28. Oktober 2016 | Drei von vier Menschen (74,6%) speichern sensible Daten auf ihrem Smartphone ie private Bilder und Videos (57,8%) sowie Kontaktdaten von Dritten (47,9%). Zudem erlauben 29,8 Prozent der Nutzer den Direktzugriff ohne Passwortabfrage auf Nutzerkonten bei sozialen Netzwerken, E-Mail- sowie Cloud-Diensten. Fast jeder Fünfte (19,7%) hat auch Apps installiert, die persönliche Daten, etwa zur eigenen Gesundheit oder Fitness, speichern und auswerten. Gleichzeitig gaben fast 20 Prozent der Nutzer an, keinerlei Sicherheitsfunktionen zum Schutz dieser kritischen Informationen eingerichtet zu haben.
Nicht einmal die Hälfte (46,3%) führt regelmäßige Software-Updates durch, um Sicherheitslücken zu schließen.
Zu diesen Ergebnissen kommt eine repräsentative Online-Befragung von TNS Infratest im Auftrag des BSI anlässlich des European Cyber Security Month (ECSM) unter dem Motto "Smartphone & Co – sicher mobil"
Weitere Informationen zum Rundum-Schutz für mobile Geräte können auf der Seite "Schutz für Smartphone und Co" nachgelesen werden.



 Your new post is loading...
Your new post is loading...











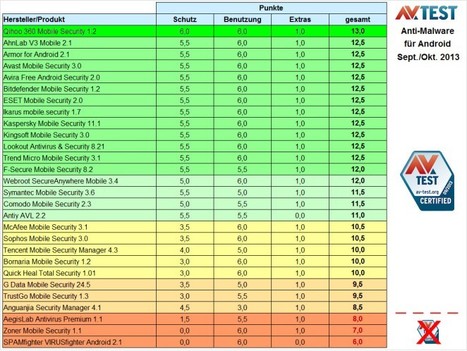
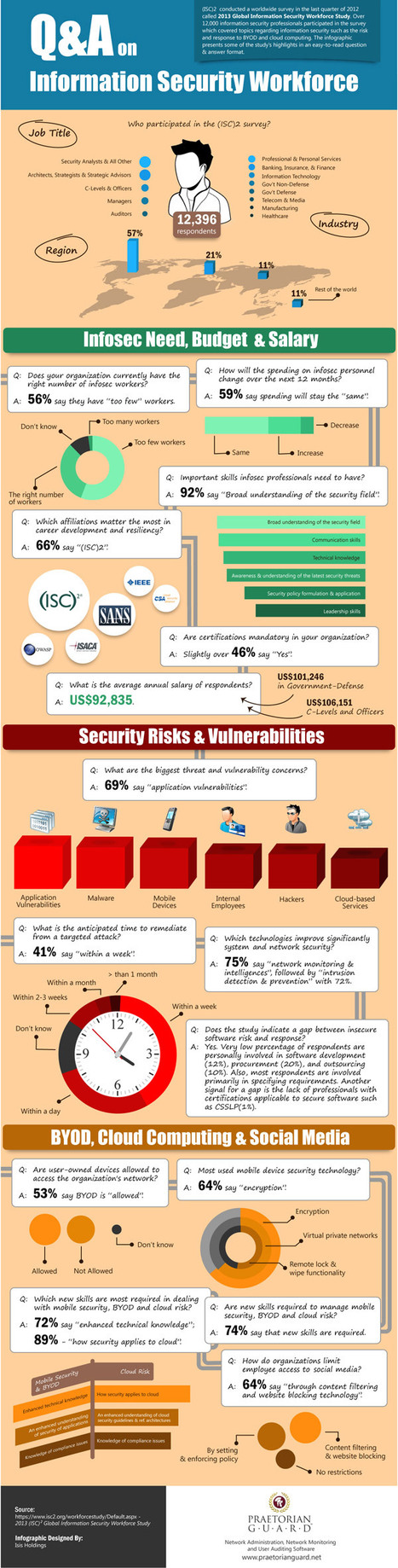

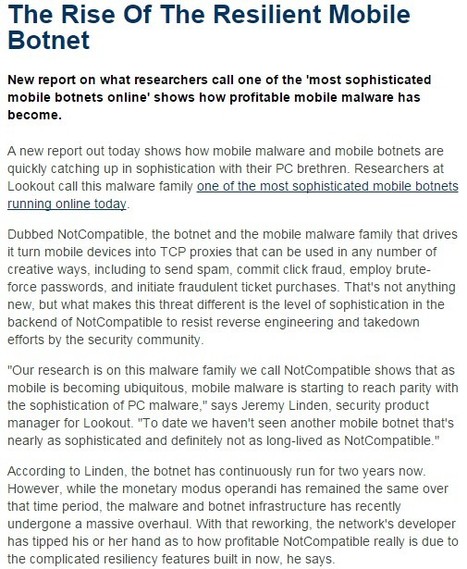
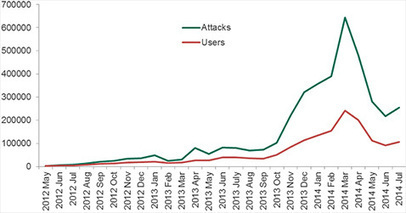







![BYOD Security Issues [Infographic] | ICT Security-Sécurité PC et Internet | Scoop.it](https://img.scoop.it/CaiNaHRcRGZDVZM2V3tufTl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)








28. Oktober 2016 | Drei von vier Menschen (74,6%) speichern sensible Daten auf ihrem Smartphone ie private Bilder und Videos (57,8%) sowie Kontaktdaten von Dritten (47,9%). Zudem erlauben 29,8 Prozent der Nutzer den Direktzugriff ohne Passwortabfrage auf Nutzerkonten bei sozialen Netzwerken, E-Mail- sowie Cloud-Diensten. Fast jeder Fünfte (19,7%) hat auch Apps installiert, die persönliche Daten, etwa zur eigenen Gesundheit oder Fitness, speichern und auswerten. Gleichzeitig gaben fast 20 Prozent der Nutzer an, keinerlei Sicherheitsfunktionen zum Schutz dieser kritischen Informationen eingerichtet zu haben.
Nicht einmal die Hälfte (46,3%) führt regelmäßige Software-Updates durch, um Sicherheitslücken zu schließen.
Zu diesen Ergebnissen kommt eine repräsentative Online-Befragung von TNS Infratest im Auftrag des BSI anlässlich des European Cyber Security Month (ECSM) unter dem Motto "Smartphone & Co – sicher mobil"
Weitere Informationen zum Rundum-Schutz für mobile Geräte können auf der Seite "Schutz für Smartphone und Co" nachgelesen werden.