ChatGPT est victime d’une nouvelle faille de sécurité. En exploitant cette brèche, il est possible d’extraire des données sensibles concernant des individus en s’adressant au chatbot d’OpenAI.
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/topic/21st-century-innovative-technologies-and-developments/?&tag=ChatGPT
https://www.scoop.it/t/21st-century-innovative-technologies-and-developments/?&tag=AI
https://www.scoop.it/topic/21st-century-innovative-technologies-and-developments/?&tag=Ethics
Via Gust MEES



 Your new post is loading...
Your new post is loading...







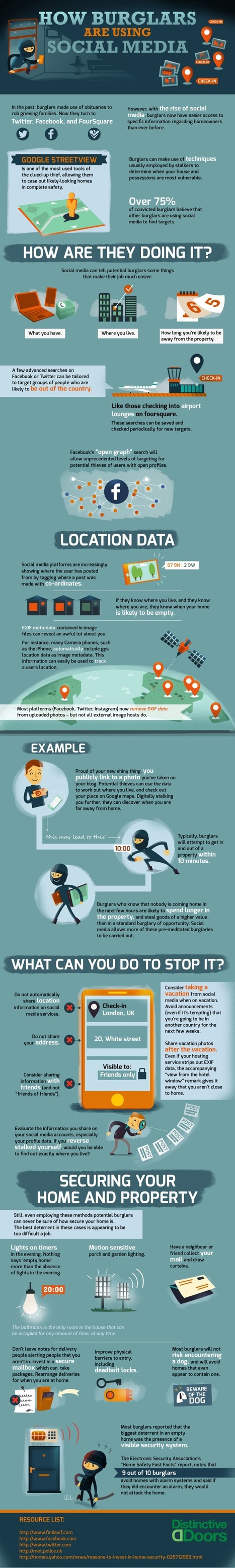













![Do You Know Who’s Watching You? [INFOGRAPHIC] | information analyst | Scoop.it](https://img.scoop.it/4sviZxLmnLcUQr4Dr4vRUTl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)

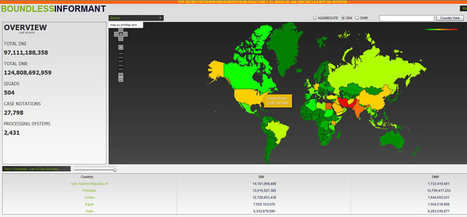
![How to protect your privacy better than CIA director David Petraeus! [Infographic] | information analyst | Scoop.it](https://img.scoop.it/R4a0X05nEZvpjd3GvWBKvDl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)





ChatGPT est victime d’une nouvelle faille de sécurité. En exploitant cette brèche, il est possible d’extraire des données sensibles concernant des individus en s’adressant au chatbot d’OpenAI.
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/topic/21st-century-innovative-technologies-and-developments/?&tag=ChatGPT
https://www.scoop.it/t/21st-century-innovative-technologies-and-developments/?&tag=AI
https://www.scoop.it/topic/21st-century-innovative-technologies-and-developments/?&tag=Ethics