Hackers may not be who we think they are. In fact, you might be a hacker and not even know it. Learn the true meaning of hacking and some of the many reasons...
Get Started for FREE
Sign up with Facebook Sign up with X
I don't have a Facebook or a X account
 Your new post is loading... Your new post is loading...
 Your new post is loading... Your new post is loading...
|

Gust MEES's curator insight,
April 16, 2013 8:54 AM
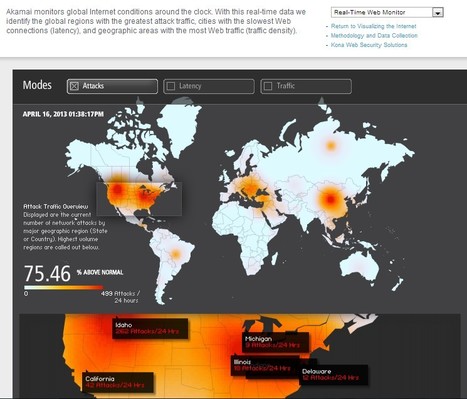
Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?tag=SHODAN+Search+Engine http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=Internet+of+Things http://www.scoop.it/t/securite-pc-et-internet/?tag=smart-TV http://www.scoop.it/t/securite-pc-et-internet/?tag=Internet+of+things http://www.scoop.it/t/securite-pc-et-internet/?tag=Cars Check this and become conscious about the importance of Cyber-Security!!!
Check also:
- https://gustmees.wordpress.com/
- https://gustmeesen.wordpress.com/
- https://gustmeesfr.wordpress.com/
|











Interesting video