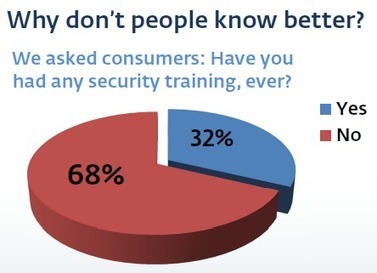
A new ESET study finds that only 1 in 10 consumers have had any classes or training about protecting their computer and/or their personal information during the last 12 months.
Indeed, a shocking 68 percent say they have never had any such training, ever. These and other findings, first revealed by ESET at the Virus Bulletin conference in Dallas, come just in time for National Cyber Security Awareness Month.
- http://www.staysafeonline.org/ncsam
Frankly, I find these numbers alarming in their implications for cybersecurity, the protection of the data streams that have become the lifeblood of our digital economy and our nation’s critical infrastructure. These findings also cast doubt on the perennial assertion by some experts that security problems mainly arise from the stupidity of users.
In light of these survey results it is worth asking whether the stupidity lies more with those who expect to achieve system security without providing any education on the subject to the people who use the systems.
===========================================
Gust MEES
There is a need for Cyber-Hygiene, please read my blog:
- http://gustmees.wordpress.com/2012/07/11/cyberhygiene-hygiene-for-ict-in-education-and-business/
===========================================
Read more, a MUST:
http://blog.eset.com/2012/10/10/study-finds-90-percent-have-no-recent-cybersecurity-training



 Your new post is loading...
Your new post is loading...


![Is Public WiFi Safe? [INFOGRAPHIC] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/vEEB7Lpb3JbEnTJ-E-kPzjl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)








![How to Be always Secured on Facebook [Infographic] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/hmAbxbrqPB27JWSWS_Ll6Tl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)








![Mobile Apps Permission - Find out what Your Apps are doing [Infographic] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/EYkwCdlFCGTI_RPr2huYnDl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)





