This survey aims to provide a general, comprehensive, and structured overview of the state-of-the-art methods for anomaly detection in data represented as graphs..
Research and publish the best content.
Get Started for FREE
Sign up with Facebook Sign up with X
I don't have a Facebook or a X account
Already have an account: Login

Outliers, aberrations, fat tails, trouble at the mill and maybe something good once in awhile
Curated by
Ellie Kesselman Wells
 Your new post is loading... Your new post is loading...
 Your new post is loading... Your new post is loading...
|
Tony Agresta's curator insight,
December 3, 2013 2:48 PM
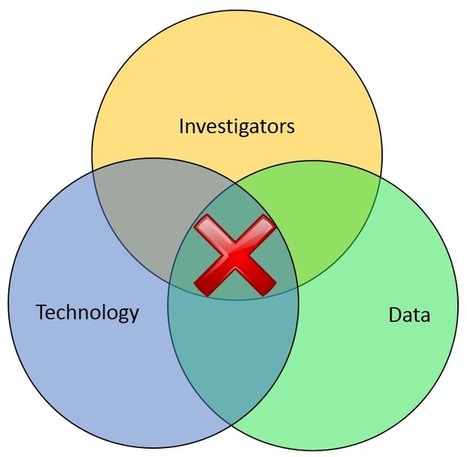
Here's another good post from Doug Wood of www.fightfinancialcrimes.com. Advances in technology are revolutionizing how fraud investigations are being done today. |









Via arXiv