An average of 19 vulnerabilities per day were reported in 2014, according to the data from the National Vulnerability Database (NVD). In this article, I look at some of the trends and key findings for 2014 based on the NVD’s database.
.
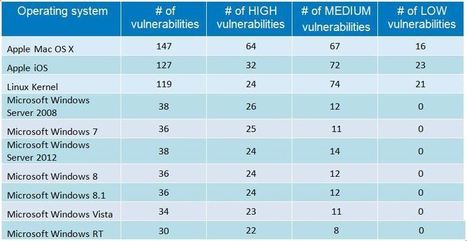
#Mac OS X and #Linux had more #vulnerabilities in 2014 than ALL #Windows Versions in sum.
.
Not surprisingly at all, web browsers continue to have the most security vulnerabilities because they are a popular gateway to access a server and to spread malware on the clients. Adobe free products and Java are the main challengers but web browsers have continuously topped the table for the last six years. Mozilla Firefox had the most vulnerabilities reported in 2009 and 2012; Google Chrome in 2010 and 2011; Internet Explorer was at the top for the last two years.
To keep systems secure, it is critical that they are fully patched. IT admins should focus on (patch them first):
- Operating systems (Windows, Linux, OS X)
- Web browsers
- Java
- Adobe free products (Flash Player, Reader, Shockwave Player, AIR).
.
Learn more:
.
.



 Your new post is loading...
Your new post is loading...








par Stéphane Larcher, le 23 février 2015 16:16
La National Vulnerability Database vient de publier les chiffres pour 2014. Contrairement aux idées reçues, Windows (toutes versions confondues) s’est révélé moins vulnérable que Mac OS X, iOS ou Linux. Toutefois, Microsoft n’a pas non plus de raison de pavoiser car Internet Explorer est l’application la plus vulnérable, très loin devant les autres.