 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
|
We knew that other companies were recording interactions with their smart devices, and using some of those recordings to check for quality by having real people listen to those interactions. But, until now, we thought Apple was different.
On Friday Apple confirmed, to the Guardian, a whistleblowers account that the company has similar practices to Google and Amazon, but never disclosed that fact in its privacy policy.
Apple samples a small number of recordings of interactions with its voice assistant Siri, which is used by millions of Americans on their iPhones, Apple Watch, and other iOS and Mac devices. According to the whistleblower, that includes "countless instances of recordings featuring private discussions between doctors and patients, business deals, seemingly criminal dealings, sexual encounters and so on."
I accidentally wake up Siri all the time on my watch or phone when I have no intention of interacting with her, and I've never given any thought to the fact that she's listening to whatever goes on in the background. In fact, we have a daughter whose name apparently sounds close enough to "hey Siri," that I'm frequently reminded by my iPhone that "you need to clean up your room," and "come set the table," are not commands yet supported by voice assistants (though that would be awesome). Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security/?&tag=Privacy http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security/?tag=SIRI

|
Scooped by
Gust MEES
|
Beware! A new bug can crash iOS and macOS with a single text message
RESIST THE TEMPTATION TO SEND THIS TEXT BOMB TO ANYONE.
Be careful what you click on.
Abraham Masri, a Twitter user with the rather wonderful handle of @cheesecakeufo, has shared publicly a malicious link that is capable of crashing iOS and macOS when received through Apple's Messages app.
The link, which I'm only going to reproduce here as an image, points to a GitHub page.
Clicking on the link can cause your Messages application to crash on iOS and Mac devices, and you may find other peculiar behaviour occurs such as being returned to your lock screen.
It turns out that there's some pretty funky-looking code on that webpage.
Something about the so-called ChaiOS bug's code gives your Apple device a brainstorm. Ashamed about the mess it gets itself in, Messages decides the least embarrassing thing to do is to crash.
Nasty. But, thankfully, more of a nuisance than something that will lead to data being stolen from your computer or a malicious hacker being able to access your files.
Readers with long memories will recall that Apple users have been bedevilled by text bomb vulnerabilities like this in the past. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
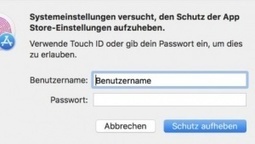
Un utilisateur d’Open Radar a découvert un petit souci dans macOS 10.13.2. Il permet à un administrateur local de modifier les préférences systèmes du Mac App Store en saisissant n’importe quel mot de passe.
Sale temps pour la sécurité sur macOS. Le dernier bug de sécurité en date n’est pas du niveau des précédents mais fait malgré tout un peu tache sur le CV d’Apple. Un utilisateur d’Open Radar, une communauté de rapporteurs de bugs, a révélé un petit souci dans macOS High Sierra 10.13.2, la dernière version officiellement disponible.
Ainsi, selon lui, n’importe quel utilisateur administrateur local sur la machine peut ouvrir le panneau des Préférences Système du Mac App Store et déverrouiller le cadenas qui empêche les modifications de ces réglages en saisissant n’importe quel mot de passe. Si le cadenas est déjà ouvert et que cet utilisateur souhaite tenter sa chance, c’est possible. Il suffit de le refermer, de l’ouvrir à nouveau et de taper n’importe quelle suite de lettres ou chiffres. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
MacRumors spotted a bug report that affects the current version of macOS High Sierra. In System Preferences, you can unlock the App Store preference pane by typing any password. Apple has reportedly already fixed the bug in beta versions of the next macOS High Sierra update.
While this bug is nowhere as serious as the infamous root login bug, as John Gruber wrote, this one is quite embarrassing. What’s wrong with password prompts and macOS?
If you want to test this bug at home, I was able to reproduce it quite easily. Open System Preferences, go to the App Store settings and look at the padlock icon. If it’s unlocked, lock it first and then try unlocking it with any password. Ta-da!
You can enable or disable automatic downloads and installation of app and operating system updates using this preference pane. This doesn’t represent an immediate security risk. But if someone already has access to your computer, they could disable automatic security updates and take advantage of vulnerabilities that are regularly patched.
By default, App Store settings are unlocked for admin users. But if you’re a bit paranoid about security, chances are you locked down all your system settings to make sure nobody is playing with them.
More importantly than the bug itself, Apple should reconsider their quality assurance processes. It’s time to stop shipping updates with embarrassing bugs. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
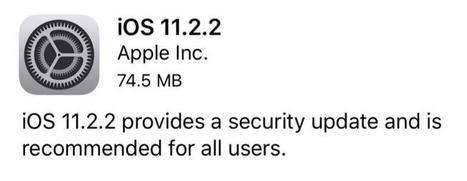
Another day, another patch to install. This time, it's iOS 11.2.2 for iPhone, iPad, and iPod touch.
Must read: How to tell if your iPhone battery needs replacing
The patch is to fix the Spectre vulnerability that came to light earlier this month.
Apple describes the patch as follows:
iOS 11.2.2 includes security improvements to Safari and WebKit to mitigate the effects of Spectre (CVE-2017-5753 and CVE-2017-5715).
Apple says it "recommends" the update "for all users."
To download the update, go to Settings > General > Software Update (the preferred way, and this way the patch is only about 75MB), or connect your iPhone to a computer running iTunes and then carry out the update (this is slower and downloads the entire iOS 11.2.2 package, which is several gigabytes, as opposed to just the smaller update). Learn more / en savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
Apple just released iOS 11.2.2 with some Safari and WebKit improvements to mitigate the Spectre vulnerability. macOS is also receiving an update. It’s a supplemental update to macOS High Sierra 10.13.2 and it includes the same fix.
As always, you should update your devices with the latest security patches. In this case, Meltdown and Spectre are serious vulnerabilities. With Meltdown, a malicious application running on an unpatched device can read the unencrypted kernel memory. You don’t want anyone to grab your password and private encryption keys.
Meltdown was already addressed in previous updates. iOS 11.2, macOS 10.13.2 and tvOS 11.2 already included mitigations for Meltdown. Apple Watch chips aren’t affected by Meltdown.
Spectre isn’t as serious as it only breaks the isolation between multiple applications. But it can be exploited using JavaScript in a web browser. That’s why it’s important to fix it before somebody figures out how to distribute malicious JavaScript code in an ad unit.
On your iPhone or iPad, head over to the Settings app, then tap on General and Software Update. On your Mac, open the Mac App Store and check for updates. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security/?&tag=LPE+Exploit https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
05.01.2018 - 01:50 Uhr
Durch eine massive Sicherheitslücke in den Computerchips von Milliarden Geräten können auf breiter Front vertrauliche Daten abgeschöpft werden.
Jetzt hat Apple bestätigt, dass auch „alle Mac-Systeme und iOS-Geräte betroffen sind“. Im Klartext: Jeder Apple-Computer, jedes iPhone und jedes iPad könnte von Hackern angegriffen werden. Bislang seien aber keine solche Attacken bekannt, erklärt Apple in einem Hilfe-Dokument.
Was müssen Besitzer von Apple-Geräten wissen?
Nach Angaben des Unternehmens wurde eines der beiden möglichen Angriffsszenarien („Meltdown“) bereits mit Aktualisierungen seiner Betriebssysteme abgestellt. Auf Geräten, die mit iOS 11.2, MacOS 10.13.2 bzw. tvOS 11.2 arbeiten, soll diese Angriffsmöglichkeit nicht mehr möglich sein.
Mit einem Update für den Internet-Browser Safari solle in den nächsten Tagen auch das Angriffsszenario „Spectre“ verhindert werden. Die Apple Watch ist laut Apple nicht von der Sicherheitslücke betroffen, benötigt daher keine Aktualisierung.
Apple empfiehlt außerdem dringend, Apps oder Programme ausschließlich aus sicheren Quellen wie dem eigenen App-Store zu laden. Andernfalls laufe man Gefahr, gefährliche Spionagesoftware aufs eigene Gerät zu holen. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Meltdown+and+Spectre+Attacks https://gustmeesde.wordpress.com/2014/12/26/programme-die-auf-jeden-neuen-pc-und-smartphones-gehoren/ https://gustmeesde.wordpress.com/2014/12/16/browser-sind-das-einfallstor-fur-malware-sind-eure-browser-up-to-date/

|
Scooped by
Gust MEES
|
A researcher that goes by the handle “Siguza” released details of a local privilege escalation attack against macOS that dates back to 2002. A successful attack could give adversaries complete root access to targeted systems. Siguza released details of the attack on Dec. 31 via Twitter, wishing followers a “Happy New Year” and linked to a technical write-up outlining the research. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security/?&tag=LPE+Exploit

|
Scooped by
Gust MEES
|
Le compteur des plaintes continue de tourner pour Apple, et il n’a sans doute pas fini de le faire. Aux Etats-Unis et à Israël, le fabricant totalisait déjà huit plaintes, la plupart sous le statut de class-action. Si ces procédures étaient jugées recevables, la firme pourrait écoper de plusieurs millions de dollars de sanctions.
En France, les peines encourues sont généralement moindres. Une condamnation serait cependant préjudiciable à l’image du géant mondial, surtout s’il était reconnu coupable de délit d’obsolescence programmée. C’est sur ce fondement que l’association HOP (Halte à l’Obsolescence Programmée), déjà auteure de plaintes similaires contre les fabricants d'imprimantes, attaque Apple.
Réduire délibérément la durée de vie pour vendre plus
Comme elle le rappelle dans un communiqué, depuis la loi de transition énergétique de 2015, la pratique de l’obsolescence programmée est un délit en France. Or, HOP estime qu’en altérant les performances des iPhone 6, 6S, SE et 7 au travers d’une mise à jour d’iOS, Apple s’est rendu coupable de ce délit.
Le ralentissement du processeur de ces iPhone, officiellement au motif d’en préserver la batterie, relève selon le plaignant de ce délit, défini comme « le recours à des techniques par lesquelles le responsable de la mise sur le marché d’un produit vise à en réduire délibérément la durée de vie pour en augmenter le taux de remplacement. »
L’association considère que la mise à jour par Apple « a lieu au moment même de la sortie de l’iPhone 8. Le ralentissement des appareils plus anciens semble avoir pour intention délibérée de pousser les clients d’Apple à l’achat du nouveau modèle. »
En cas de condamnation, la peine peut aller jusqu’à deux ans de prison et 300.000 euros d’amende, mais surtout 5% du chiffre d’affaires annuel. Et lorsqu’on est la multinationale la plus rentable de l’histoire, ce montant atteint donc plusieurs milliards de dollars. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security/?&tag=Lawsuits https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
Over the years, iPhone owners have often wondered aloud if Apple was doing something to slow down older devices. Now, we know that yes, it does do that. Just a few days after admitting that it has been quietly throttling older iPhones with degraded batteries, a pair of lawsuits have been filed against Apple alleging fraud and deceptive practices.
It became clear during the last few iOS version updates that Apple had opted to apply performance throttling to older devices. It wasn’t until Geekbench ran comparisons with various iOS versions that iPhone owners had any proof. Apple was forced to issue a statement in which is admitted to slowing down iPhones. In some ways, its position makes sense, but the way it handled the situation is terrible.
The situation has to do with how lithium-ion batteries age. We’re all familiar with batteries losing capacity as they get old, but they also have less voltage. It turns out Apple didn’t include enough headroom for the battery, and its voltage can fall below what is needed to power the custom A-series system-on-a-chip. Without enough voltage, the phone can just shut down without warning. Apple’s solution to this was to add performance throttling to iOS based on battery voltage. So, if your battery is degrading, your phone gets slow. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Last week was a really bad week for Apple, with both iOS and macOS falling victim to high profile bugs.
I won't bore you with the details, but the TL:DR of the headaches that Apple -- and more importantly, Apple's customers -- encountered was as follows:
A serious -- and very stupid -- root bug was uncovered in macOS.
The patch that Apple pushed out for the root bug broke file sharing for some.
Updating macOS to 10.13.1 after installing the root patch rolled back the root bug patch.
iOS 11 was hit by a date bug that caused devices to crash when an app generated a notification, forcing Apple to prematurely release iOS 11.2
Stuff happens, I get it.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security/?&tag=Root https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
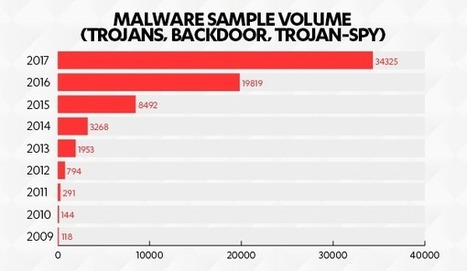
In den ersten drei Quartalen des Jahres 2017 stieg die Zahl der Malware-Angriffe auf Macs um über 70 % und die PUA (potenziell unerwünschte Anwendungen wie z.B. Adware) um 50 % gegenüber dem Vorjahr (Quelle: F-Secure Labs). Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security
|

|
Scooped by
Gust MEES
|
A software developer discovered a bug that lets anyone send you a malicious link on iMessage that can crash your phone.
Because the bug lies in the link preview, it can freeze the iMessage app without you even clicking on it.
Called "chaiOS," the bug affects phones running iOS 10 or later.
A bug called "chaiOS" is wreaking havoc on iPhones.
According to a report out Wednesday from BuzzFeed's Nicole Nguyen, the security vulnerability is capable of freezing or crashing your phone if you're sent a specific link through iMessage.
According to BuzzFeed, the bug was originally discovered by software developer Abraham Masri, who posted his findings to Github. Masri said his intentions were good — he had alerted Apple to the bug ahead of time and said he only posted it publicly to get Apple's attention.
Masri's original post has since been taken down, but the link may still be floating around, according to BuzzFeed.
Because of the way links work in iMessage — the app generates previews of links before you click on them — you can be affected by chaiOS without even clicking on the link itself. The link preview contains the bug, and it can freeze iMessage all on its own. The bug is capable of crashing iMessage altogether, and in some cases, forcing you to restore your phone to factory settings.
The bug affects phones running iOS 10 up to at least iOS 11.2.5 beta 5, according to BuzzFeed. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
Neues Passwort-Problem in MacOS High Sierra
MacOS High Sierra hat erneut ein Problem: Nun ist bekannt geworden, dass die Einstellungen für den eingebauten App Store ohne korrektes Passwort geändert werden können.
In der aktuellen Version von MacOS High Sierra können die Einstellungen im App-Store-Menü in den Systemeinstellungen mit einem beliebigen Passwort geändert werden. Dies zeigt ein Bugreport auf Open Radar. Die Sicherheitslücke ist indes nicht so gravierend wie die passwortlose Root-Anmeldung unter MacOS High Sierra und erfordert einen Administrator-Account. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
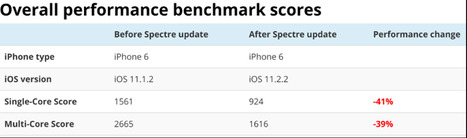
For a number of iPhone owners iOS 11.2.2 is throttling performance by as much as 50%. I exclusively picked up on this trend in my iOS 11.2.2 Upgrade Guide yesterday as users were not just subjectively reporting their iPhones and iPads felt slower, but being able to demonstrate it with before and after benchmark scores (1, 2, 3, 4, 5, etc).
I was subsequently contacted by tech developer Melvin Mughal who, having read my Guide, decided to document a detailed breakdown of how his iPhone 6 performed before and after updating to iOS 11.2.2. For him the impact was dramatic.
Across over 30 single-core and multi-core benchmarks, Mughal found single-core and multi-core performance of his iPhone 6 fell by an average of 41% and 39% after updating to iOS 11.2.2. The results are broken down on his blog. It is worth pointing out Mughal upgrade to iOS 11.2.2 from iOS 11.1.2 not iOS 11.2.1, but that shouldn't be relevant as the throttling Apple introduced in iOS 11.2 was specifically for the iPhone 7 only. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
A bug has been discovered in macOS 10.13.2 that allows you to unlock the App Store system preferences using any username and password as long as you are logged in as a local admin. This means that if your account is an admin and you leave the computer unattended, anyone can change the App Store settings on the Mac without your knowledge.
While this is not as serious as the recent bug that allowed you to gain macOS root access by entering no password repeatedly, it does show that there are some serious code auditing issues in macOS regarding how passwords can be used. This is twice now in as little as three months that the password field was able to be used in macOS to gain extra privileges.
As shown in the video above, using this bug is really simple. Just open up the App Store system preferences and if the little padlock icon is locked, click on it. macOS will then prompt you for a username and password. Enter any username and password you want and press Unlock and the App Store system preferences will become unlocked. This allows you to change settings such as what updates to install, whether to install security updates, and more.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
If you own any Apple products, you're going to want to make sure you have the latest updates installed.
Apple just released two incredibly important security updates for iOS and MacOS, which address the massive Spectre vulnerability Apple previously said affects all Macs and iPhones.
SEE ALSO: Apple on Meltdown and Spectre bugs: 'All Mac systems and iOS devices are affected'
The updates, 11.2.2 for iOS and 10.13.2 for macOS High Sierra, are available now for iPhones, iPads, and Macs.
Spectre was one of two major CPU vulnerabilities revealed by security researchers last week that affects devices with processors from major chip makers, including Intel, AMD, and ARM. Apple previously released software updates to address the other flaw, Meltdown.
While it's always a good idea to keep your software up to date, these latest updates are especially important. As security researchers have warned, the Meltdown and Spectre bugs are particularly nasty. So even if you're the type to wait days, or even weeks, to update to the latest software, you really shouldn't waste any time with these updates.
Google and Microsoft also previously released software updates to address the issue. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Meltdown+and+Spectre+Attacks https://gustmeesde.wordpress.com/2014/12/26/programme-die-auf-jeden-neuen-pc-und-smartphones-gehoren/ https://gustmeesde.wordpress.com/2014/12/16/browser-sind-das-einfallstor-fur-malware-sind-eure-browser-up-to-date/

|
Scooped by
Gust MEES
|
An IT security researcher has leaked details on an unpatched Apple’s macOS bug which lets attackers gain root access and take complete control of a targeted device.
After a disastrous 2017, where Apple faced all sorts of security-related issues and complaints, the company is in trouble again right from the first day of the New Year! On the very first day of 2018 (or the last day of 2017, depending on your location and region), a security researcher having immense expertise in hacking Apple’s iOS has posted details of an unpatched security flaw present in macOS operating system.
“One tiny, ugly bug. Fifteen years. Full system compromise” wrote the researcher, who uses the alias Siguza (s1guza). Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security/?&tag=LPE+Exploit https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
Un chercheur en sécurité a découvert une faille importante datant au moins de 2002. Depuis quelques mois Apple enchaîne les vulnérabilités sur son système d’exploitation.
La faille aurait beau avoir plus de quinze ans, elle n’en donne pas moins accès à tout le contrôle de macOS. C’est la découverte réalisée par le chercheur en sécurité Siguza qui a dévoilé la chose sur Twitter et GitHub. Cette vulnérabilité zero-day concerne directement le kernel de l’OS d’Apple. Consolation pour les potentielles victimes, il faut toutefois avoir accès à la machine pour pouvoir l’exploiter.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security/?&tag=LPE+Exploit https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Mit "Apple iCloud für Windows" können Sie persönliche Dokumente, Mails, Fotos und Termine zwischen Apple-Geräten wie iPhone oder iPad und Windows-PC synchronisieren.
Apple hat für seine Software "iCloud für Windows" ein außerplanmäßiges Update auf Version 7.2 veröffentlicht, das gleich mehrere Sicherheitslücken schließt.
Das Bundesamt für Sicherheit in der Informationstechnik (BSI) stuft die Sicherheitslücken auf seiner fünf-stufigen Skala mit Risikostufe 4 ("hoch") ein und empfiehlt allen iPhone- oder iPad-Nutzern mit Windows-PCs das Programm möglichst schnell zu updaten:
Apple behebt mit einem Sicherheitsupdate für iCloud für Windows mehrere Sicherheitslücken, die von einem Angreifer aus dem Internet ausgenutzt werden können, um beliebige Aktionen auf Ihrem Gerät auszuführen und private Informationen über Sie zu sammeln.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
Quietly inserting code into iOS that measurably slows down the performance of older iPhones is a monumentally boneheaded blunder.
The ink is barely dry on the piece I wrote earlier this week about how Apple needs to do better in 2017 when it comes to light that the company has done another boneheaded thing.
Must read: Apple seems to have forgotten about the whole 'it just works' thing
It now turns out that the old yet often-quoted urban legend that Apple inserts code into iOS to slow down older iPhones is true.
Yes, Apple is slowing down your old iPhone.
The company admitted yesterday that it started doing it last year when it released iOS 10.2.1 following reports that iPhone 6, iPhone 6s, and iPhone SE were shutting down randomly due to cold weather, low battery charge, or battery aging.
Apple expanded the scope of this code to include iPhone 7 and iPhone 7 Plus devices with the release of iOS 11.2. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
Apple said it has fixed an undisclosed vulnerability in its HomeKit framework that could have allowed unauthorized remote control of HomeKit devices such as smart locks and connected garage door openers.
The flaw was first reported by the publication 9to5Mac on Thursday. According to the publication, the vulnerability requires an iPhone or iPad running the latest iOS 11.2 that is linked to the HomeKit user’s iCloud account. Related PostsDecember 7, 2017 , 1:51 pm November 28, 2017 , 8:47 pm November 14, 2017 , 9:00 am
The write-up on the vulnerability is vague and does not state what the specific vulnerability is, only that it was demonstrated to the publication and that it is complex to exploit. HomeKit is Apple’s software framework for smart-home appliances that lets iPhone and iPads users communicate with and control dozens of compatible third-party HomeKit-enabled devices.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
Blamable Woche für Apple: Mehrere Fehler in seinen Betriebssystemen zwingen das Unternehmen zu schnellen Updates – und die Kunden zu Wachsamkeit. Vier recht peinliche Software-Fehler in nur einer Woche also. Die Zahl der konkret Betroffenen ist zwar möglicherweise nicht besonders hoch. Aber angesichts der enormen Verbreitung von Apple-Hardware ist das Unternehmen immer gezwungen, schnell Updates zu entwickeln und auf die riesige Nutzerbasis zu verteilen, stets unter medialer Beobachtung.
Außerdem ist Apple längst nicht mehr nur Hardware-Hersteller, auch wenn es mitunter noch so wahrgenommen wird. Software und Dienste gehören aber genauso zu seinem Ökosystem, und beide haben nicht erst seit dieser Woche einen deutlich schlechteren Ruf als die Geräte, auf denen sie laufen.
Das Unternehmen wirbt aber gern damit, dass seine Produkte besonders sicher seien und sich besonders leicht bedienen ließen. Und so muss es sich wohl auch an seinen Werbesprüchen messen lassen. Einer lautet zurzeit: "Anything you can do, you can do better."
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security/?&tag=Root https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security
|



 Your new post is loading...
Your new post is loading...
























We knew that other companies were recording interactions with their smart devices, and using some of those recordings to check for quality by having real people listen to those interactions. But, until now, we thought Apple was different.
On Friday Apple confirmed, to the Guardian, a whistleblowers account that the company has similar practices to Google and Amazon, but never disclosed that fact in its privacy policy.
Apple samples a small number of recordings of interactions with its voice assistant Siri, which is used by millions of Americans on their iPhones, Apple Watch, and other iOS and Mac devices. According to the whistleblower, that includes "countless instances of recordings featuring private discussions between doctors and patients, business deals, seemingly criminal dealings, sexual encounters and so on."
I accidentally wake up Siri all the time on my watch or phone when I have no intention of interacting with her, and I've never given any thought to the fact that she's listening to whatever goes on in the background. In fact, we have a daughter whose name apparently sounds close enough to "hey Siri," that I'm frequently reminded by my iPhone that "you need to clean up your room," and "come set the table," are not commands yet supported by voice assistants (though that would be awesome).
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security
http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security/?&tag=Privacy
http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security/?tag=SIRI