 Your new post is loading...
 Your new post is loading...
Les contrôles d’accès censés protéger les données personnelles comme le carnet d’adresses peuvent être contournés, comme vient de le démontrer un chercheur en sécurité.
Depuis hier, 24 septembre, les utilisateurs d’ordinateurs Mac peuvent installer la dernière version du système d’exploitation macOS Mojave. Malheureusement, celle-ci est déjà impacté par une importante faille de sécurité qui met à mal la protection des données personnelles. Avec macOS Mojave, Apple a en effet musclé les contrôles d’accès aux fichiers et aux applications sensibles tels que le carnet d’adresses, l’historique des messages, la base de données d’email, le microphone, la caméra, etc. Mais ces contrôles d’accès peuvent être court-circuités, comme le démontre le chercheur en sécurité Patrick Wardle.
Cet expert a développé une application baptisée « breakMojave » capable de siphonner en douce le carnet d’adresses de l’utilisateur sans rien lui demander. Il a montré le déroulement du hack dans une vidéo Vimeo. Au départ, on constate qu’aucune application tierce n’a accès au carnet d’adresses. Le chercheur ouvre ensuite une fenêtre Terminal et tente d’accéder directement aux données du carnet d’adresses, sans succès. Le lancement de breakMojave provoque enfin l’extraction des données, qui se retrouvent copiées en vrac sur le bureau. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
Les chercheurs en sécurité de Versprite ont identifié plusieurs failles de sécurité touchant Airmail pour Mac. Ces dernières pourraient compromettre la sécurité d'un compte, laissant un accès libre à la totalité des messages.
Sur un blog, Versprite dévoile en détail la méthode mise en place pour tirer partie des vulnérabilités du logiciel. Pour résumer, l'attaque commence par l'envoi d'un mail comprenant un ou plusieurs liens faisant office de piège, et contenant un schéma URL particulier à Airmail. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
Unfortunately for Apple, and customers who like to believe that their phone is private, a workaround has been discovered whereby police could prevent an iPhone or iPad entering USB Restricted Mode if they act quickly enough.
Researchers at Elcomsoft discovered that the one hour countdown timer can be reset simply by connecting the iPhone to an untrusted USB accessory:
“In other words, once the police officer seizes an iPhone, he or she would need to immediately connect that iPhone to a compatible USB accessory to prevent USB Restricted Mode lock after one hour. Importantly, this only helps if the iPhone has still not entered USB Restricted Mode.”
And where might you find such a compatible USB accessory that can prevent USB Restricted Mode from kicking in?
Look no further than Apple’s own online store, where the company will happily sell you a Lightning to USB 3 Camera Adapter for a mere $39. Chances are that there are even cheaper accessories which will do the job just as well. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
A bug in macOS can expose the contents of a user's files -- including document text and photo thumbnails -- even if the drive is encrypted.
Security researcher Wojciech Regula found that the "Quick Look" feature in macOS, which takes a snapshot of a file's contents and the full file path without the user having to open each file, stores that snapshot data in an unprotected location on the computer's hard drive.
Regula, a security specialist, wrote up details about the macOS data leak issue earlier this month.
"It means that all photos that you have previewed ... are stored in that directory as a miniature and its path," Regula wrote. They stay there even if you delete the files, he said.
Patrick Wardle, chief research officer at Digita Security, built on Regula's work in his own blog post, published Monday, noting that the bug is triggered every time a user opens a folder.
The bug exposes even encrypted volumes to potential snooping.
"If we unmount the encrypted volume, the thumbnails of the file are ... still stored in the user's temporary directory, and thus can be extracted," said Wardle. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security/?&tag=Encryption

|
Scooped by
Gust MEES
|
Apple loggt APFS-Passwort im Klartext mit
Wer externe Datenträger mit APFS nutzt und diese verschlüsselt, dessen Passwort wird in einigen MacOS-Versionen im Klartext mitgeloggt. Der Fehler ist bislang nur teilweise behoben worden.
Wer externe Datenträger mit Apples Dateisystem APFS (Apple Filesystem) nutzt und diese verschlüsselt, dessen Passwort wird in einigen Versionen von MacOS im Klartext mitgeloggt, wie die Forensik-Expertin Sarah Edwards schreibt. Der Fehler ist von Apple mit der aktuellen Version 10.13.3 bei der Einrichtung neuer Volumes behoben worden, verwundbar waren offenbar Nutzer der Versionen 10.13.1 und 10.13.2. Auch die Version 10.13.2 ist mittlerweile gegen Angriffe abgesichert.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
Il n’y a apparemment pas que Cellebrite qui peut s’immiscer dans les smartphones d’Apple. Ce jeudi 15 mars 2018, la société de sécurité Malwarebytes a publié un article sur son blog au sujet d’un mystérieux boîtier baptisé GrayKey, qui serait capable de briser la sécurité et d’absorber les données de n’importe quel iPhone en circulation.
Commercialisé par la petite entreprise américaine Grayshift (moins de 50 employés), ce boîtier semble avoir vocation à intégrer les bureaux des agences gouvernementales, notamment américaines. Toutefois, très peu d’informations sont disponibles à l’heure actuelle. Pour accéder au site de la société, il faut d’abord en faire la demande. Autrement, impossible d’obtenir la moindre information : « GayKey n’est pas pour tout le monde », peut-on lire sur le site.
Deux versions du boîtier
Malwarebytes a mené l’enquête et a tout de même réussi à mettre la main sur quelques éléments intéressants. On apprend notamment que deux variantes du boîtier sont proposées aux clients de Grayshift. La première est vendue 15 000 dollars mais elle comporte des limitations et requiert une connexion à Internet. Par exemple, une fois installé, l’appareil sera « géo-bloqué », il sera donc impossible à déplacer. Le nombre de déverrouillages semble également limité.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security/?&tag=Cellebrite

|
Scooped by
Gust MEES
|
Apple has confirmed that it is working on a bug fix that will stop apps like Messages from crashing when they attempt to display a Unicode symbol representing a letter from the south Indian language of Telugu.
The Unicode-based bug has been exploited by juvenile pranksters, who posted app-crashing messages on Twitter, WhatsApp, Instagram, and Facebook, or even changed their screenname to one which contained the symbol.
The symbol, which I won’t repeat here for fear of crashing readers’ apps (trust me.. while writing this article I managed to bork my browser once at twice), can cause iPhones, iPads, Apple Watches and even Apple TV devices to endlessly reboot themselves if received in a notification. If you’re curious there’s a good write-up about it on Mozilla engineer Manish Goregaokar’s blog.
One security researcher demonstrated that it was possible to make macOS network applications crash by creating a Wi-Fi hotspot which included the offending symbol. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security/?&tag=Telugu+Character https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security/?&tag=iOS https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Des extraits du code source d'iOS 9 ont été postées sur GitHub. Apple a confirmé la fuite en la faisant supprimer du site. Elle pourrait autant amener des pirates que des chercheurs en sécurité informatique à trouver des vulnérabilités sous iOS.iBoot : cinq petites lettres qui ne plaisent vraiment pas à Apple. Mercredi 7 février, un ou une internaute a publié sur GitHub le code source d'un composant clé du système d'exploitation de l'iPhone. Une fuite "qui pourrait autant amener des pirates que des chercheurs en sécurité à trouver des vulnérabilités sous iOS et à réussir plus facilement des jailbreaks", rapporte Motherboard. Si le code partagé sur GitHub – désormais supprimé – indiquait qu'il s'agissait d'une partie du code source d'iOS 9 (une vieille version du système d'exploitation), "certaines parties sont probablement encore utilisées sous iOS 11", suggère Motherboard. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
US authorities have charged a 28-year-old Ohio man who is alleged to have created and installed creepy spyware on thousands of computers for 13 years.
Phillip R. Durachinsky, of North Royalton, Ohio, is alleged to have used Mac malware known as “Fruitfly” to remotely control victims’ computers, access and upload files, grab screenshots, log keystrokes, and surreptitiously spy via infected computer’s webcams.
Durachinsky, who faces multiple charges including Computer Fraud and Abuse Act violations, Wiretap Act violations, and identify theft, is said to have created a visual interface that allowed him to retrieve live images from several infected computers simultaneously.
In the indictment, Durachinsky is said to have used malware he created between 2003 and January 2017 to steal personal data, tax records, passwords, and “potentially embarrassing communications.”
According to the indictment, Durachinsky used stolen usernames and passwords to hack into his victims’ online accounts and steal further information, keeping detailed notes on his victims. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security/?&tag=Fruitfly

|
Scooped by
Gust MEES
|
Un utilisateur d’Open Radar a découvert un petit souci dans macOS 10.13.2. Il permet à un administrateur local de modifier les préférences systèmes du Mac App Store en saisissant n’importe quel mot de passe.
Sale temps pour la sécurité sur macOS. Le dernier bug de sécurité en date n’est pas du niveau des précédents mais fait malgré tout un peu tache sur le CV d’Apple. Un utilisateur d’Open Radar, une communauté de rapporteurs de bugs, a révélé un petit souci dans macOS High Sierra 10.13.2, la dernière version officiellement disponible.
Ainsi, selon lui, n’importe quel utilisateur administrateur local sur la machine peut ouvrir le panneau des Préférences Système du Mac App Store et déverrouiller le cadenas qui empêche les modifications de ces réglages en saisissant n’importe quel mot de passe. Si le cadenas est déjà ouvert et que cet utilisateur souhaite tenter sa chance, c’est possible. Il suffit de le refermer, de l’ouvrir à nouveau et de taper n’importe quelle suite de lettres ou chiffres. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
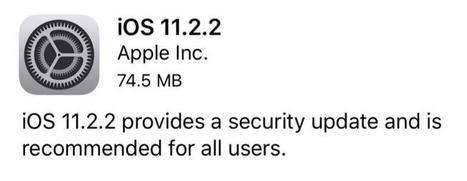
Another day, another patch to install. This time, it's iOS 11.2.2 for iPhone, iPad, and iPod touch.
Must read: How to tell if your iPhone battery needs replacing
The patch is to fix the Spectre vulnerability that came to light earlier this month.
Apple describes the patch as follows:
iOS 11.2.2 includes security improvements to Safari and WebKit to mitigate the effects of Spectre (CVE-2017-5753 and CVE-2017-5715).
Apple says it "recommends" the update "for all users."
To download the update, go to Settings > General > Software Update (the preferred way, and this way the patch is only about 75MB), or connect your iPhone to a computer running iTunes and then carry out the update (this is slower and downloads the entire iOS 11.2.2 package, which is several gigabytes, as opposed to just the smaller update). Learn more / en savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
Apple just released iOS 11.2.2 with some Safari and WebKit improvements to mitigate the Spectre vulnerability. macOS is also receiving an update. It’s a supplemental update to macOS High Sierra 10.13.2 and it includes the same fix.
As always, you should update your devices with the latest security patches. In this case, Meltdown and Spectre are serious vulnerabilities. With Meltdown, a malicious application running on an unpatched device can read the unencrypted kernel memory. You don’t want anyone to grab your password and private encryption keys.
Meltdown was already addressed in previous updates. iOS 11.2, macOS 10.13.2 and tvOS 11.2 already included mitigations for Meltdown. Apple Watch chips aren’t affected by Meltdown.
Spectre isn’t as serious as it only breaks the isolation between multiple applications. But it can be exploited using JavaScript in a web browser. That’s why it’s important to fix it before somebody figures out how to distribute malicious JavaScript code in an ad unit.
On your iPhone or iPad, head over to the Settings app, then tap on General and Software Update. On your Mac, open the Mac App Store and check for updates. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security/?&tag=LPE+Exploit https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security
|

|
Scooped by
Gust MEES
|
An Australian teenager has admitted hacking into Apple’s internal network and stealing 90 GB worth of files.
The 16-year-old, who cannot be named for legal reasons, has pleaded guilty to breaking into Apple’s systems on multiple occasions over the course of a year, from his parent’s home in Melbourne’s suburbs.
According to a report in The Age, the young hacker claimed to be a “fan” of the company, who “dreamed” of working for Apple one day.
The teen is thought to have attempted to hide his identity using a variety of tools, such as VPN software. But after Apple eventually spotted the unauthorised access of their internal systems they informed the FBI, who in turn worked with the Australian Federal Police to track down the intruder.
A search of the teenager’s home last year saw law enforcement officers seize two Apple laptops with serial numbers that “matched the serial numbers of devices which accessed the internal systems”, according to a prosecutor.
In addition, a mobile phone and hard drive was also seized. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
Longstoryshort, Holmes was able to copy this API token, paste it into his own web requests, and get read-and-write access to much of Homebrew’s GitHub content.
As he explains in his post, he could have hacked pretty much any Homebrew package, thereby infecting any and every Mac user who installed or updated that package – or, of course, any other package that depended on it.
And, as Holmes wryly pointed out, the most downloaded package in the last 30 days at Homebrew is itself all about cybersecurity: openssl, with more than half-a-million installs last month.
That’s a lot of Brew users – and by implication a lot of developers who themselves build software for distribution to other people – whom he could have put on the spot.
What to do?
If you’re a Brew user, there’s no need for alarm and no immediate action you need to take.
Holmes disclosed this responsibly to the Homebrew crew, who fixed the issue right away – within a few hours, in fact – and published a short, frank and informative disclosure notice.
As in the case of Gentoo’s recent supply-chain breach, the disclosure notice is worth reading whether the incident directly affects you or not.
Howebrew included some security precautions that the team is planning to add, and why. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security/?&tag=Nobody+is+perfect

|
Scooped by
Gust MEES
|
Ein Bug in der QuickLook-Schnellansicht speichert auch geschützte Dateien im Dateisystem, so Sicherheitsforscher.
In macOS wird ein Sandboxing verwendet, um sensible Daten voneinander zu trennen. Zudem sollte das Betriebssystem auch keine verschlüsselten Dateien zwischenspeichern. Doch genau dieses geschieht aufgrund eines Bugs – und das sogar schon über mehrere Jahre, wie zwei Sicherheitsforscher nun herausgefunden haben.
Der Fehler, so schreiben der Original-Autor Wojciech Regula und sein Kollege Patrick Wardle, liegt in der Schnellansicht QuickLook, die im macOS-Dateimanager Finder bereitsteht und es ermöglicht, mit einem Druck auf die Leertaste Dateiinhalte – etwa Bilder, Tabellen oder Texte – flott durchzusehen.
Automatische Zwischenspeicherung
Wird QuickLook verwendet, werden aufgerufene Bilder und andere Dokumentenarten allerdings automatisch zwischengespeichert – zwar nicht in Form der Originaldatei, jedoch in Form von Icon-Miniaturen (Thumbnails). Dabei unterscheidet macOS nicht zwischen verschlüsselten und unverschlüsselten Dateien. Die Thumbnails lassen sich dann wiederum in einem Cache-Verzeichnis auffinden und anschauen – Zugriff auf das (unverschlüsselte) Hauptmedium des Macs vorausgesetzt. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security/?&tag=Encryption

|
Scooped by
Gust MEES
|
Apple delivered its latest batch of security updates for iOS and macOS this week.
On iDevices, the update was a full-on point release, bumping the iOS version from 11.3 to 11.3.1 and making it easy to check whether you’ve installed the update correctly: just go to Settings → General → Software Update and see what version number you’re currently on.
For Mac users, the patch is dubbed simply Security Update 2018-001, so your macOS version stays at 10.13.4 after you’ve installed it.
Safari was bumped from 11 to 11.1 in this update – note that if you’re still on El Capitan or Sierra (OS X 10.11.6 and macOS 10.12.6 respectively), where there isn’t a 2018-001 update, you’ll need to update Safari separately.
Just two critical vulnerabilities were patched this time, both of them in the WebKit web rendering code in iOS and macOS. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
Über die Ausnutzung von insgesamt drei Fehlern gelang es einem Sicherheitsforscher, aus dem Browser heraus tief in macOS einzugreifen. Auch ein weiterer Safari-Hack verlief erfolgreich.
Auf der diesjährigen Pwn2Own der Zero Day Initiative im Rahmen der CanSecWest-Konferenz im kanadischen Vancouver gelangen Sicherheitsforschern in der letzten Woche zwei erfolgreiche Angriffe auf macOS über den Apple-Browser Safari.
Verkettung von drei Fehlern
Samuel Groß von der Gruppe phoenhex, dem zusammen mit einem Kollegen im vergangenen Jahr ein ähnlicher Angriff gelungen war, zeigte einen aus drei Fehlern bestehenden Angriff, bei dem es über Safari gelang, einen Text auf der eigentlich besonders geschützte Funktionstastenleiste Touch Bar eines MacBook Pro zu platzieren (siehe Bild). In Safari nutzte Groß einen JIT-Optimization-Bug und anschließend einen Logikfehler in macOS, um die Sandbox zu verlassen. Fehler drei war ein Kernel-Overwrite, über den Code mit Hilfe einer Kernel-Erweiterung ausgeführt werden konnte. Groß erhielt 65.000 US-Dollar und 6 "Master of Pwn"-Punkte.
EInem zweiten Team, den MWR Labs um Alex Plaskett, Georgi Geshev und Fabi Beterke, gelang am zweiten Tag der Pwn2Own wiederum ein Sandbox-Escape in Safari. Dabei wurden zwei Fehler ausgenutzt. Die Gruppe erhielt 55.000 Dollar und 5 "Master of Pwn"-Punkte. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Pwn20wn

|
Scooped by
Gust MEES
|
Déjà quatre nouveaux malwares identifiés en 2018 sur Mac
Malwarebytes dévoile en outre que pas moins de quatre nouveaux malwares ont été identifiés depuis le début de l'année 2018. L'un d'entre eux a été identifié par un utilisateur dont les DNS ont été changés à son insu et qui s'est retrouvé dans l'impossibilité de les remettre à zéro : OSX.MaMi. Outre le changement de DNS, le malware avait également installé un nouveau certificat de sécurité.
Un autre malware serait issu des outils développés par le Liban dans le cadre de l'opération d'espionnage d'Etat DarkCaracal. Ce malware ne serait toutefois qu'en phase de développement, la version identifiée étant la 0.1, d'après Malwarebytes. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
C'est le site italien mobileworld.it qui rapporte l'information. Un message texto spécifique composé avec un caractère de cette écriture provoque de nombreux problèmes.
En en cas de notification embarquant le message, c'est l’interface d’accueil du terminal, nommée Springboard, qui est mis en berne. Et en cas de reboot, l'appareil peut se retrouver à redémarrer sans cesse. Alors, seule la réinitialisation peut sauver l'utilisateur.
iMessage, WhatsApp et Facebook Messenger touchés
Le bug fonctionne sur la version iOS 11.2.5 du système d'exploitation, la dernière version de l'outil. Mais il ne marche pas avec iOS 11.3 beta. Le bug a été testé avec macOS et watchOS. Et il fonctionne dans cette configuration. A noter que les applications iMessage, WhatsApp, Facebook Messenger, Outlook for iOS, et Gmail sont sensibles à ce fâcheux bug. A noter que Telegram et Skype ne sont pas touchés par ce bug.
Apple a mentionné qu’il allait corriger ce bug avant la sortie d’iOS 11.3, prévue pour dans quelques mois. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security/?&tag=iOS https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
What’s happened? Earlier this week someone anonymously published a key piece of Apple’s iOS source code onto GitHub. Which bit of iOS was it? It was an integral part of iOS known as “iBoot” – the section of code which controls the security of your iPhone or iPad as it starts up. So it’s an important part of iOS? Very important and highly sensitive. The secure boot firmware ensures that iOS will only run apps digitally signed by Apple, and checks that the operating system has not been tampered with by a hacker. Does that make this leak interesting to hackers? Yes, and to other parties (I’m looking at you principally law enforcement agencies) who might be interested in finding vulnerabilities that could be exploited to help them compromise and unlock iOS devices. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
A software developer discovered a bug that lets anyone send you a malicious link on iMessage that can crash your phone.
Because the bug lies in the link preview, it can freeze the iMessage app without you even clicking on it.
Called "chaiOS," the bug affects phones running iOS 10 or later.
A bug called "chaiOS" is wreaking havoc on iPhones.
According to a report out Wednesday from BuzzFeed's Nicole Nguyen, the security vulnerability is capable of freezing or crashing your phone if you're sent a specific link through iMessage.
According to BuzzFeed, the bug was originally discovered by software developer Abraham Masri, who posted his findings to Github. Masri said his intentions were good — he had alerted Apple to the bug ahead of time and said he only posted it publicly to get Apple's attention.
Masri's original post has since been taken down, but the link may still be floating around, according to BuzzFeed.
Because of the way links work in iMessage — the app generates previews of links before you click on them — you can be affected by chaiOS without even clicking on the link itself. The link preview contains the bug, and it can freeze iMessage all on its own. The bug is capable of crashing iMessage altogether, and in some cases, forcing you to restore your phone to factory settings.
The bug affects phones running iOS 10 up to at least iOS 11.2.5 beta 5, according to BuzzFeed. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
Neues Passwort-Problem in MacOS High Sierra
MacOS High Sierra hat erneut ein Problem: Nun ist bekannt geworden, dass die Einstellungen für den eingebauten App Store ohne korrektes Passwort geändert werden können.
In der aktuellen Version von MacOS High Sierra können die Einstellungen im App-Store-Menü in den Systemeinstellungen mit einem beliebigen Passwort geändert werden. Dies zeigt ein Bugreport auf Open Radar. Die Sicherheitslücke ist indes nicht so gravierend wie die passwortlose Root-Anmeldung unter MacOS High Sierra und erfordert einen Administrator-Account. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
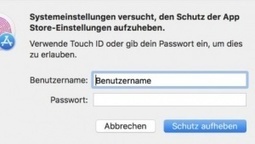
MacRumors spotted a bug report that affects the current version of macOS High Sierra. In System Preferences, you can unlock the App Store preference pane by typing any password. Apple has reportedly already fixed the bug in beta versions of the next macOS High Sierra update.
While this bug is nowhere as serious as the infamous root login bug, as John Gruber wrote, this one is quite embarrassing. What’s wrong with password prompts and macOS?
If you want to test this bug at home, I was able to reproduce it quite easily. Open System Preferences, go to the App Store settings and look at the padlock icon. If it’s unlocked, lock it first and then try unlocking it with any password. Ta-da!
You can enable or disable automatic downloads and installation of app and operating system updates using this preference pane. This doesn’t represent an immediate security risk. But if someone already has access to your computer, they could disable automatic security updates and take advantage of vulnerabilities that are regularly patched.
By default, App Store settings are unlocked for admin users. But if you’re a bit paranoid about security, chances are you locked down all your system settings to make sure nobody is playing with them.
More importantly than the bug itself, Apple should reconsider their quality assurance processes. It’s time to stop shipping updates with embarrassing bugs. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
If you own any Apple products, you're going to want to make sure you have the latest updates installed.
Apple just released two incredibly important security updates for iOS and MacOS, which address the massive Spectre vulnerability Apple previously said affects all Macs and iPhones.
SEE ALSO: Apple on Meltdown and Spectre bugs: 'All Mac systems and iOS devices are affected'
The updates, 11.2.2 for iOS and 10.13.2 for macOS High Sierra, are available now for iPhones, iPads, and Macs.
Spectre was one of two major CPU vulnerabilities revealed by security researchers last week that affects devices with processors from major chip makers, including Intel, AMD, and ARM. Apple previously released software updates to address the other flaw, Meltdown.
While it's always a good idea to keep your software up to date, these latest updates are especially important. As security researchers have warned, the Meltdown and Spectre bugs are particularly nasty. So even if you're the type to wait days, or even weeks, to update to the latest software, you really shouldn't waste any time with these updates.
Google and Microsoft also previously released software updates to address the issue. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Meltdown+and+Spectre+Attacks https://gustmeesde.wordpress.com/2014/12/26/programme-die-auf-jeden-neuen-pc-und-smartphones-gehoren/ https://gustmeesde.wordpress.com/2014/12/16/browser-sind-das-einfallstor-fur-malware-sind-eure-browser-up-to-date/
|



 Your new post is loading...
Your new post is loading...

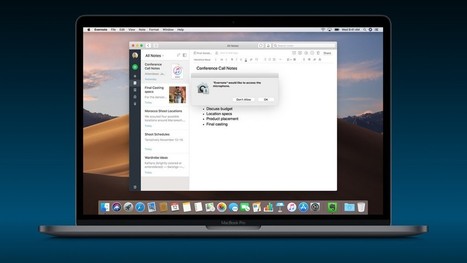

























Les contrôles d’accès censés protéger les données personnelles comme le carnet d’adresses peuvent être contournés, comme vient de le démontrer un chercheur en sécurité.
Depuis hier, 24 septembre, les utilisateurs d’ordinateurs Mac peuvent installer la dernière version du système d’exploitation macOS Mojave. Malheureusement, celle-ci est déjà impacté par une importante faille de sécurité qui met à mal la protection des données personnelles. Avec macOS Mojave, Apple a en effet musclé les contrôles d’accès aux fichiers et aux applications sensibles tels que le carnet d’adresses, l’historique des messages, la base de données d’email, le microphone, la caméra, etc. Mais ces contrôles d’accès peuvent être court-circuités, comme le démontre le chercheur en sécurité Patrick Wardle.
Cet expert a développé une application baptisée « breakMojave » capable de siphonner en douce le carnet d’adresses de l’utilisateur sans rien lui demander. Il a montré le déroulement du hack dans une vidéo Vimeo. Au départ, on constate qu’aucune application tierce n’a accès au carnet d’adresses. Le chercheur ouvre ensuite une fenêtre Terminal et tente d’accéder directement aux données du carnet d’adresses, sans succès. Le lancement de breakMojave provoque enfin l’extraction des données, qui se retrouvent copiées en vrac sur le bureau.
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security