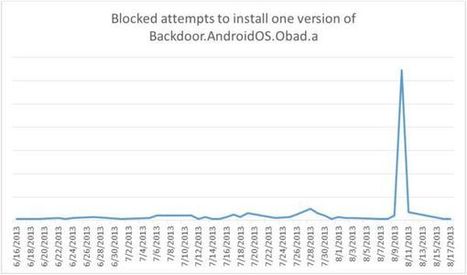






















A total of 1,000,000 Android device users around the world encountered dangerous software between August 2013 and July 2014, according to the results of a survey carried out by Kaspersky Lab and INTERPOL. In fact, this period was the peak of cyber attacks registered in recent years.
The most popular malicious programs are SMS Trojans that send messages to premium rate numbers without the owner’s awareness.