 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
|
Share this news now.Share this news now.In a cybercrime ecosystem populated by commercially available WordPress brute-forcing and mass vulnerable WordPress installation scanning tools, cybercriminals continue actively capitalizing on the platform’s leading market share within the Content Management System’s market segment.
Successfully exploiting tens of thousands of installations on a daily basis, for the purpose of utilizing the legitimate infrastructure to achieve their fraudulent/malicious campaign objectives, the tactic is also largely driven by the over-supply of compromised/accounting data, usually embedded within sophisticated Web-based attack platforms like the ones we’ve profiled in the past.
We’ve recently intercepted a malicious campaign exclusively relying on rogue WordPress sites, ultimately serving client-side …Share this news now.
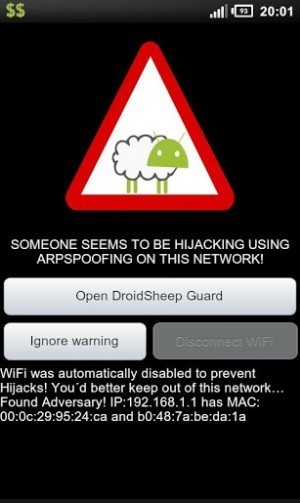
DroidSheep Guard protects your phone from DroidSheep, Faceniff & other hijackers DroidSheep Guard protects your phone from Tools like DroidSheep, Faceniff and other Se...

|
Scooped by
Gust MEES
|
OpenVPN - The Open Source VPN

|
Scooped by
Gust MEES
|
There are 50,538 smartphones and tablets in use at Cisco, which has 71,825 employees. Not only does that already comprise a ratio of one device per 1.4 employees, said Lance Perry, vice-president of IT customer strategy and success for Cisco, during an excellent presentation at the Consumerization of IT in the Enterprise (CITE) conference in San Francisco on Monday. But the 50,000+ device figure is also an increase of 52% from just 12 months earlier. Read more: the practice... http://www.forbes.com/sites/sap/2012/03/05/cisco-the-biggest-mobile-byod-deployment-around/

|
Scooped by
Gust MEES
|
"iPhones, iPads, Androids, Tablets are pouring into organizations. In today's BYOD culture, AirTight often sees 3 times as many unmanaged personal devices in a customer's airspace than corporate devices. ===> The key to keeping your network secure is to manage those devices." <=== Read more...
Anti-Theft is an application for your mobile phone that provides a great way to protect it if it gets lost or stolen – and it’s FREE!
This is what you get:
- Easy to install and use
- Protects your confidential information against loss or theft
- Helps you locate your phone
Read more...
SC Magazine has various news articles and information for IT security professionals. Bring-your-own-device and cloud security are just some of the topics that add to the changing threat landscape of online security. Read more...

|
Scooped by
Gust MEES
|
A BYOD policy can eliminate a lot of the problems associated with bring your own device programs. Learn best practices for creating a BYOD policy. BYOD isn’t a synonym for “free for all.” Once an organization decides to let employees use their own mobile devices and PCs for work, it must put a BYOD policy in place to control this usage. ===> Requires Free Membership to View
Your phone goes everywhere with you. You keep it at your desk at work, near your bed when you sleep, and in your pocket during dinner. Many people use their phones for mobile banking, keeping in close touch with friends and family over Facebook and Twitter, and sending countless text messages about their daily lives. But do our phones deserve the trust we place in the security of all the information we're giving them? If you choose your apps carefully and give out your personal information sparingly, you'll have no problem at all. But if you download everything and give out your name and address every time you can, you'll be making a huge mistake.

|
Scooped by
Gust MEES
|
In the face of new threats aimed at OS X, a security expert has warned that Mac users may be even more vulnerable than Windows users. Because Windows users are more likely to be running up-to-date anti-virus programs, Graham Cluley of Sophos says that many Mac users are missing a "valuable safety net". In the face of several new threats targeting Mac OS X that have been discovered in recent weeks, Mac users should make sure that they have some form of protection, Cluley said. However, keeping your computer safe from cybercriminals isn't just a case of having anti-virus programs installed - it's about making sensible choices as well. As we have seen on the Windows platform, the majority of the attacks do not exploit any weakness in the operating system but instead take advantage of the bug in people's brains. ===> Mac users can be just as easily duped as their Windows cousins into making poor choices, and could end up infected as a result, Cluley told Macworld. <=== Use antivirus programs!
|
Avira launched the Avira Rescue System, a software first aid kit for scanning and repairing PC computers that are already infected with malw...

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
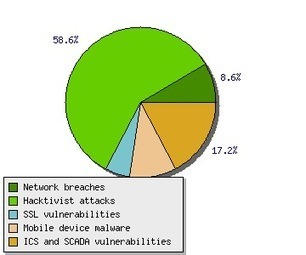
Tom Kellermann discusses the changes we can expect to see in 2013 The world has reached a point of inflection in cybercrime. As cyberspace abounds with cyber privateers, and many nations of the world become havens for these modern-day pirates, it appears that 2013 is the year of hacking for criminal gain. In our recently released predictions for 2013, our CTO Raimund Genes illustrated his strategic vision per the future of cybercrime. The predictions highlight improvements in threats we will encounter in 2013, more specifically on the attack vectors used by cybercriminals. Raimund predicts that attackers will shift their strategy from developing sophisticated malware to focusing on the means to infiltrate networks and evade detection.

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
” Mobile devices can expose users’ and
organizations’ valuable data to unauthorized people if
necessary precautions are not taken.

|
Scooped by
Gust MEES
|
The Security, Privacy and Legal Implications of BYOD
Some organizations believe that BYOD will allow them to avoid significant costs. Other companies believe that company data on personal devices is inevitable.
Unfortunately, BYOD raises significant data security and privacy concerns, which can lead to potential legal and liability risk. Many companies are having to play catch-up to control these risks. ===> This blogpost identifies and explores some of the key privacy and security legal concerns associated with BYOD, including “reasonable” BYOD security, BYOD privacy implications, and security and privacy issues related to BYOD incident response and investigations. <=== Read more...
SecurEnvoy revealed details of its latest release that gives users full flexibility of the device they use, while ensuring complete security to the organization. At the click of a button users can have their authentication token as an SMS on a mobile, an app on a smartphone or tablet, or a soft token on a laptop – with the ability to swap between devices at will. Read more...

|
Scooped by
Gust MEES
|
These posters are a great way to raise awareness about good online safety habits and tips. Our 10 posters offer helpful reminders about everything from keeping a long, strong password to making sure your software is up-to-date. We encourage you to download them, print them out and post them in your home, office, classroom community centers or religious establishments to get the word out! You can download the posters by clicking on a thumbnail image below or in our Resource Center. ===> Gust MEES: great initiative, use it, please! <===

|
Scooped by
Gust MEES
|
The explosion in development and adoption of smartphones and tablets for both personal and business use in the past two years is both a blessing and a curse to IT departments globally. Known as the Bring Your Own Device (BYOD) phenomenon, on one hand, there is an opportunity for greatly increased productivity and decreased costs. ===> On the other, there are increased security risks, management issues and even data and device ownership and governance issues. <===
Ignorance, as those in IT security know, is not bliss. And, two new studies when viewed together show that consumer ignorance of the consequences of their actions coupled with enterprises' unawareness of their computing environment equal unacceptable risk. ===> Many organizations unduly place themselves at risk by allowing access to their computers by mobile devices used by employees who download apps without understanding their consequences. That doesn't seems like a smart information risk management policy; actually, it doesn't seem like a policy at all. <===
|



 Your new post is loading...
Your new post is loading...





![Cisco: The Biggest Mobile BYOD Deployment Around? [Slides] | 21st Century Tools for Teaching-People and Learners | Scoop.it](https://img.scoop.it/979Kz0MNTSPBQDYgcyqzhzl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)











![Mobile Security Firm Analyzes 1.7 Million Android Apps [Infographic] | 21st Century Tools for Teaching-People and Learners | Scoop.it](https://img.scoop.it/-U8bVTIhWiIVeL-h7oriNjl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)










Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=WordPress
- http://www.scoop.it/t/wordpress-annotum-for-education-science-journal-publishing/?tag=WordPress-Security