 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
|
Neues Passwort-Problem in MacOS High Sierra
MacOS High Sierra hat erneut ein Problem: Nun ist bekannt geworden, dass die Einstellungen für den eingebauten App Store ohne korrektes Passwort geändert werden können.
In der aktuellen Version von MacOS High Sierra können die Einstellungen im App-Store-Menü in den Systemeinstellungen mit einem beliebigen Passwort geändert werden. Dies zeigt ein Bugreport auf Open Radar. Die Sicherheitslücke ist indes nicht so gravierend wie die passwortlose Root-Anmeldung unter MacOS High Sierra und erfordert einen Administrator-Account. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
MacRumors spotted a bug report that affects the current version of macOS High Sierra. In System Preferences, you can unlock the App Store preference pane by typing any password. Apple has reportedly already fixed the bug in beta versions of the next macOS High Sierra update.
While this bug is nowhere as serious as the infamous root login bug, as John Gruber wrote, this one is quite embarrassing. What’s wrong with password prompts and macOS?
If you want to test this bug at home, I was able to reproduce it quite easily. Open System Preferences, go to the App Store settings and look at the padlock icon. If it’s unlocked, lock it first and then try unlocking it with any password. Ta-da!
You can enable or disable automatic downloads and installation of app and operating system updates using this preference pane. This doesn’t represent an immediate security risk. But if someone already has access to your computer, they could disable automatic security updates and take advantage of vulnerabilities that are regularly patched.
By default, App Store settings are unlocked for admin users. But if you’re a bit paranoid about security, chances are you locked down all your system settings to make sure nobody is playing with them.
More importantly than the bug itself, Apple should reconsider their quality assurance processes. It’s time to stop shipping updates with embarrassing bugs. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
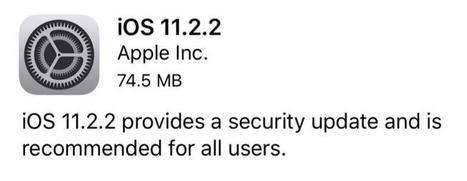
Another day, another patch to install. This time, it's iOS 11.2.2 for iPhone, iPad, and iPod touch.
Must read: How to tell if your iPhone battery needs replacing
The patch is to fix the Spectre vulnerability that came to light earlier this month.
Apple describes the patch as follows:
iOS 11.2.2 includes security improvements to Safari and WebKit to mitigate the effects of Spectre (CVE-2017-5753 and CVE-2017-5715).
Apple says it "recommends" the update "for all users."
To download the update, go to Settings > General > Software Update (the preferred way, and this way the patch is only about 75MB), or connect your iPhone to a computer running iTunes and then carry out the update (this is slower and downloads the entire iOS 11.2.2 package, which is several gigabytes, as opposed to just the smaller update). Learn more / en savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
05.01.2018 - 01:50 Uhr
Durch eine massive Sicherheitslücke in den Computerchips von Milliarden Geräten können auf breiter Front vertrauliche Daten abgeschöpft werden.
Jetzt hat Apple bestätigt, dass auch „alle Mac-Systeme und iOS-Geräte betroffen sind“. Im Klartext: Jeder Apple-Computer, jedes iPhone und jedes iPad könnte von Hackern angegriffen werden. Bislang seien aber keine solche Attacken bekannt, erklärt Apple in einem Hilfe-Dokument.
Was müssen Besitzer von Apple-Geräten wissen?
Nach Angaben des Unternehmens wurde eines der beiden möglichen Angriffsszenarien („Meltdown“) bereits mit Aktualisierungen seiner Betriebssysteme abgestellt. Auf Geräten, die mit iOS 11.2, MacOS 10.13.2 bzw. tvOS 11.2 arbeiten, soll diese Angriffsmöglichkeit nicht mehr möglich sein.
Mit einem Update für den Internet-Browser Safari solle in den nächsten Tagen auch das Angriffsszenario „Spectre“ verhindert werden. Die Apple Watch ist laut Apple nicht von der Sicherheitslücke betroffen, benötigt daher keine Aktualisierung.
Apple empfiehlt außerdem dringend, Apps oder Programme ausschließlich aus sicheren Quellen wie dem eigenen App-Store zu laden. Andernfalls laufe man Gefahr, gefährliche Spionagesoftware aufs eigene Gerät zu holen. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Meltdown+and+Spectre+Attacks https://gustmeesde.wordpress.com/2014/12/26/programme-die-auf-jeden-neuen-pc-und-smartphones-gehoren/ https://gustmeesde.wordpress.com/2014/12/16/browser-sind-das-einfallstor-fur-malware-sind-eure-browser-up-to-date/

|
Scooped by
Gust MEES
|
A researcher that goes by the handle “Siguza” released details of a local privilege escalation attack against macOS that dates back to 2002. A successful attack could give adversaries complete root access to targeted systems. Siguza released details of the attack on Dec. 31 via Twitter, wishing followers a “Happy New Year” and linked to a technical write-up outlining the research. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security/?&tag=LPE+Exploit

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Blamable Woche für Apple: Mehrere Fehler in seinen Betriebssystemen zwingen das Unternehmen zu schnellen Updates – und die Kunden zu Wachsamkeit. Vier recht peinliche Software-Fehler in nur einer Woche also. Die Zahl der konkret Betroffenen ist zwar möglicherweise nicht besonders hoch. Aber angesichts der enormen Verbreitung von Apple-Hardware ist das Unternehmen immer gezwungen, schnell Updates zu entwickeln und auf die riesige Nutzerbasis zu verteilen, stets unter medialer Beobachtung.
Außerdem ist Apple längst nicht mehr nur Hardware-Hersteller, auch wenn es mitunter noch so wahrgenommen wird. Software und Dienste gehören aber genauso zu seinem Ökosystem, und beide haben nicht erst seit dieser Woche einen deutlich schlechteren Ruf als die Geräte, auf denen sie laufen.
Das Unternehmen wirbt aber gern damit, dass seine Produkte besonders sicher seien und sich besonders leicht bedienen ließen. Und so muss es sich wohl auch an seinen Werbesprüchen messen lassen. Einer lautet zurzeit: "Anything you can do, you can do better."
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security/?&tag=Root https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
The patch that Apple rushed out yesterday to fix the root access flaw in macOS brings with it problems of its own. Fortunately, this new bug is quite easy to fix. The patch that Apple released to fix the "root" security flaw discovered in the latest release of macOS High Sierra is causing problems for some users. Must read: How strong are iPhone X sales? The patch - which Apple rushed out in less than 24 hours - can cause file sharing to stop working for some users, according to a support document published by Apple. The fix itself is pretty straightforward, although does require users to be familiar with using Terminal: - Open the Terminal app (which is in the Utilities folder of the Applications folder)
- Type sudo /usr/libexec/configureLocalKDC and press Return
- Enter your administrator password when requested and press Return
- Quit the Terminal app
Note that this fix is only for the file sharing bug caused by Security Update 2017-001 for macOS High Sierra 10.13.1. If you're running a different version, this patch isn't for you. It's likely that Apple will push a patch for this bug as part of the macOS High Sierra 10.13.2 update. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
At first, the Twitter user who publicised this flaw was criticised by some people, who considered his tweet to be “irresponsible disclosure”, because it told the world about a problem that it might have been better to tell Apple about privately first so the hole could be closed and then announced.
But others soon realised that this was not a brand new discovery – indeed, it had been discussed more than two weeks ago on Apple’s on support forum.
Apple’s official policy of saying nothing about security issues until a fix is out meant that there wasn’t much to go on once the news broke, except to assume that the company was frantically coding up a fix…
…and, fortunately that turns out to have been true. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
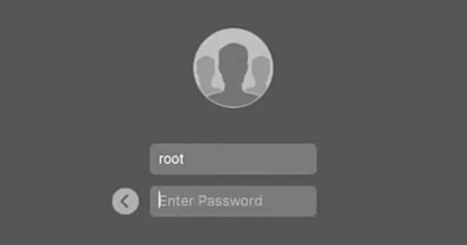
Une incroyable faille de sécurité permet d'accéder à un appareil sous macOS High Sierra sans le moindre effort en rentrant simplement le nom d'utilisateur "root".
Une énorme faille de sécurité permet de pénétrer dans d’importe quel appareil sous macOS High Sierra et cela sans le moindre effort. La démarche est on ne peut plus simple. Lorsque le système d’exploitation demande une autorisation d’accès avec un mot de passe et un identifiant, il suffit de rentrer le nom d’utilisateur « root » puis de cliquer plusieurs fois sur le bouton d'accès et comme par magie la machine accepte l'opération.
Cette faille a été découverte Lemi Orhan Ergin, le fondateur de Software Craftsmanship Turkey. Il a tweeté l’information à Apple qui travaille déjà sur un correctif. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
Want to have god-like powers over a Mac? Just enter your username as root... no password required. But an attacker needs to have physical access to a Mac computer in order to exploit this flaw?Not so fast. For instance, security researcher Patrick Wardle reports that it is possible to exploit the flaw remotely. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
In software, there are bugs, and there are dangerous bugs. It looks like macOS High Sierra has one of those dangerous bugs; one that could give someone full access to virtually any user account. And holy buckets, it is scary. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
THERE ARE HACKABLE security flaws in software. And then there are those that don't even require hacking at all—just a knock on the door, and asking to be let in. Apple's macOS High Sierra has the second kind.
On Tuesday, security researchers disclosed a bug that allows anyone a blindingly easy method of breaking that operating system's security protections. Anyone who hits a prompt in High Sierra asking for a username and password before logging into a machine with multiple users, they can simply type "root" as a username, leave the password field blank, click "unlock" twice, and immediately gain full access.
In other words, the bug allows any rogue user that gets the slightest foothold on a target computer to gain the deepest level of access to a computer, known as "root" privileges. Malware designed to exploit the trick could also fully install itself deep within the computer, no password required. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security
|

|
Scooped by
Gust MEES
|
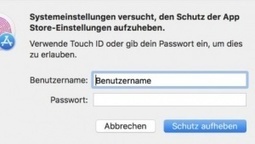
Un utilisateur d’Open Radar a découvert un petit souci dans macOS 10.13.2. Il permet à un administrateur local de modifier les préférences systèmes du Mac App Store en saisissant n’importe quel mot de passe.
Sale temps pour la sécurité sur macOS. Le dernier bug de sécurité en date n’est pas du niveau des précédents mais fait malgré tout un peu tache sur le CV d’Apple. Un utilisateur d’Open Radar, une communauté de rapporteurs de bugs, a révélé un petit souci dans macOS High Sierra 10.13.2, la dernière version officiellement disponible.
Ainsi, selon lui, n’importe quel utilisateur administrateur local sur la machine peut ouvrir le panneau des Préférences Système du Mac App Store et déverrouiller le cadenas qui empêche les modifications de ces réglages en saisissant n’importe quel mot de passe. Si le cadenas est déjà ouvert et que cet utilisateur souhaite tenter sa chance, c’est possible. Il suffit de le refermer, de l’ouvrir à nouveau et de taper n’importe quelle suite de lettres ou chiffres. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
A bug has been discovered in macOS 10.13.2 that allows you to unlock the App Store system preferences using any username and password as long as you are logged in as a local admin. This means that if your account is an admin and you leave the computer unattended, anyone can change the App Store settings on the Mac without your knowledge.
While this is not as serious as the recent bug that allowed you to gain macOS root access by entering no password repeatedly, it does show that there are some serious code auditing issues in macOS regarding how passwords can be used. This is twice now in as little as three months that the password field was able to be used in macOS to gain extra privileges.
As shown in the video above, using this bug is really simple. Just open up the App Store system preferences and if the little padlock icon is locked, click on it. macOS will then prompt you for a username and password. Enter any username and password you want and press Unlock and the App Store system preferences will become unlocked. This allows you to change settings such as what updates to install, whether to install security updates, and more.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
If you own any Apple products, you're going to want to make sure you have the latest updates installed.
Apple just released two incredibly important security updates for iOS and MacOS, which address the massive Spectre vulnerability Apple previously said affects all Macs and iPhones.
SEE ALSO: Apple on Meltdown and Spectre bugs: 'All Mac systems and iOS devices are affected'
The updates, 11.2.2 for iOS and 10.13.2 for macOS High Sierra, are available now for iPhones, iPads, and Macs.
Spectre was one of two major CPU vulnerabilities revealed by security researchers last week that affects devices with processors from major chip makers, including Intel, AMD, and ARM. Apple previously released software updates to address the other flaw, Meltdown.
While it's always a good idea to keep your software up to date, these latest updates are especially important. As security researchers have warned, the Meltdown and Spectre bugs are particularly nasty. So even if you're the type to wait days, or even weeks, to update to the latest software, you really shouldn't waste any time with these updates.
Google and Microsoft also previously released software updates to address the issue. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Meltdown+and+Spectre+Attacks https://gustmeesde.wordpress.com/2014/12/26/programme-die-auf-jeden-neuen-pc-und-smartphones-gehoren/ https://gustmeesde.wordpress.com/2014/12/16/browser-sind-das-einfallstor-fur-malware-sind-eure-browser-up-to-date/

|
Scooped by
Gust MEES
|
Un chercheur en sécurité a découvert une faille importante datant au moins de 2002. Depuis quelques mois Apple enchaîne les vulnérabilités sur son système d’exploitation.
La faille aurait beau avoir plus de quinze ans, elle n’en donne pas moins accès à tout le contrôle de macOS. C’est la découverte réalisée par le chercheur en sécurité Siguza qui a dévoilé la chose sur Twitter et GitHub. Cette vulnérabilité zero-day concerne directement le kernel de l’OS d’Apple. Consolation pour les potentielles victimes, il faut toutefois avoir accès à la machine pour pouvoir l’exploiter.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security/?&tag=LPE+Exploit https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
Mit "Apple iCloud für Windows" können Sie persönliche Dokumente, Mails, Fotos und Termine zwischen Apple-Geräten wie iPhone oder iPad und Windows-PC synchronisieren.
Apple hat für seine Software "iCloud für Windows" ein außerplanmäßiges Update auf Version 7.2 veröffentlicht, das gleich mehrere Sicherheitslücken schließt.
Das Bundesamt für Sicherheit in der Informationstechnik (BSI) stuft die Sicherheitslücken auf seiner fünf-stufigen Skala mit Risikostufe 4 ("hoch") ein und empfiehlt allen iPhone- oder iPad-Nutzern mit Windows-PCs das Programm möglichst schnell zu updaten:
Apple behebt mit einem Sicherheitsupdate für iCloud für Windows mehrere Sicherheitslücken, die von einem Angreifer aus dem Internet ausgenutzt werden können, um beliebige Aktionen auf Ihrem Gerät auszuführen und private Informationen über Sie zu sammeln.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
Last week was a really bad week for Apple, with both iOS and macOS falling victim to high profile bugs.
I won't bore you with the details, but the TL:DR of the headaches that Apple -- and more importantly, Apple's customers -- encountered was as follows:
A serious -- and very stupid -- root bug was uncovered in macOS.
The patch that Apple pushed out for the root bug broke file sharing for some.
Updating macOS to 10.13.1 after installing the root patch rolled back the root bug patch.
iOS 11 was hit by a date bug that caused devices to crash when an app generated a notification, forcing Apple to prematurely release iOS 11.2
Stuff happens, I get it.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security/?&tag=Root https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
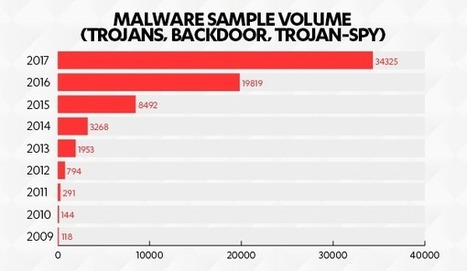
In den ersten drei Quartalen des Jahres 2017 stieg die Zahl der Malware-Angriffe auf Macs um über 70 % und die PUA (potenziell unerwünschte Anwendungen wie z.B. Adware) um 50 % gegenüber dem Vorjahr (Quelle: F-Secure Labs). Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
Die von Apple schnell ausgelieferte Aktualisierung für macOS 10.13 kann die Dateifreigabe lahmlegen. Inzwischen hat der Mac-Hersteller bei dem Sicherheits-Update nochmals nachgebessert – das File-Sharing-Problem aber offenbar nicht ausgeräumt.
Das wichtige Sicherheits-Update 2017-001 für macOS High Sierra führt unter Umständen zu Problemen bei der Dateifreigabe: Nach der Installation des Updates, das Apple inzwischen auch automatisch einspielt, funktioniert der entfernte Zugriff auf die per File Sharing geteilten Verzeichnisse des Macs nicht länger, wie Nutzer berichten.
Workaround bei Dateifreigabe-Problem in High Sierra
Apple ist der Fehler bekannt, das Unternehmen hat bereits einen manuellen Workaround veröffentlicht: Nutzer sollen im Terminal
sudo /usr/libexec/configureLocalKDC
eingeben und den Befehl ausführen, so Apple – dafür ist die Eingabe des Admin-Passwortes vonnöten. Dies repariere die Dateifreigabe.
Apple bessert bei Sicherheits-Update nach
Offenbar hat Apple bei dem Security-Update 2017-001 inzwischen nachgebessert und – ohne weiteren Hinweis – eine neue Fassung veröffentlicht, die nun auch für macOS 10.13.0 gedacht ist. Zuvor wurde noch macOS 10.13.1 vorausgesetzt. Nach der Installation zeigt die Neufassung die Build-Nummer 17B1003, bei der ersten Version war es noch 17B1002. Die neue Fassung scheint aber ein für Unterstützung der ersten öffentlichen High-Sierra-Version zu sorgen, das Dateifreigabenproblem kann offenbar weiterhin auftreten.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
Apple released a security update Wednesday to fix a major bug that allowed anyone to bypass security protocols and act as a computer's administrator.
"Security is a top priority for every Apple product, and regrettably we stumbled with this release of macOS," a spokesperson for Apple said in a statement. "When our security engineers became aware of the issue Tuesday afternoon, we immediately began working on an update that closes the security hole."
The security issue impacted macOS High Sierra 10.13.1. Apple says the update is now available for download and will be rolled out automatically to all systems running the affected software.
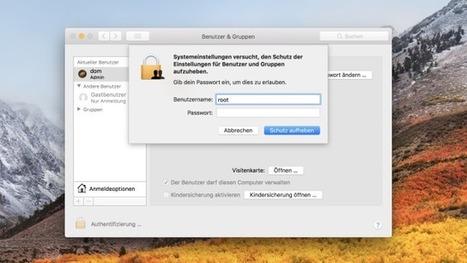
On Tuesday, developers noticed that someone with access to a Mac computer running Apple's most recent Mac software could type "root" and no password in the Users & Groups section of System Preferences and gain administrator-level access to the computer.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
In der aktuellen macOS-Version High Sierra steckt eine Sicherheitslücke, die Beobachter sprachlos macht: Mit wenigen Klicks können Angreifer sich root-Rechte verschaffen - weil Apple dafür kein Passwort verlangt.
Schon vor einigen Wochen fiel macOS High Sierra, die aktuelle Version des Apple-Betriebssystems, durch einen abstrusen Bug auf: Das Passwort verschlüsselter Festplatten kopierte das Betriebssystem kurzerhand in den Passwort-Hinweis und machte es damit für jeden sichtbar. Wer damals dachte, viel schlimmer kann es nicht kommen, hat sich getäuscht: In einer jetzt entdeckten Sicherheitslücke verlangt Apple an kritischen Punkten einfach überhaupt kein Passwort mehr. Angreifer können sich mit wenigen Klicks vollen Zugriff auf den Computer sichern.
Öffentlich wurde der eklatante Bug durch einen Tweet. Der Entwickler Lemi Orhan Ergin beschreibt darin das Vorgehen, mit dem sich Dritte auf einem Mac root-Rechte verschaffen können, ohne dafür ein Passwort zu benötigen. Mit diesen Rechten ist es möglich, den Mac vollständig zu übernehmen.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
What’s the maddest, baddest, craziest, can-you-believe-it, how-did-that-happen security blunder of recent memory?
Companies contending for the top three spots in the past quarter surely include:
Uber. Suffered a breach, paid the hackers off, pretended it never happened, got found out anyway.
Equifax. Personal data including social security numbers for about half of US adults carried off by crooks.
Apple. When connecting an encrypted device, [Show password hint] would reveal the password itself.
Well, Apple just did it again, and this one is even worse that before – so Cupertino may well be back in first place.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
Update: Apple has acknowledged the issue and is working on it. Statement and workaround below.
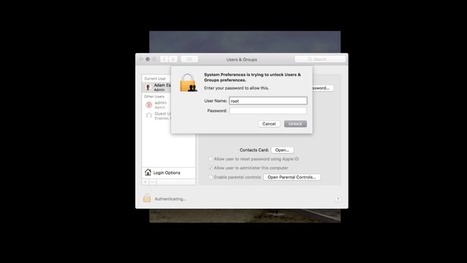
Wow, this is a bad one. On Macs running the latest version of High Sierra — 10.13.1 (17B48) — it appears that anyone can log in just by putting “root” in the user name field. This is a huge, huge problem. Apple will fix it probably within hours, but holy moly. Do not leave your Mac unattended until this is resolved.
The bug is most easily accessed by going to Preferences and then entering one of the panels that has a lock in the lower left-hand corner. Normally you’d click that to enter your user name and password, which are required to change important settings like those in Security & Privacy.
No need to do that any more! Just enter “root” instead of your user name and hit enter. After a few tries, it should log right in. There’s no need to do this yourself to verify it. Doing so creates a “root” account that others may be able to take advantage of if you don’t disable it. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security
|



 Your new post is loading...
Your new post is loading...






















Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security