A series of disconnected events can be used to identify a threat.
Imagine your system alerting you that one of your endpoints has received a suspicious file from a suspicious site. It generates a low priority alert that gets lost in the flood of other alerts.
The infected endpoint connects to several popular news sites and downloads their front page. This will not generate any alerts. What happened is that the infected endpoint just confirmed network connectivity.
After several hours, your alert screen, having wrapped a few hundreds of times since the infection, reports another low priority alert. The infected endpoint (bot) is now trying to locate other bots by looking up randomly generated URIs based on dynamic DNS domains. Your IPS sees this as a number of failed DNS queries followed by a successful one. The newly infected bot then connects to another bot downloading its payload with no traffic traversing the IPS since it is not communicating outside.
Does this sound far-fetched and unlikely, like an extreme example? Well, this is how Kraken works, and the Kraken botnet has been active since at least 2008.



 Your new post is loading...
Your new post is loading...

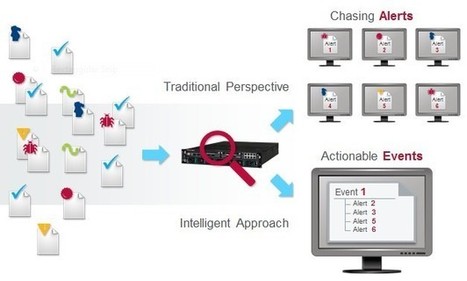






"Next-gen" Intrusion Protection Systems can be misleading. The primary concern should be stronger security infrastructure, while making the best use of analysts’ time.