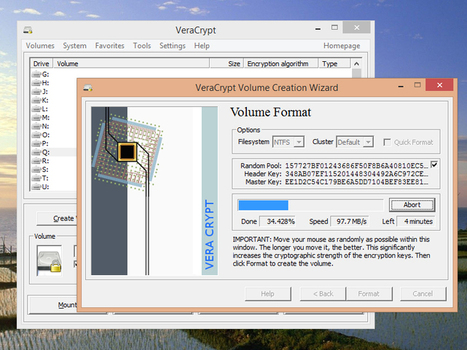
VeraCrypt ist ein neues Verschlüsselungsprogramm, das besser und sicherer sein will, als TrueCrypt.
VeraCrypt
Mit VeraCrypt betritt eine neue Verschlüsselungs-Software den Markt, die verspricht vollkommen sicher zu sein. Sie setzt zwar auf dem laut den eigenen Machern unsicheren TrueCrypt auf, wurde aber an den entscheidenden Stellen verbessert und soll immun gegen Brute-Force-Attacken sein. Verschlüsseln Sie Ihre Daten um gegen Schnüffeleien seitens Regierungen, Privatpersonen oder Konzernen gewappnet zu sein.
Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=ENCRYPTION



 Your new post is loading...
Your new post is loading...


















Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=ENCRYPTION