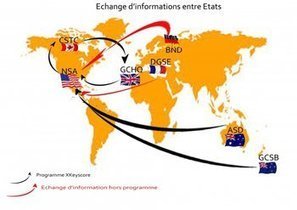
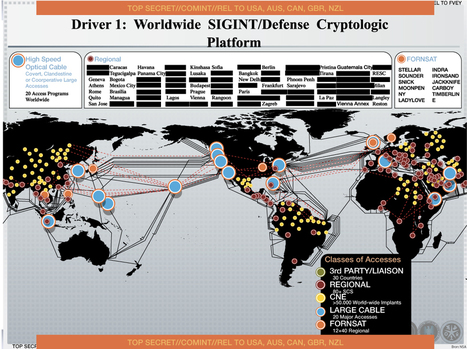
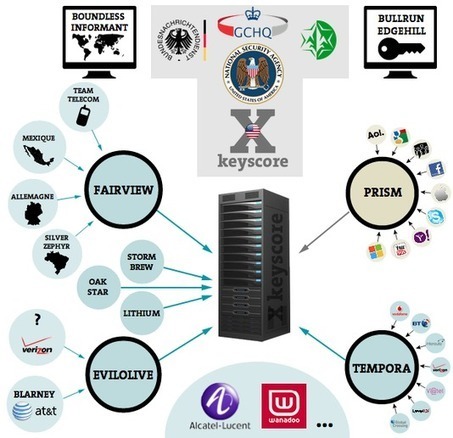
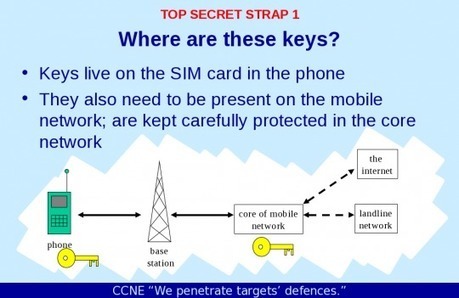
"The House of Representatives passed bipartisan legislation on Wednesday designed to help companies and the federal government better defend against the growing threat of cyberattacks, despite opposition from privacy advocates.
Passed by a 307-116 vote, the controversial Protecting Cyber Networks Act encourages US companies to share information about security breaches with the federal government by providing them with expanded legal liability protections. Prompted in part by a recent uptick in high-profile data breaches, the legislation would allow companies to share information through a "cyber portal" administered by the Department of Homeland Security..."



 Your new post is loading...
Your new post is loading...