Of the many weapons and tricks in an attacker’s arsenal, none is more dangerous or insidious than the ability to hide and continuously compromise a system from within.
This is the role of a rootkit. Malware uses rootkits, or rootkit functionality, in order to hide their presence on an affected computer and thus impede their removal.
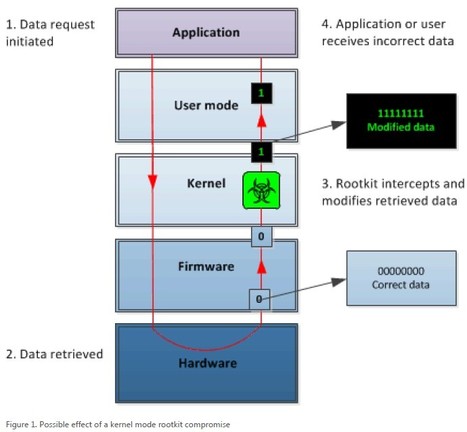
===> Once compromised by a rootkit, any information returned by an affected system can no longer be trusted and must be regarded as suspect (which is exactly how they hide themselves and their components from you - by modifying requests for information that might give them away). <===
===> Know your enemy and protect yourself by learning about these threats. <===
You can download the paper here [PDF]:
Read more:



 Your new post is loading...
Your new post is loading...