Festplattenverschlüsselung sorgt für sichere Daten bei Diebstahl
Get Started for FREE
Sign up with Facebook Sign up with X
I don't have a Facebook or a X account
| Tags |
|---|
 Your new post is loading... Your new post is loading...
 Your new post is loading... Your new post is loading...
What is the Tor Browser Bundle (TBB)?
The Tor software protects you by bouncing your communications around a distributed network of relays run by volunteers all around the world: it prevents somebody watching your Internet connection from learning what sites you visit, it prevents the sites you visit from learning your physical location, and it lets you access sites which are blocked.
The Tor Browser Bundle lets you use Tor on Windows, Mac OS X, or Linux without needing to install any software. It can run off a USB flash drive, comes with a pre-configured web browser to protect your anonymity, and is self-contained. Learn more.
Gust MEES's insight:
It runs ALSO on a USB-Stick (Memory-Stick) and is NOT dependent on any OS! SO... It runs on any computer where ever you are...
Learn more about PRIVACY:
- http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=Privacy
- http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=PRISM

Cas Van Bakel's curator insight,
April 17, 2018 3:19 AM
Ik heb zelf nog nooit tor gebruikt, dus dit is niet voor mij.
ScanNow for Universal Plug and Play (UPnP)
The free scanner checks whether your network-enabled devices might be vulnerable to attack through the UPnP protocol.
Recent research from Rapid7 revealed that around 40-50 million network-enabled devices are at risk due to vulnerabilities found in the Universal Plug and Play (UPnP) protocol. UPnP enables devices such as routers, printers, network-attached storage (NAS), media players and smart TVs to communicate with each other.
Three groups of security flaws in the protocol are exposing millions of users to remote attacks that could result in the theft of sensitive information or other criminal activity such as spying.
Gust MEES's insight:
One tool more...
Gust MEES's insight:
Looks very interesting, give it a try...
Here a practical application of it on DDOS on the VideoLAN downloads infrastructure
- https://www.youtube.com/watch?feature=player_embedded&v=hNjdBSoIa8k
You've probably all heard of Firesheep by now, a Firefox add-on which lets anyone hijack a user's session to various popular web applications when they're using an open wireless network. While sniffing/stealing session credentials is nothing new, Firesheep exposes this capability to the masses by automating the process so that absolutely no technical know-how is required. Unfortunately, it is actually quite difficult to defend against Firesheep because most sites only permit SSL connections during the initial login, not while surfing other pages. As such, while your username and password are encrypted, your session ID is available to all other machines on the same network.
Gust MEES's insight:
A MUST install when using Public WiFi!!!
Check also:
- https://gustmeesen.wordpress.com/2012/03/16/beginners-it-security-guide/
Was tun, wenn sich ein Virus tief ins System einnistet und Windows verseucht ist? Mit unserem Anti-Virus-USB-Stick rücken Sie der Malware effektiv zu Leibe. Die kostenlosen Spezial-Tools spüren selbst gut versteckte Schädlinge auf.
Scylla is another tool that you can use for penetration testing protocols used by different applications. Scylla works with three basic stages, the pre-hack
Gust MEES's insight:
G Data hat auf der CeBIT in Hannover die neue Generation seiner Sicherheitslösungen vorgestellt.
Die Bochumer Sicherheitsexperten nennen ihre neue Lösung „G Data CloseGap“, den „Lückenschließer“. Die neue Technologie - „made in Germany“ – soll schnell und ressourcenschonend die Lücken im Abwehrring des Computers schließen, die zwischen dem ersten Auftreten eines Schädlings und der Bereitstellung einer entsprechenden Signatur auftreten. CloseGap verbindet hierzu signaturbasierte und proaktive Schutztechnologien (wie BankGuard, WebCloud und BehaviourBlocker), weshalb G Data das Ganze auch als Hybridschutz bezeichnet. So wehrt beispielsweise das ebenfalls neu entwickelte Bankguard-Modul gefährliche Banking-Trojaner signaturunabhängig in Echtzeit ab, wie G Data verspricht.
Gust MEES's insight:
Hört sich vielversprechend an...
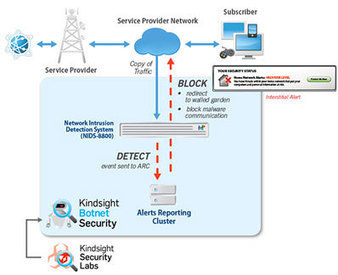
At RSA Conference 2013 Kindsight announced the Kindsight Botnet Security service to help Internet service providers detect botnet activity in the network and protect subscribers against bot infections... The Kindsight NIDS sensor can also block infected devices from communicating with C&C servers, preventing hackers from sending instructions and launching other attacks.
Gust MEES's insight:
That's good news...

Gust MEES's comment,
March 7, 2013 3:41 PM
Hi Jetmir, please check ===> http://www.slideshare.net/solvitor/annotum-scholarly-publishing-platform + ===> http://www.scoop.it/t/wordpress-annotum-for-education-science-journal-publishing?tag=Wordpress+Plugin+Creates+Online+School Hope that helps ;) have a great day :)

Gust MEES's comment,
March 7, 2013 3:55 PM
Hi Jetmir, check out also ===> http://www.scoop.it/t/wordpress-annotum-for-education-science-journal-publishing

Gust MEES's comment,
March 7, 2013 5:28 PM
Hi Jetmir, take also a look at DOKEOS ===> http://dokeos.com/ Let me know later, please about what You think about them. Thanks...
Gust MEES's insight:
Great tools...
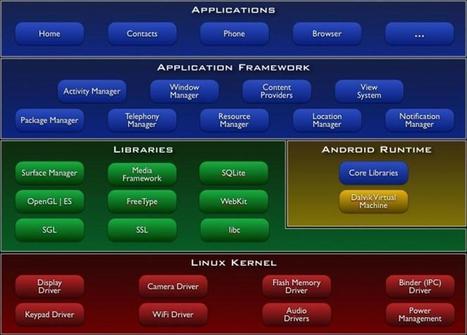
Android, as we are all aware, is a Linux-based operating system which was initially developed by Android Inc. and was later purchased by Google. It was designed for touch screen devices like smartphones, tablets, cameras, set-top boxes, etc… and has reached the hands of millions of consumers. Over a period of time, operating systems like Windows and Linux have matured against threats, thereby diverting the hackers towards newer targets like handheld devices. Millions of Android applications are downloaded from the Google Play store by users, thereby exposing end users’ email ids, banking details, sensitive details and messaging content due to insecure coding practices. The users are either unaware or trust the apps to protect their sensitive data against theft. Via Frederic GOUTH
Gust MEES's insight:
Check it out...
Sécurité PC et Internet/sources d'information Sécurité PC et Internet/sources d'information Apprentissage à la sécurité (domestique) PC et Internet, les meilleurs adresses Internet pour se renseign...
Gust MEES's insight:
Find BEST links in English, French and German to get the MOST information out about Cyber-Security and HOWTO protect you!

Gust MEES's curator insight,
February 12, 2013 11:15 AM
Find BEST links in English, French and German to get the MOST information out about Cyber-Security and HOWTO protect you! |
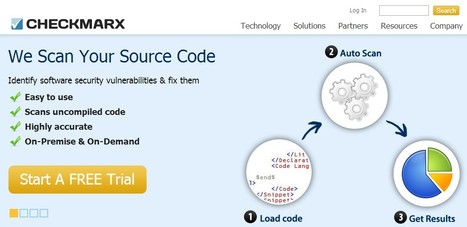
Checkmarx is a leading provider of code analysis tools, static code analysis, software code analysis, and other software that enable application developers to make flawless applications and provide solutions aligned with best practices of the...
Gust MEES's insight:
Check it out...
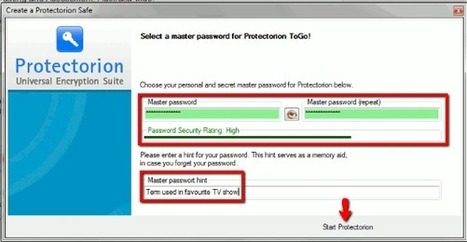
Do you ever worry what would happen if your files fell into the wrong hands, especially those files that you kept on your external flash drive? Thankfully there are many options to encrypt sensitive data. Protectorion ToGo is one such application. While the free version is meant for private use only, it does allow you to encrypt up to two external devices. An added bonus is that the application is compatible with Windows XP/Vista/7/8 (32bit + 64bit). Via Frédéric DEBAILLEUL, Gust MEES
Gust MEES's insight:

Gust MEES's curator insight,
June 2, 2013 6:22 AM
A MUST 4 everyone!!! Learn more:
- http://www.scoop.it/t/ict-security-tools

173 Sud's curator insight,
June 2, 2013 9:01 AM
The free version of Protectorion is limited, as you can only encrypt two external drives and it is for personal use only.
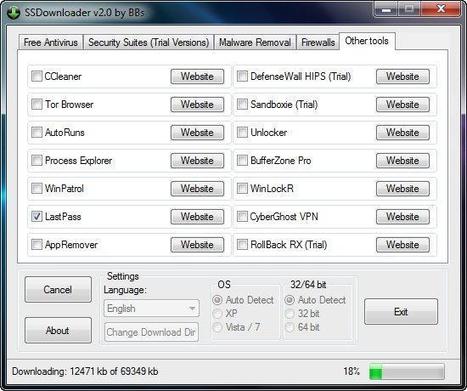
SSDownloader or Security Software Downloader is a small, easy to use download manager specially designed for security software.
Gust MEES's insight:

Gust MEES's curator insight,
May 21, 2013 4:38 PM
Check also:
- http://www.scoop.it/t/ict-security-tools
Is your system slower and less efficient than it was before? YooApplications presents Sweepi, a free tool that will help you solve this problem and protect your privacy.
Gust MEES's insight:
I recommend it as I use it already since its creation, ages ago!!!
It erases also parts of the HardDisk...
Windows ONLY.

Gust MEES's curator insight,
April 30, 2013 8:19 AM
I recommend it as I use it already since its creation, ages ago!!!
It erases also parts of the HardDisk...
Windows ONLY.
Mit dem FreedomStick können Sie nahezu anonym im Internet surfen.
Gust MEES's insight:
Anonymität und Privacy im Internet...
StreamArmor is the sophisticated tool for discovering hidden alternate data streams (ADS) as well as clean them completely from the system.
Gust MEES's insight:
StreamArmor is the standalone, portable application which does not require any installation. 
Gust MEES's comment,
April 10, 2013 6:17 PM
Hi Amigo Omega's, who are You!? Is YOUR voice bigger & is YOUR professional experience BIGGER & BETTER than other prodessional ones!? Let me know ;) BUT with a detailed report & NOT with a simple comment 4 getting known :(((
From the creators of BackTrack comes Kali Linux, the most advanced and versatile penetration testing distribution ever created. BackTrack has grown far beyond its humble roots as a live CD and has now become a full-fledged operating system. With all this buzz, you might be asking yourself
Gust MEES's insight:
From the creators of BackTrack comes Kali Linux, the most advanced and versatile penetration testing distribution ever created. BackTrack has grown far beyond its humble roots as a live CD and has now become a full-fledged operating system. With all this buzz, you might be asking yourself...
From
github
honeymap - jQuery frontend and node.js/socket.io backend for displaying a realtime websocket stream of GPS data on a jVectorMap world map
Gust MEES's insight:
Check also this application:
- http://www.scoop.it/t/securite-pc-et-internet?tag=Overview+of+current+cyber+attacks
At RSA Conference 2013, Qualys has expanded its popularFreeScan service to support scanning internal and external systems and web applications and also added new security and compliance audits for Patch Tuesday vulnerabilities, OWASP threats and SCAP Configuration.
Read more, very interesting...
Gust MEES's insight:
The SC Labs team reported on the strengths and weaknesses of some of the leading vulnerability assessment tools on the market.
Gust MEES's insight:
A great list of great tools...
Universal Plug and Play has always had security holes. Here's how to plug them.
Gust MEES's insight:
|


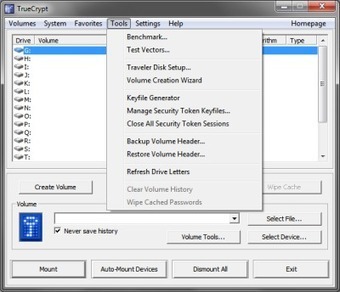

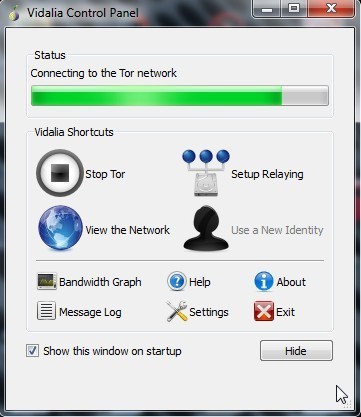










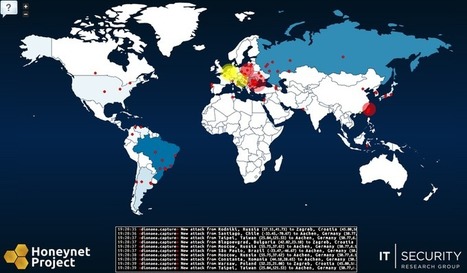
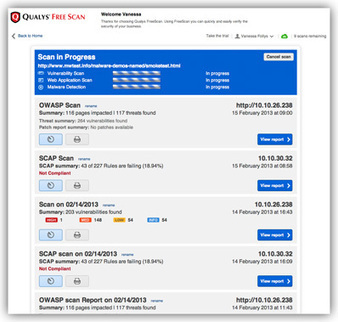
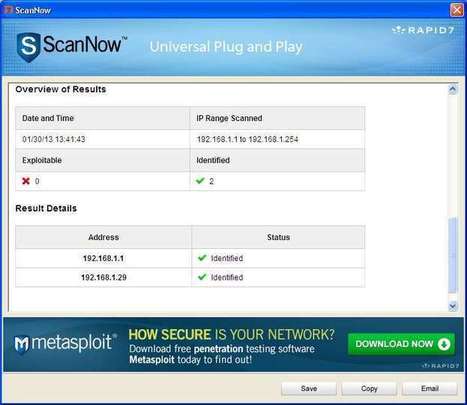





Learn more:
- http://www.scoop.it/t/ict-security-tools
- http://www.scoop.it/t/ict-security-tools/?tag=Encryption