The Equation Group's attack on hard-drive firmware is one of the most advanced ever discovered, Kaspersky Lab said.
A cyberespionage group with a toolset similar to ones used by U.S. intelligence agencies has infiltrated key institutions in countries including Iran and Russia, utilizing a startlingly advanced form of malware that is impossible to remove once it's infected your PC.
Kaspersky Lab released a report Monday that said the tools were created by the “Equation” group, which it stopped short of linking to the U.S. National Security Agency
.
The tools, exploits and malware used by the group—named after its penchant for encryption—have strong similarities with NSA techniques described in top-secret documents leaked in 2013.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=REGIN
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Warriorpride
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Quantum
- http://www.scoop.it/t/securite-pc-et-internet/?tag=cyberwar
- http://www.scoop.it/t/securite-pc-et-internet/?tag=NSA
- http://www.scoop.it/t/securite-pc-et-internet/?tag=TAO



 Your new post is loading...
Your new post is loading...















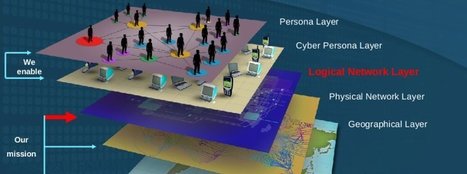


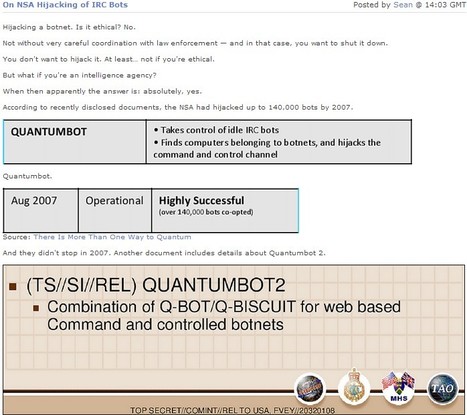










The Equation Group's attack on hard-drive firmware is one of the most advanced ever discovered, Kaspersky Lab said.
A cyberespionage group with a toolset similar to ones used by U.S. intelligence agencies has infiltrated key institutions in countries including Iran and Russia, utilizing a startlingly advanced form of malware that is impossible to remove once it's infected your PC.
Kaspersky Lab released a report Monday that said the tools were created by the “Equation” group, which it stopped short of linking to the U.S. National Security Agency
.
The tools, exploits and malware used by the group—named after its penchant for encryption—have strong similarities with NSA techniques described in top-secret documents leaked in 2013.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=REGIN
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Warriorpride
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Quantum
- http://www.scoop.it/t/securite-pc-et-internet/?tag=cyberwar
- http://www.scoop.it/t/securite-pc-et-internet/?tag=NSA
- http://www.scoop.it/t/securite-pc-et-internet/?tag=TAO
- https://gustmees.wordpress.com/2012/05/21/visual-it-securitypart2-your-computer-as-a-possible-cyber-weapon/