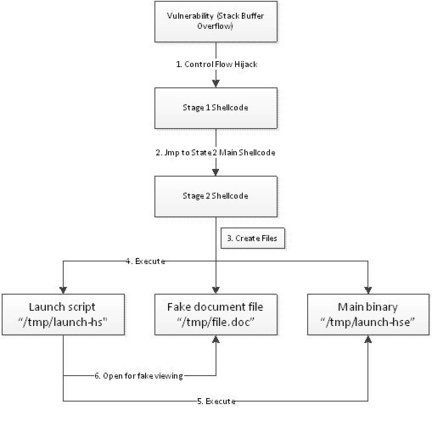
.. . For most people it is very difficult to understand IT-Security and also the need to apply it…. To me it looks sometimes like that people see a computer as a modern typewriter and/or a game console, but that’s not the case, I will try to explain to you a computer in a visual manner so that you might able to understand better why there is a need to protect your computer and also why a computer is in danger to get a virus, trojan, and other malware infections.
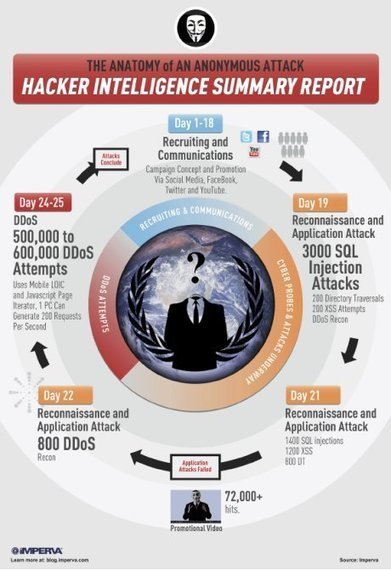
Why a computer could become a possible Cyber-Weapon who is attacking web-sites and perhaps also your Government’s web-sites!
Read more:
Via Gust MEES



 Your new post is loading...
Your new post is loading...