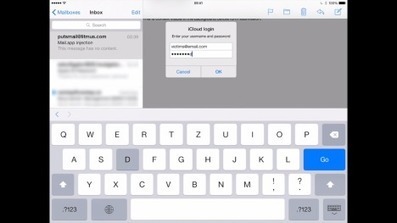
Der Sicherheitsexperte Jan Soucek hat einen äußerst gefährlichen Bug in der E-Mail-App von Apples iOS entdeckt. Ein Angreifer kann darüber eine Fake-Abfrage der Apple-ID einblenden - und so das Passwort abgreifen.
CHIP Online meint:
Auch wenn nicht jeder glücklich darüber sein dürfte, dass Soucek seinen Programm-Code mit der Veröffentlichung auch möglichen Angreifern bereitstellt, trifft die eigentliche Schuld Apple. Es ist eine äußerst fragwürdige Politik, eine Sicherheitslücke derartigen Ausmaßes einfach ein halbes Jahr zu ignorieren. Hier muss Apple nun unbedingt in kürzester Zeit nachbessern - spätestens mit der Veröffentlichung von iOS 8.4 Ende Juni.
Mehr erfahren/ Learn more:
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security



 Your new post is loading...
Your new post is loading...













CHIP Online meint:
Auch wenn nicht jeder glücklich darüber sein dürfte, dass Soucek seinen Programm-Code mit der Veröffentlichung auch möglichen Angreifern bereitstellt, trifft die eigentliche Schuld Apple. Es ist eine äußerst fragwürdige Politik, eine Sicherheitslücke derartigen Ausmaßes einfach ein halbes Jahr zu ignorieren. Hier muss Apple nun unbedingt in kürzester Zeit nachbessern - spätestens mit der Veröffentlichung von iOS 8.4 Ende Juni.
Mehr erfahren/ Learn more:
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security