ProxyBack stealthily uses your bandwidth to route traffic from a shady Russian proxy seller. ...
For as long as people have been doing productive things with software, there have been jerks making malware to screw things up and make money. As security gets better, the malware has gotten smarter over the years. Some modern variants like ransomware are pretty clever, but Palo Alto Networks has just reported discovery of something new. ProxyBack sets up anonymous proxies on infected PCs to route traffic over the victim’s connection.
There is demand for proxy connections in various countries, for both legitimate and non-legitimate uses. When ProxyBack managed to infiltrate a system (probably via deceptive software downloads), it goes to work setting up a reverse tunnel on the machine. This allows ProxyBack to circumvent security measures like software and hardware firewalls that prevent the flow of data.
Via Gust MEES




 Your new post is loading...
Your new post is loading...

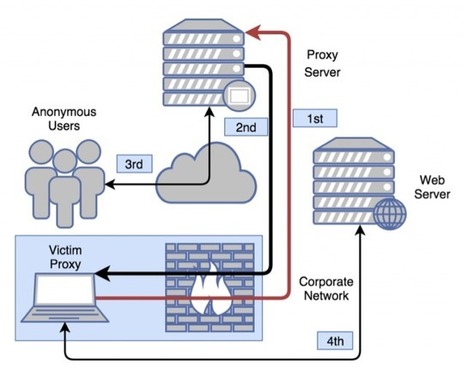









For as long as people have been doing productive things with software, there have been jerks making malware to screw things up and make money. As security gets better, the malware has gotten smarter over the years. Some modern variants like ransomware are pretty clever, but Palo Alto Networks has just reported discovery of something new. ProxyBack sets up anonymous proxies on infected PCs to route traffic over the victim’s connection.
There is demand for proxy connections in various countries, for both legitimate and non-legitimate uses. When ProxyBack managed to infiltrate a system (probably via deceptive software downloads), it goes to work setting up a reverse tunnel on the machine. This allows ProxyBack to circumvent security measures like software and hardware firewalls that prevent the flow of data.