Dr. Peter Lokhorst is Managing Director of InfoSecure BV, which is currently in seven countries and provides awareness training programs to international clients including Procter & Gamble, European Central Bank, Deutsche Telecom and Bayer.
What you want is a change in behavior of individuals and a cultural change in the company as a whole. To achieve this goal, you must repeatedly confront employees with possible threats and show them best practices.
Also, the role of the managers is crucial. It is important to train trainers in their role and be sure that they practice good behavior on a day-to-day basis. Safety is not about knowledge in most cases, but it is all about “awareness” in the true sense of the word.
You only reach a higher level of awareness if safety is an issue that repeatedly is discussed and addressed.



 Your new post is loading...
Your new post is loading...









![How to keep your business safe – the one checklist all SMBs should have [Infographic] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/Sn5HIth7pKg7GHGiGeIaXzl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)

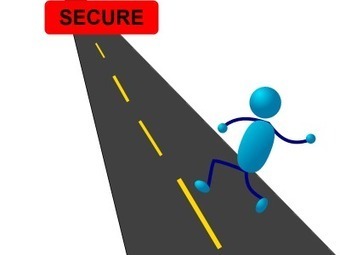














par Stéphane Larcher, le 23 février 2015 16:16
La National Vulnerability Database vient de publier les chiffres pour 2014. Contrairement aux idées reçues, Windows (toutes versions confondues) s’est révélé moins vulnérable que Mac OS X, iOS ou Linux. Toutefois, Microsoft n’a pas non plus de raison de pavoiser car Internet Explorer est l’application la plus vulnérable, très loin devant les autres.