Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
|
What’s happened? Earlier this week someone anonymously published a key piece of Apple’s iOS source code onto GitHub. Which bit of iOS was it? It was an integral part of iOS known as “iBoot” – the section of code which controls the security of your iPhone or iPad as it starts up. So it’s an important part of iOS? Very important and highly sensitive. The secure boot firmware ensures that iOS will only run apps digitally signed by Apple, and checks that the operating system has not been tampered with by a hacker. Does that make this leak interesting to hackers? Yes, and to other parties (I’m looking at you principally law enforcement agencies) who might be interested in finding vulnerabilities that could be exploited to help them compromise and unlock iOS devices. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
Un utilisateur d’Open Radar a découvert un petit souci dans macOS 10.13.2. Il permet à un administrateur local de modifier les préférences systèmes du Mac App Store en saisissant n’importe quel mot de passe.
Sale temps pour la sécurité sur macOS. Le dernier bug de sécurité en date n’est pas du niveau des précédents mais fait malgré tout un peu tache sur le CV d’Apple. Un utilisateur d’Open Radar, une communauté de rapporteurs de bugs, a révélé un petit souci dans macOS High Sierra 10.13.2, la dernière version officiellement disponible.
Ainsi, selon lui, n’importe quel utilisateur administrateur local sur la machine peut ouvrir le panneau des Préférences Système du Mac App Store et déverrouiller le cadenas qui empêche les modifications de ces réglages en saisissant n’importe quel mot de passe. Si le cadenas est déjà ouvert et que cet utilisateur souhaite tenter sa chance, c’est possible. Il suffit de le refermer, de l’ouvrir à nouveau et de taper n’importe quelle suite de lettres ou chiffres. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
05.01.2018 - 01:50 Uhr
Durch eine massive Sicherheitslücke in den Computerchips von Milliarden Geräten können auf breiter Front vertrauliche Daten abgeschöpft werden.
Jetzt hat Apple bestätigt, dass auch „alle Mac-Systeme und iOS-Geräte betroffen sind“. Im Klartext: Jeder Apple-Computer, jedes iPhone und jedes iPad könnte von Hackern angegriffen werden. Bislang seien aber keine solche Attacken bekannt, erklärt Apple in einem Hilfe-Dokument.
Was müssen Besitzer von Apple-Geräten wissen?
Nach Angaben des Unternehmens wurde eines der beiden möglichen Angriffsszenarien („Meltdown“) bereits mit Aktualisierungen seiner Betriebssysteme abgestellt. Auf Geräten, die mit iOS 11.2, MacOS 10.13.2 bzw. tvOS 11.2 arbeiten, soll diese Angriffsmöglichkeit nicht mehr möglich sein.
Mit einem Update für den Internet-Browser Safari solle in den nächsten Tagen auch das Angriffsszenario „Spectre“ verhindert werden. Die Apple Watch ist laut Apple nicht von der Sicherheitslücke betroffen, benötigt daher keine Aktualisierung.
Apple empfiehlt außerdem dringend, Apps oder Programme ausschließlich aus sicheren Quellen wie dem eigenen App-Store zu laden. Andernfalls laufe man Gefahr, gefährliche Spionagesoftware aufs eigene Gerät zu holen. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Meltdown+and+Spectre+Attacks https://gustmeesde.wordpress.com/2014/12/26/programme-die-auf-jeden-neuen-pc-und-smartphones-gehoren/ https://gustmeesde.wordpress.com/2014/12/16/browser-sind-das-einfallstor-fur-malware-sind-eure-browser-up-to-date/

|
Scooped by
Gust MEES
|
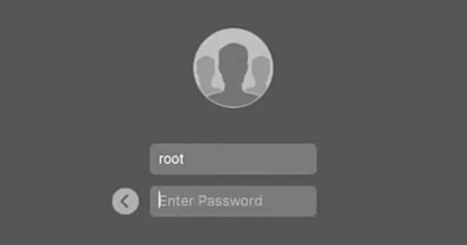
Apple released a security update Wednesday to fix a major bug that allowed anyone to bypass security protocols and act as a computer's administrator.
"Security is a top priority for every Apple product, and regrettably we stumbled with this release of macOS," a spokesperson for Apple said in a statement. "When our security engineers became aware of the issue Tuesday afternoon, we immediately began working on an update that closes the security hole."
The security issue impacted macOS High Sierra 10.13.1. Apple says the update is now available for download and will be rolled out automatically to all systems running the affected software.
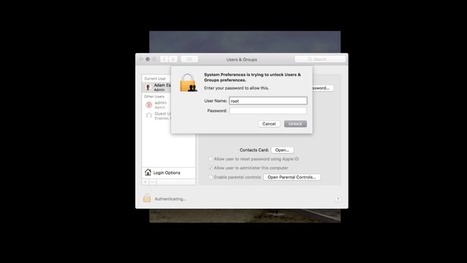
On Tuesday, developers noticed that someone with access to a Mac computer running Apple's most recent Mac software could type "root" and no password in the Users & Groups section of System Preferences and gain administrator-level access to the computer.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
Want to have god-like powers over a Mac? Just enter your username as root... no password required. But an attacker needs to have physical access to a Mac computer in order to exploit this flaw?Not so fast. For instance, security researcher Patrick Wardle reports that it is possible to exploit the flaw remotely. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
What’s the maddest, baddest, craziest, can-you-believe-it, how-did-that-happen security blunder of recent memory?
Companies contending for the top three spots in the past quarter surely include:
Uber. Suffered a breach, paid the hackers off, pretended it never happened, got found out anyway.
Equifax. Personal data including social security numbers for about half of US adults carried off by crooks.
Apple. When connecting an encrypted device, [Show password hint] would reveal the password itself.
Well, Apple just did it again, and this one is even worse that before – so Cupertino may well be back in first place.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
THERE ARE HACKABLE security flaws in software. And then there are those that don't even require hacking at all—just a knock on the door, and asking to be let in. Apple's macOS High Sierra has the second kind.
On Tuesday, security researchers disclosed a bug that allows anyone a blindingly easy method of breaking that operating system's security protections. Anyone who hits a prompt in High Sierra asking for a username and password before logging into a machine with multiple users, they can simply type "root" as a username, leave the password field blank, click "unlock" twice, and immediately gain full access.
In other words, the bug allows any rogue user that gets the slightest foothold on a target computer to gain the deepest level of access to a computer, known as "root" privileges. Malware designed to exploit the trick could also fully install itself deep within the computer, no password required. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
VIETNAMESISCHE SICHERHEITSFORSCHER:
Neue Maske soll iPhone X sofort entsperren
Die Maske, mit denen Forscher des vietnamesischen Anbieters Bkav ein iPhone X überlistet haben, ist überarbeitet worden. Die neue Version soll die Entsperrung über Face ID ermöglichen, ohne dass das iPhone X angelernt werden muss.
Mitarbeiter des vietnamesischen Sicherheitsanbieters Bkav wollen mit einer neuen Maskenversion Apples Face ID leichter als bisher überlisten können und warnen davor, die Gesichtserkennung im geschäftlichen Bereich zu nutzen - weil diese so unsicher sei.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security/?&tag=Face-ID

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
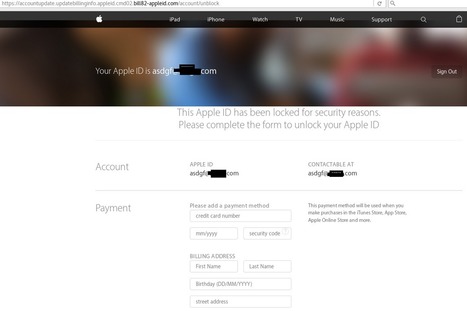
Mit gefälschten E-Mails und Webseiten wollen Kriminelle Zugangsdaten von Apple-Nutzern erschleichen. Die Phishing-Seiten setzen auf "gute Optik" und geben sich durch https-Verschlüsselung einen seriösen Anschein, warnt die Polizei Niedersachsen. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
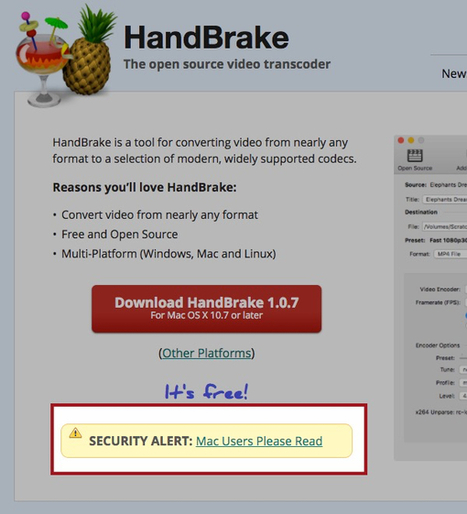
A mirror download server for the popular tool HandBrake video file-transcoding app has been compromised by hackers, who replaced its Mac edition with malware.
The first most Mac users will know about the security incident will be when they visit the app’s website, at https://handbrake.fr, and see a link to a “Security Alert”: Anyone who has downloaded HandBrake on Mac between [02/May/2017 14:30 UTC] and [06/May/2017 11:00 UTC] needs to verify the SHA1 / 256 sum of the file before running it. Anyone who has installed HandBrake for Mac needs to verify their system is not infected with a Trojan. You have 50/50 chance if you’ve downloaded HandBrake during this period. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security/?&tag=HandBrake http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
In the big picture, which operating systems attract more malware is beside the point. Windows may be targeted more often, but if you’re the Mac user who gets victimized by tainted code, the tally doesn’t matter. For Mac users, the important thing is to raise awareness of the threats they face and explain what they can do about it.
Below is a look at the Mac malware SophosLabs has intercepted, analyzed and protected customers against, followed by recent issues Naked Security has written about. From there, we look at some tips to ensure better protection.
View from the lab
Mac malware has been studied at length by SophosLabs, and in a 2017 malware forecast released last month, it warned that more threats are coming, including several varieties of ransomware. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
|

|
Scooped by
Gust MEES
|
A security researcher has revealed details of a new piece of undetectable malware targeting Apple's Mac computers—reportedly first macOS malware of 2018.
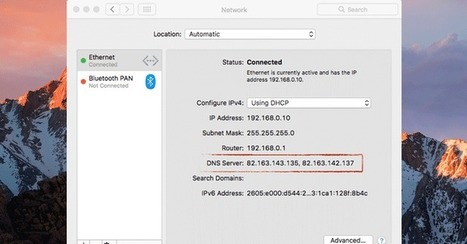
Dubbed OSX/MaMi, an unsigned Mach-O 64-bit executable, the malware is somewhat similar to DNSChanger malware that infected millions of computers across the world in 2012.
DNSChanger malware typically changes DNS server settings on infected computers, allowing attackers to route internet traffic through malicious servers and intercept sensitive information.
First appeared on the Malwarebytes forum, a user posted a query regarding unknown malware that infected his friend's computer that silently changed DNS settings on infected macOS to 82.163.143.135 and 82.163.142.137 addresses. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
Apple has issued a statement regarding the Meltdown and Spectre vulnerabilities, confirming all Mac systems and iOS devices are affected, but saying there are no known exploits impacting customers at this time.
The iPhone maker has already released mitigations in iOS 11.2, macOS 10.13.2, and tvOS 11.2 to help defend against Meltdown. A spokesperson confirmed Friday that Apple Watch is not affected by either Meltdown or Spectre, despite its own initial report Thursday.
"In the coming days we plan to release mitigations in Safari to help defend against Spectre," the company said in a statement. "We continue to develop and test further mitigations within the operating system for the Spectre techniques, and will release them in upcoming updates of iOS, macOS, and tvOS." Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Meltdown+and+Spectre+Attacks https://gustmeesde.wordpress.com/2014/12/26/programme-die-auf-jeden-neuen-pc-und-smartphones-gehoren/ https://gustmeesde.wordpress.com/2014/12/16/browser-sind-das-einfallstor-fur-malware-sind-eure-browser-up-to-date/

|
Scooped by
Gust MEES
|
At first, the Twitter user who publicised this flaw was criticised by some people, who considered his tweet to be “irresponsible disclosure”, because it told the world about a problem that it might have been better to tell Apple about privately first so the hole could be closed and then announced.
But others soon realised that this was not a brand new discovery – indeed, it had been discussed more than two weeks ago on Apple’s on support forum.
Apple’s official policy of saying nothing about security issues until a fix is out meant that there wasn’t much to go on once the news broke, except to assume that the company was frantically coding up a fix…
…and, fortunately that turns out to have been true. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
In der aktuellen macOS-Version High Sierra steckt eine Sicherheitslücke, die Beobachter sprachlos macht: Mit wenigen Klicks können Angreifer sich root-Rechte verschaffen - weil Apple dafür kein Passwort verlangt.
Schon vor einigen Wochen fiel macOS High Sierra, die aktuelle Version des Apple-Betriebssystems, durch einen abstrusen Bug auf: Das Passwort verschlüsselter Festplatten kopierte das Betriebssystem kurzerhand in den Passwort-Hinweis und machte es damit für jeden sichtbar. Wer damals dachte, viel schlimmer kann es nicht kommen, hat sich getäuscht: In einer jetzt entdeckten Sicherheitslücke verlangt Apple an kritischen Punkten einfach überhaupt kein Passwort mehr. Angreifer können sich mit wenigen Klicks vollen Zugriff auf den Computer sichern.
Öffentlich wurde der eklatante Bug durch einen Tweet. Der Entwickler Lemi Orhan Ergin beschreibt darin das Vorgehen, mit dem sich Dritte auf einem Mac root-Rechte verschaffen können, ohne dafür ein Passwort zu benötigen. Mit diesen Rechten ist es möglich, den Mac vollständig zu übernehmen.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
Sicherheitsexperten haben eine gigantische Lücke im neuen Apple-Betriebsystem Mac OS High Sierra entdeckt!
Laut einem Bericht des Magazin „Wired“ lässt sich die Abfrage von Nutzername und Passwort mit einem erschreckend einfachen Trick umgehen: Statt des Nutzernamens tippt man lediglich das Wort „root“ ein, lässt das Passwort-Feld leer, drückt mehrfach die Eingabetaste – und erhält vollständigen Zugriff auf das Gerät.
Dann sei es jedem Angreifer mit Zugang zu einem solchen Computer möglich, in die tiefsten Systemeinstellungen vorzudringen.
Beim Kurznachrichtendienst Twitter zeigen gleich mehrere Nutzer, wie simpel sich die Passwortabfrage aushebeln lässt.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
In software, there are bugs, and there are dangerous bugs. It looks like macOS High Sierra has one of those dangerous bugs; one that could give someone full access to virtually any user account. And holy buckets, it is scary. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
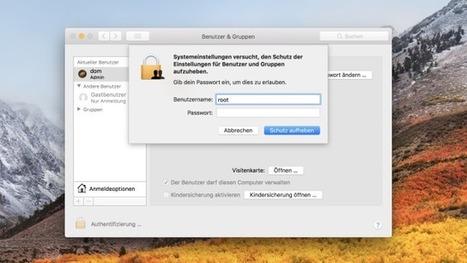
Apple, Apple, Apple. What are we going to do with you? In your most recent High Sierra macOS release, it turns out you've given a way for any local user to take over a Mac -- lock, stock, and two smoking barrels.
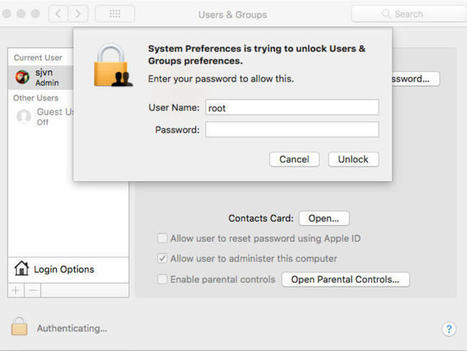
This exploit doesn't require any mad NSA-type hacker skillz. All you have to do is go to System Preferences, then Users and Groups, and click the lock to make changes. Then, enter "root" as your username without a password. Shazam! You're in.
As on any Unix/Linux-based system, the root user can control all administration functions and can read and write to any file system, including those of other users. In theory, root is disabled on Apple systems unless expressly authorized. Wrong!
Once in, you can edit your own permissions. For example, want to give yourself administrator privileges? Sure! Or, you can set up new administration-level accounts. Once you've done that, you can do anything your heart desires within the system. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Macs are becoming an increasingly big target for malware authors, and a new report has pointed to a massive increase this year in the likes of viruses aimed at Apple’s machines (which were once regarded as relative safe havens in comparison to Windows PCs).
The findings from Malwarebytes show that as of July 2017, there has been a huge leap of 230% in Mac malware compared to the previous year.
Some categories of malicious software are increasing at an even faster rate than this, namely adware and potentially unwanted programs (PUPs) according to the security firm, although it didn’t clarify any percentage rates in these cases.
Malwarebytes also observed that the Mac App Store is currently awash with a ‘tidal wave’ of scam software.
As Betanews reports, the authors of the study looked to the future, predicting that: “In 2018, Mac malware will increase but PUPs will see the largest growth. These are not very well policed and are free to proliferate unchecked.
“Mac users are already experiencing some of this now, with an explosion of fake anti-virus apps in the Mac App Store. These are not well controlled by Apple and not commonly known of even within the security community.” Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
Quoi de mieux pour piéger l'utilisateur de se faire passer pour une source légitime ? Des pirates ont ainsi réussi à s'introduire dans les serveurs de l'éditeur d'Handbrake et ont remplacé le logiciel d'encodage vidéo par une version piégée. Du coup, entre le 2 et le 6 mai dernier, si vous avez téléchargé (ou mis à jour) l'application vous avez toutes les chances (une chance sur deux pour être précis) d'avoir obtenu une version corrompue avec un joli malware en cadeau (OSX.PROTON). Afin de vérifier si son Mac est infecté, il suffit d’ouvrir le Moniteur d’activité (localisé dans le dossier 'Utilitaires' d’Applications) et de regarder si le processus 'activity_agent' est en cours d’exécution. Si tel est le cas, cela veut dire que le malware est actif sur la machine. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security/?&tag=HandBrake http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
A malware research team has discovered a new piece of Mac malware that reportedly affects all versions of MacOS and is signed with a valid developer certificate authenticated by Apple (via The Hacker News).
The malware has been dubbed "DOK" and is being disseminated through an email phishing campaign which researchers at CheckPoint say is specifically targeting macOS users, making it the first of its kind.
The malware works by gaining administration privileges in order to install a new root certificate on the user's system. This enables it to gain access to all communications between the host Mac and the internet, including traffic flowing through connections encrypted with SSL. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
Auch in diesem Jahr war mit Safari und macOS zwei Apple Produkte vertreten. Wissenschaftler haben es sich seit jeher zur Aufgabe gemacht, sogenannte 0-day (Zero-Day- oder “Tag-Null”-) Lücken zu finden. Diese werden so genannt, da kein Hersteller davon etwas weiß, und es dafür noch keinen Patch oder Aktualisierung gibt. Das macht sie besonders gefährlich: Solche Lücken können ungestört von Angreifern ausgenutzt werden, um Computer-Systeme zu übernehmen, ohne das jemand etwas mitbekommt.
Stattliche Preisgelder
Nicht von ungefähr kommen daher stattliche Preisgelder und Auszeichnungen. Summen in Höhe von 50.000 Dollar sind keine Seltenheit. Für ganz knifflige Angriffe werden sogar bis zu 100.000 Dollar ausbezahlt. Das Geld wird meist von Forschungseinrichtungen eingesetzt um weiter arbeiten zu können.
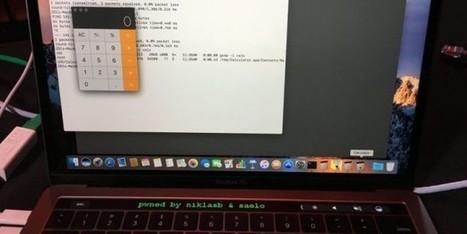
Über den Safari in die Touch Bar
Die Touch Bar war auch auf der Sicherheitskonferenz in aller Munde. Angreifer konnten nämlich durch einen Fehler im Apple eigene Browser Safari eine Lücke ausnutzen, um sich so Root-Rechte unter macOS zu verschaffen. Mit diesen haben die Wissenschaftler eine Nachricht auf der Touch Bar platziert, um ihren Angriff und die Sicherheitslücke zu beweisen. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security https://gustmees.wordpress.com/2012/05/02/get-smart-with-5-minutes-tutorialsit-securitypart-1-browsers/ https://gustmees.wordpress.com/2013/04/22/i-got-interviewed-feeling-honored/
|



 Your new post is loading...
Your new post is loading...







![[Infographic] More Mac malware than ever before | #Apple #CyberSecurity #Awareness | Apple, Mac, MacOS, iOS4, iPad, iPhone and (in)security... | Scoop.it](https://img.scoop.it/zVWZk_6Mb_tevX9qigIDITl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)