 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
|
Zombiecomputer und wie Sie sie vermeiden:
Sie haben wahrscheinlich das Wort Botnetz in letzter Zeit mehr als einmal gehört, und das überrascht kaum. Jedes verbundene Gerät kann zombifiziert werden — und Teil eines Botnetzes werden. Das schließt PCs, Smartphones, Tablets, Router, WLAN-Kühlschränke, Smart Toys und viele andere Geräte ein.
In diesem Post erklären wir, was ein Botnetz ist, was es anrichtet und wie Sie Ihre Geräte davor schützen, Teil eines Botnetzes zu werden.
Botnetze: Was sind sie?
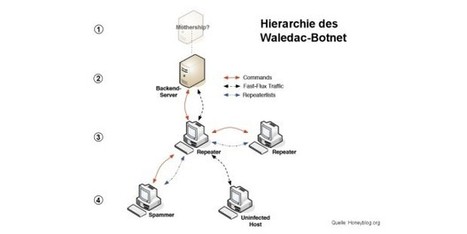
Ein Botnetz ist eine Gruppe von Geräten, die mit dem Internet verbundenen sind und mit einer bestimmten Malware infiziert wurden. Die Art von Malware, die Bots, oder Zombies, erstellt, arbeitet verdeckt, erwirbt Administratorenrechte und übergibt den Cyberkriminellen die Kontrolle, ohne sich zu verraten. Das infizierte Gerät funktioniert wie gewöhnlich – aber es folgt auch gleichzeitig den Anweisungen des Kommandeurs des Botnetzes. Zusammen bilden die infizierten Geräte eine starke Infrastruktur, mit der Cyberverbrechen begangen werden können.
Einige Botnetzkommandeure spezialisieren sich nur auf den Support und die Verbreitung des Botnetzes. Sie vermieten diese schädlichen Tools an andere Kriminelle, die mit ihnen Angriffe und andere kriminale Taten durchführen. Hier sind die vier gängigsten Wege, um ein Botnetz zu verwenden. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=Botnet http://www.scoop.it/t/21st-century-learning-and-teaching/?&tag=Botnet https://twitter.com/search?src=typd&q=%23fscd

|
Scooped by
Gust MEES
|
Botnets
Botnets have existed for at least a decade. As early as 2000, hackers were breaking into computers over the Internet and controlling them en masse from centralized systems. Among other things, the hackers used the combined computing power of these botnets to launch distributed denial-of-service attacks, which flood websites with traffic to take them down.
But now the problem is getting worse, thanks to a flood of cheap webcams, digital video recorders, and other gadgets in the "Internet of things." Because these devices typically have little or no security, hackers can take them over with little effort. And that makes it easier than ever to build huge botnets that take down much more than one site at a time. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=Botnet

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
CIRCL » Botfree.lu - Luxembourg anti-botnet support - ACDC Luxembourg support center
Botfree.lu - Luxembourg anti-botnet support - ACDC Luxembourg support center Infected systems are often part of a botnet which can be controlled remotely by attackers to perform criminal activities like attacking other computers, send malicious emails or perform denial-of-service attack. My PC is infected and I’m looking for support If you have a strong suspicion that your machine is infected and you are looking for support to reinstall the system, you can check the PC-doctor list to find a SME to support you. I received a malicious or suspicious link Phishing link can be directly tested and reported via the CIRCL urlabuse interface. I have a security incident in my company If you have a security incident in your company, you can report it to CIRCL.

|
Scooped by
Gust MEES
|
Massive Qbot Botnet strikes 500,000 Machines Through WordPress. Attackers steal banking credentials and hire out compromised computers to others

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Legitimate sites forced to aid criminals' illicit botnet operations
Hackers have hijacked more than 162,000 legitimate WordPress sites, connecting them to a criminal botnet and forcing them to mount distributed denial-of-service (DDoS) attacks, according to security firm Sucuri.
Sucuri CTO Daniel Cid said the company uncovered the botnet when analysing an attack targeting one of its customers. Cid said Sucuri managed to trace the source of the attack to legitimate WordPress sites. "The most interesting part is that all the requests were coming from valid and legitimate WordPress sites. Yes, other WordPress sites were sending random requests at a very large scale and bringing the site down," read the blog.

|
Scooped by
Gust MEES
|
Security researchers at Proofpoint have uncovered the very first wide-scale hack attack that involved television sets and at least one refrigerator.

|
Scooped by
Gust MEES
|
Principal Security experts are confident that in the next months we will assist to the explosion for Android botnets and in general of mobile cyber threats.
An ongoing brute-force attack on WordPress-based websites has compromised more than 90,000 blogs, but there are simple ways to make sure your blog won't be next to fall.

|
Scooped by
Gust MEES
|
According to Sucuri, WordPress administrators who have been hacked should strongly consider taking the following steps to eradicate the intruders and infections: - Log in to the administrative panel and remove any unfamiliar admin users (the first step after the attackers get in is to add a new user). - Change all passwords for all admin users (and make sure all legitimate accounts are protected with strong passwords this time!) - Update the secret keys inside WordPress, otherwise any rogue admin user can remain logged in. ===> Reinstall WordPress from scratch or revert to a known, safe backup. <===

|
Scooped by
Gust MEES
|
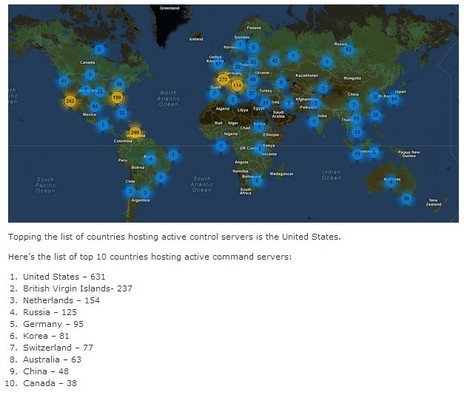
The U.S. hosts 631 active commandandcontrol hubs for botnets, according to McAfee. Runner-up hosts included the British Virgin Islands, with 237, and the Netherlands, hosting 154.

|
Scooped by
Gust MEES
|
McAfee Labs has long monitored botnet activities and their control servers as they plague the Internet. With millions of McAfee endpoints and network security appliances sending information to McAfee Global Threat Intelligence (GTI) in the cloud, coupled with a vast collection of malicious binary and proactive research, McAfee Labs has a clear view of botnet threats around the world.
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Today, half of America’s internet shut down when hackers unleashed a large distributed denial of service (DDoS) attack on the servers of Dyn, a major DNS host. It’s still unclear exactly who carried out the attack and why, but regardless, the event served as a demonstration of how easily large swaths of the web can be wiped out if attacked by determined hackers. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=Internet+of+Things

|
Scooped by
Gust MEES
|
The Simda botnet, believed to have infected more than 770,000 computers worldwide, has been targeted in a global operation.
In a series of simultaneous actions around the world, on Thursday 9 April, 10 command and control servers were seized in the Netherlands, with additional servers taken down in the US, Russia, Luxembourg and Poland.
The operation involved officers from the Dutch National High Tech Crime Unit (NHTCU) in the Netherlands, the Federal Bureau of Investigation (FBI) in the US, the Police Grand-Ducale Section Nouvelles Technologies in Luxembourg, and the Russian Ministry of the Interior’s Cybercrime Department “K” supported by the INTERPOL National Central Bureau in Moscow.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Botnet

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
F-Secure Security Labs brings you the latest online security news from around the world. Ensure that you are up-to-date with the latest online threats to guarantee your online wellbeing.

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
In late May we reported on the details of Backdoor.AndroidOS.Obad.a, the most sophisticated mobile Trojan to date. At the time we had almost no information about how this piece of malware gets onto mobile devices.

|
Scooped by
Gust MEES
|
Instead of being used as spam during DDoS attacks, botnets are now used to bring down enterprise apps, leaving the more connected countries more vulnerable, according to Barracuda Networks.
There is a lot of interesting discussion going on at the moment across the interwebs on the intention of the latest string of Brute Force attacks, much of which That finding comes from Arbor Networks, which said that attackers had compromised numerous PHP Web applications, such as Joomla, as well as many WordPress sites, many of which were using an outdated version of the TimThumb plug-in. After compromising the sites, attackers then loaded toolkits onto the sites that turned them into DDoS attack launch pads. – Information Week Security

|
Scooped by
Gust MEES
|
70% of those infections communicate with their C&C servers at least once every two hours, and more than half of organizations across the globe have had malware downloaded onto their networks via these bots.

|
Scooped by
Gust MEES
|
Microsoft annonce avoir fermé un nouveau botnet en collaboration avec Symantec et affectant les requêtes des internautes sur les moteurs de recherche.
Sur l'un de ses blogs officiels, Microsoft explique que le botnet en question, Bamital, était constitué d'environ huit millions d'ordinateurs zombies. Ces derniers étaient infectés d'un malware modifiant les liens cibles au sein des moteurs de recherche. Ce click jacking était opéré sur Google, Bing et Yahoo! ainsi que sur leurs plateformes publicitaires.
|



 Your new post is loading...
Your new post is loading...















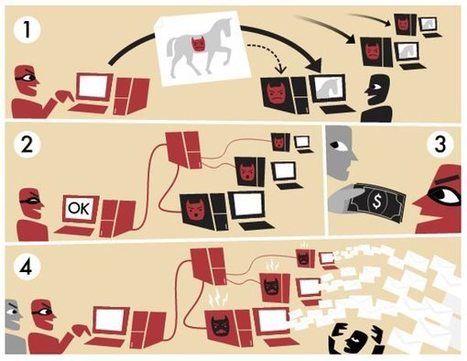








Zombiecomputer und wie Sie sie vermeiden:
Sie haben wahrscheinlich das Wort Botnetz in letzter Zeit mehr als einmal gehört, und das überrascht kaum. Jedes verbundene Gerät kann zombifiziert werden — und Teil eines Botnetzes werden. Das schließt PCs, Smartphones, Tablets, Router, WLAN-Kühlschränke, Smart Toys und viele andere Geräte ein.
In diesem Post erklären wir, was ein Botnetz ist, was es anrichtet und wie Sie Ihre Geräte davor schützen, Teil eines Botnetzes zu werden.
Botnetze: Was sind sie?
Ein Botnetz ist eine Gruppe von Geräten, die mit dem Internet verbundenen sind und mit einer bestimmten Malware infiziert wurden. Die Art von Malware, die Bots, oder Zombies, erstellt, arbeitet verdeckt, erwirbt Administratorenrechte und übergibt den Cyberkriminellen die Kontrolle, ohne sich zu verraten. Das infizierte Gerät funktioniert wie gewöhnlich – aber es folgt auch gleichzeitig den Anweisungen des Kommandeurs des Botnetzes. Zusammen bilden die infizierten Geräte eine starke Infrastruktur, mit der Cyberverbrechen begangen werden können.
Einige Botnetzkommandeure spezialisieren sich nur auf den Support und die Verbreitung des Botnetzes. Sie vermieten diese schädlichen Tools an andere Kriminelle, die mit ihnen Angriffe und andere kriminale Taten durchführen. Hier sind die vier gängigsten Wege, um ein Botnetz zu verwenden.
Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/securite-pc-et-internet/?&tag=Botnet
http://www.scoop.it/t/21st-century-learning-and-teaching/?&tag=Botnet
https://twitter.com/search?src=typd&q=%23fscd