 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Die Systeme der Funke Mediengruppe wurden offenbar von außen verschlüsselt. Paywalls wurden von Funke vorläufig abgeschaltet.
Die Funke Mediengruppe ist am Dienstag, dem 22. Dezember nach eigenen Angaben Opfer eines Hackerangriffs geworden. "Davon betroffen sind bundesweit zahlreiche Systeme", sagte ein Sprecher der Deutschen Presse-Agentur. "Wir arbeiten mit Hochdruck an der Lösung." Die Polizei Essen ermittelt, wie sie auf Anfrage bestätigte. Bei der Staatsanwaltschaft übernahm die Zentral- und Ansprechstelle Cybercrime (ZAC) das Verfahren, wie ein Sprecher sagte. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Cyber-Attacks

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
A newly uncovered trojan malware campaign is targeting businesses and higher education in what appears to be an effort to steal usernames, passwords and other private information as well as creating a persistent backdoor onto compromised systems.
Jupyter infostealer has been detailed by cybersecurity company Morphisec who discovered it on the network of an unnamed higher education establishment in the US. It's thought the trojan has been active since May this year.
The attack primarily targets Chromium, Firefox, and Chrome browser data, but also has additional capabilities for opening up a backdoor on compromised systems, allowing attackers to execute PowerShell scripts and commands, as well as the ability to download and execute additional malware.
The Jupyter installer is disguised in a zipped file, often using Microsoft Word icons and file names that look like they need to be urgently opened, pertaining to important documents, travel details or a pay rise.
If the installer is run, it will install legitimate tools in an effort to hide the real purpose of the installation – downloading and running a malicious installer into temporary folders in the background. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Malware

|
Scooped by
Gust MEES
|
WordPress bungles critical security 5.5.2 fix and saves face next day with 5.5.3 update.
The day after WordPress pushed out a critical 5.5.2 security update, patching a remote code execution bug and nine additional flaws, it was forced push out a second update and then a third 5.5.3 update.
The hiccup is tied to the WordPress auto-update feature that accidentally started sending 455 million websites a WordPress update (5.5.2) that caused new WordPress installs to fail. After realizing the error, it put the brakes on the rollout, and inadvertently triggered an Alpha version of WordPress to be downloaded to some customers.
The issue was corrected quickly on Oct. 30, but not before WordPress site operators reported new WordPress installs failing and others grousing over broken administration login pages. WordPress said a final 5.5.3 update is now available. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=WordPress

|
Scooped by
Gust MEES
|
Linus Torvalds has kicked off yet another development cycle for the Linux kernel, announcing the release of 5.10-rc1, and this time with an historical twist. The new version of the kernel effectively marks the end of a decade-old feature that has long been made redundant after it was found to cause security bugs.
With the closing of the two-week-long merge window, which precedes the release of every new iteration of the Linux kernel, Torvalds shared his reflections on the Linux kernel mailing list, maintaining that "things seem to have gone fairly smoothly".
The merging window is a key part of any new kernel release process, during which up to 1,000 patches submitted by the developer community are merged every day into the mainline repository managed by Torvalds. A review process ensures that each patch implements a desirable change. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Linux

|
Scooped by
Gust MEES
|
Recherches CyberArk : des vulnérabilités dans le protocole LoRaWAN vulnérabilisent des réseaux IoT
octobre 2020 par CyberArk
Les chercheurs de CyberArk ont découvert que des failles courantes d’un protocoles de sécurité IoT exposent les réseaux de ces objets aux attaques, dont les conséquences pourraient être désastreuses.
Des vulnérabilité de LoRaWAN (Long Range Wide Area Network) permettent ainsi aux cybercriminels d’ajouter des appareils compromis à un réseau IoT, à l’aide du protocole MQTT (Message Queuing Telemetry Transport). Ces terminaux malveillants peuvent alors communiquer avec d’autres appareils connectés et procéder à une attaque par déni de service pour désactiver l’ensemble du réseau.
Les conséquences potentielles sont significatives : les entreprises, les industries et les villes elles-mêmes dépendent de plus en plus des réseaux de capteurs IoT pour des actions diverses, et pourraient donc être affectées. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Internet+of+things https://www.scoop.it/topic/securite-pc-et-internet/?&tag=iot https://www.scoop.it/topic/securite-pc-et-internet/?&tag=LoRaWAN

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Tous les appareils utilisant la norme Bluetooth 4.0 à 5.0 sont vulnérables. Les correctifs ne sont pas disponibles pour l'heure.
Les organisations à l'origine de la technologie sans fil Bluetooth viennent de publier des conseils sur la manière dont les vendeurs d'appareils peuvent atténuer une nouvelle attaque contre les appareils compatibles Bluetooth. Nommée BLURtooth, il s'agit d'une vulnérabilité dans un composant de la norme Bluetooth nommé Cross-Transport Key Derivation (CTKD).
Ce composant est utilisé pour configurer les clés d'authentification lors de l'appairage de deux appareils compatibles Bluetooth. Ce composant fonctionne en établissant deux jeux de clés d'authentification différents pour la norme Bluetooth Low Energy (BLE) et la norme Basic Rate/Enhanced Data Rate (BR/EDR). Le rôle du CTKD est de préparer les clés et de laisser les appareils jumelés décider quelle version de la norme Bluetooth ils veulent utiliser. La fonction "bi-mode" de Bluetooth est la principale utilité de ce système.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Bluetooth https://www.scoop.it/topic/securite-pc-et-internet/?&tag=BLURtooth

|
Scooped by
Gust MEES
|
Millions of WordPress sites are being probed in automated attacks looking to exploit a recently discovered plugin vulnerability, according to security researchers.
Wordfence, which itself produces a plugin for the platform, revealed news of the zero-day bug at the start of September. It affects File Manager which, as the name suggests, is a plugin that helps users to manage files on their WordPress sites.
The plugin is installed on around 700,000 WordPress sites, and although Wordfence estimates that only around 37%, or 262,0000, are still running a vulnerable version, this hasn’t stopped attackers from trying their luck against a much larger number of users.
“Attacks against this vulnerability have risen dramatically over the last few days. Wordfence has recorded attacks against over one million sites today, September 4, 2020. Sites not using this plugin are still being probed by bots looking to identify and exploit vulnerable versions of the File Manager plugin, and we have recorded attacks against 1.7 million sites since the vulnerability was first exploited,” explained Wordfence’s Ram Gall.
“Although Wordfence protects well over three million WordPress sites, this is still only a portion of the WordPress ecosystem. As such, the true scale of these attacks is larger than what we were able to record.”
The vulnerability itself could allow a remote, unauthenticated user to execute commands and upload malicious files on a target site. Gall therefore urged users to patch the issue promptly by installing the latest version of the plug, v6.9. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=WordPress

|
Scooped by
Gust MEES
|
The malware also mines Monero & Ethereum cryptocurrency on targeted devices.
We’re seeing new variants of malware being deployed every day. just yesterday we covered a skimmer funneling funds through Telegram and today we’re back with a new report by WeLiveSecurity.
Shedding light on a new malware family named KryptoCibule; the researchers report on 3 main tasks that it seeks to perform:
Mining Monero and Ethereum cryptocurrencies using a CPU and GPU respectively
Stealing funds by replacing legitimate wallet addresses with attacker-controlled ones with the help of the clipboard
Steal and extract cryptocurrency-related files
See: Best legal, safe & free online streaming sites – 2020
Alongside this, a remote administration tool (RAT) is also used to maintain access to the victim’s machine in order to control it. Furthermore, both the TOR Network and BitTorrent protocol is used for transmitting data and communication in general. This is yet another example of how legitimate services can be used by attackers for their own nefarious motives. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency https://www.scoop.it/topic/securite-pc-et-internet/?&tag=TOR

|
Scooped by
Gust MEES
|
The recently patched flaws could be abused by an unauthenticated, remote attackers to take over vulnerable websites.
A plugin that is designed to add quizzes and surveys to WordPress websites has patched two critical vulnerabilities. The flaws can be exploited by remote, unauthenticated attackers to launch varying attacks – including fully taking over vulnerable websites.
The plugin, Quiz and Survey Master, is actively installed on over 30,000 websites. The two critical flaws discovered by researchers include an arbitrary file-upload vulnerability, ranking 10 out of 10 on the CVSS scale; as well as an unauthenticated arbitrary file deletion error, ranking 9.9 out of 10. A patch is available for both issues in version 7.0.1 of the plugin, said the researchers with Wordfence who discovered the flaws, in a Thursday post. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=WordPress

|
Scooped by
Gust MEES
|
Die beliebten Themes Divi und Extra von Elegant Themes sowie deren Divi Builder enthielten kritische Sicherheitslücken. Wenige Tage nachdem das Team von Wordfence diese entdeckt und gemeldet hat, stellt der Anbieter Updates bereit, die das Problem beseitigen. Betreiber von WordPress-Sites, die die Plugins nutzen, sollten diese zügig installieren, da mit flächendeckenden Angriffen zu rechnen ist.
Das Problem liegt in einer mangelhaften Dateityp-Prüfung der Upload-Funktion und führt dazu, dass bösartige Benutzer beliebige Dateien hochladen können – also etwa PHP-Dateien mit einer Webshell. Der Angreifer benötigt dazu allerdings bereits einen Zugang zur Site, etwa als registrierter Benutzer. Wordfence beschreibt in seinem Advisory die Ursachen des Problems genauer. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=WordPress
|

|
Scooped by
Gust MEES
|
YOU INTUITIVELY KNOW why you should bolt your doors when you leave the house and add some sort of authentication for your smartphone. But there are lots of digital entrances that you leave open all the time, such as Wi-Fi and your cell connection. It's a calculated risk, and the benefits generally make it worthwhile. That calculus changes with Bluetooth. Whenever you don't absolutely need it, you should go ahead and turn it off.
Minimizing your Bluetooth usage minimizes your exposure to very real vulnerabilities. That includes an attack called BlueBorne, announced this week by the security firm Armis, which would allow any affected device with Bluetooth turned on to be attacked through a series of vulnerabilities. The flaws aren't in the Bluetooth standard itself, but in its implementation in all sorts of software. Windows, Android, Linux, and iOS have been vulnerable to BlueBorne in the past. Millions could still be at risk. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Bluetooth https://www.scoop.it/topic/securite-pc-et-internet/?&tag=BLURtooth

|
Scooped by
Gust MEES
|
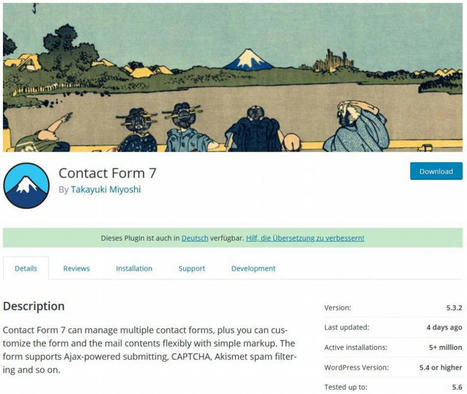
Eine Sicherheitslücke im beliebten Plug-in Contact Form 7 ermöglicht es Angreifern, Dateien jeglichen Typs hochzuladen. Ein Sicherheitsupdate ist verfügbar.
Eine gefährliche Sicherheitslücke im WordPress-Plug-in Contact Form 7 gefährdet Millionen von Word-Press-Webseiten. Gefunden wurde die Schwachstelle von Sicherheitsforschern von Astra, wie «Heise Online» berichtet.
Contact Form 7 ermöglicht es Nutzern, mehrere Kontaktformulare auf einer Webseite hinzuzufügen und ist nach Angaben des Astra-Research-Teams eines der beliebtesten WordPress-Plugins. Auf der entsprechenden WordPress-Seite sind über 5 Millionen aktive Installationen ausgewisen und das Plug-in ist in 62 Sprachen verfügbar.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=WordPress

|
Scooped by
Gust MEES
|
Der größte Anteil angreifbarer Geräte entfalle auf das Internet der Dinge (46 Prozent), gefolgt von OT (je 19 Prozent in den Teilbereichen GA und ICS) und schließlich IT mit 16 Prozent. Auf Nachfrage von heise Security sagte Forescout, dass zwar eine Vielzahl von Gerätetypen für den Business-Einsatz vertreten sei. Die große Menge verkaufter IoT-Geräte für Privatnutzer sorge jedoch dafür, dass die Gefahr auch für diese recht groß sei.
Die Angriffskomplexität ist laut Forescout in vielen Fällen gering, die Schwachstellen sehr "grundliegend". Wie schon bei Ripple20 spielt die Tatsache, dass viele IoT-Geräte für Privatnutzer – oftmals billige No-Name-Produkte – schlecht abgesichert sind und niemals Updates erhalten, Angreifern in die Hände. Unternehmensnetzwerke wiederum bieten eine höhere Zahl miteinander vernetzter, potenzieller Angriffspunkte. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Internet+of+things https://www.scoop.it/topic/securite-pc-et-internet/?&tag=iot

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Dr. Reddy’s, the contractor for Russia’s “Sputinik V” COVID-19 vaccine and a major generics producer, has had to close plants and isolate its data centers.
COVID-19 vaccine manufacturer Dr. Reddy’s Laboratories has shut down its plants in Brazil, India, Russia, the U.K. and the U.S. following a cyberattack, according to reports.
The Indian company is the contractor for Russia’s “Sputinik V” COVID-19 vaccine, which is about to enter Phase 2 human trials. The Drug Control General of India (DCGI) gave the company the go-ahead on Oct. 19.
In the U.S., it’s a major producer of generics, including therapeutics for gastrointestinal, cardiovascular, pain management, oncology, anti-infectives, pediatrics and dermatology.
In addition to shutting down plants, the drug-maker has isolated all data center services in order to apply remediations, The Economic Times reported. Citing sources, ET said that the company was victimized by a data breach. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Coronavirus

|
Scooped by
Gust MEES
|
L'équipe de sécurité de WordPress a pris une mesure qu'elle utilise rarement la semaine dernière, en utilisant une capacité interne peu connue qui permet de forcer une mise à jour de sécurité pour un plug-in populaire.
Les sites WordPress utilisant le plug-in Loginizer ont donc été mis à jour de force cette semaine, avec la version 1.6.4 de Loginizer. Cette version contient un correctif de sécurité pour un dangereux bug d'injection SQL, qui aurait pu permettre à des pirates de s'emparer de sites WordPress utilisant des versions plus anciennes du plug-in Loginizer.
Loginizer est l'un des plug-in WordPress les plus populaires aujourd'hui, avec une base d'installation de plus d'un million de sites. Il fournit des améliorations de sécurité pour la page de connexion à WordPress. Selon sa description officielle, Loginizer peut mettre sur liste noire ou blanche les adresses IP visant à accéder à la page de connexion de WordPress, ajouter la prise en charge de l'authentification à deux facteurs, ou ajouter de simples CAPTCHA pour bloquer les tentatives de connexion automatisées, parmi de nombreuses autres fonctionnalités. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=WordPress

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
A new Android malware strain has been uncovered, part of the Rampant Kitten threat group’s widespread surveillance campaign that targets Telegram credentials and more.
Researchers have uncovered a threat group launching surveillance campaigns that target victims’ personal device data, browser credentials and Telegram messaging application files. One notable tool in the group’s arsenal is an Android malware that collects all two-factor authentication (2FA) security codes sent to devices, sniffs out Telegram credentials and launches Google account phishing attacks.
Researchers found the threat group, dubbed Rampant Kitten, has targeted Iranian entities with surveillance campaigns for at least six years. It specifically targets Iranian minorities and anti-regime organizations, including the Association of Families of Camp Ashraf and Liberty Residents (AFALR); and the Azerbaijan National Resistance Organization.
The threat group has relied on a wide array of tools for carrying out their attacks, including four Windows info-stealer variants used for pilfering Telegram and KeePass account information; phishing pages that impersonate Telegram to steal passwords; and the aforementioned Android backdoor that extracts 2FA codes from SMS messages and records the phone’s voice surroundings. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Two-factor+authentication

|
Scooped by
Gust MEES
|
The “BLURtooth” flaw allows attackers within wireless range to bypass authentication keys and snoop on devices utilizing implementations of Bluetooth 4.0 through 5.0.
A high-severity Bluetooth vulnerability has been uncovered, which could enable an unauthenticated attacker within wireless range to eavesdrop or alter communications between paired devices.
The flaw (CVE-2020-15802), discovered independently by researchers at the École Polytechnique Fédérale de Lausanne (EPFL) and Purdue University, is being referred to as “BLURtooth.” The issue exists in the pairing process for Bluetooth 4.0 through 5.0 implementations. This pairing process is called Cross-Transport Key Derivation (CTKD).
“Devices… using [CTKD] for pairing are vulnerable to key overwrite, which enables an attacker to gain additional access to profiles or services that are not restricted, by reducing the encryption key strength or overwriting an authenticated key with an unauthenticated key,” according to a security advisory on Wednesday by the Carnegie Mellon CERT Coordination Center. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Bluetooth

|
Scooped by
Gust MEES
|
Emotet ist, was das Durchschnittsalter von Trojanern angeht, ein echter Greis, der Schädling erfindet sich aber immer wieder neu. Ist er einmal auf dem System, lädt er verschiedenste Schadroutinen nach, vor denen nichts sicher ist. Mit den richtigen Schutzprogrammen und kleinen Helfern wie dem Tool EmoCheck können Sie aber gegensteuern.
Auch wer sich nicht mit Computer-Sicherheit beschäftigt, hat meist schon von Emotet gehört. Schon seit mehreren Jahren treibt die Malware ihr Unwesen, mal als Banking-Trojaner oder als Passwort-Dieb oder ganz anders, denn Emotet lädt bei Bedarf immer wieder andere Schadmodule auf infizierte Systeme.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Malware https://www.scoop.it/t/securite-pc-et-internet/?&tag=Emotet

|
Scooped by
Gust MEES
|
A team of academics from Switzerland has discovered a security bug that can be abused to bypass PIN codes for Visa contactless payments.
This means that if criminals are ever in possession of a stolen Visa contactless card, they can use it to pay for expensive products, above the contactless transaction limit, and without needing to enter the card's PIN code.
The attack is extremely stealthy, academics said, and can be easily mistaken for a customer paying for products using a mobile/digital wallet installed on their smartphone.
However, in reality, the attacker is actually paying with data received from a (stolen) Visa contactless card that is hidden on the attacker's body. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/topic/securite-pc-et-internet/?&tag=VISA

|
Scooped by
Gust MEES
|
The vulnerability allows attackers to bypass Content Security Policy (CSP) protections and steal data from website visitors.
A vulnerability in Google’s Chromium-based browsers would allow attackers to bypass the Content Security Policy (CSP) on websites, in order to steal data and execute rogue code.
The bug (CVE-2020-6519) is found in Chrome, Opera and Edge, on Windows, Mac and Android – potentially affecting billions of web users, according to PerimeterX cybersecurity researcher Gal Weizman. Chrome versions 73 (March 2019) through 83 are affected (84 was released in July and fixes the issue). Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Privacy https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Browsers
|



 Your new post is loading...
Your new post is loading...






























Der Cyberangriff auf die europäische Arzneimittelbehörde wurde wohl durch chinesische Spione sowie den russischen Geheimdienst verübt. Dabei wurde auch auf COVID-19-Impfstoff-Daten zugegriffen.
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Coronavirus