 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
|
Researchers at BAE just reported on a Mac bot known as OSX/Agent-ANTU that was allegedly distributed in a novel way.
The crooks used a security hole in a controversial Mac security and cleanup utility called MacKeeper.
MacKeeper quickly patched the hole after it became known, but until you received the update you were at risk of a Remote Code Execution (RCE) hole.
As long as you were unpatched, a crook could simply entice or redirect you to a poisoned website, and use a single line of JavaScript to send a command script to MacKeeper, which would then run it.
Unfortunately, according to BAE, some crooks struck while the iron was hot.
The crooks sent unpatched MacKeeper users to a web page that tricked their Macs into downloading the OSX/Agent-ANTU malware.
Here are some examples we've seen over the years where the Windows malware "playbook" has been followed, in some cases extremely effectively, on OS X:
2012: Java-based exploit. The Flashback malware was injected onto your Mac via an unpatched Java bug. Flashback was a bot, or zombie, meaning that crooks could remotely send it instructions to help them commit further cybercrime. Estimates suggest that more than 600,000 Macs ended up infected, supposedly including "274 from Cupertino."
2013: Word-based exploit. SophosLabs reported on attackers using an exploitable bug in Microsoft Word for Mac to target Chinese minority groups. If you opened a booby-trapped document, disguised as some sort of political commentary, the crooks got control of your Mac via zombie malware called OSX/Agent-AADL.
2014: Fake "undelivered item" documents. If you opened the bogus PDF file, really an application in disguise, you could end up infected with a data-stealing Trojan called OSX/LaoShu-A. Amongst other things, this one would find files such as documents, spreadsheets, presentations and archives...and send them to the crooks.
Learn more:
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
CyberSecurity Researchers have uncovered around 25,000 iOS apps that use old versions of a popular networking library, leaving them open to attackers on the same network viewing encrypted traffic.
The bug affects Secure Sockets Layer (SSL) code in AFNetworking, a networking library developers can use to build components of iOS apps. The framework has been updated three times in the past six weeks, addressing numerous SSL flaws that leave apps vulnerable to man-in-the-middle attacks.

|
Scooped by
Gust MEES
|
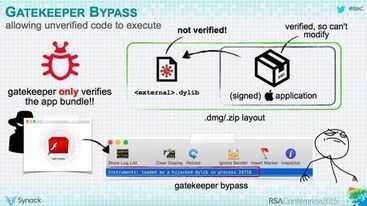
« Les virus sous Mac, ça n’existe pas ! », répète à qui veut l'entendre un vieux fond de sagesse informatique des nations. Le chercheur en sécurité Patrick Wardle, de la société Synack, vient de démontrer le contraire à l’occasion de la RSA Conference, qui se tient actuellement à San Francisco. L’homme a passé en revue tous les mécanismes de protection qu’Apple a intégrés récemment dans son système. Conclusion : tous peuvent être contournés assez facilement. Dans certains cas, l’opération est même triviale. . L’herbe n’est pas plus verte ailleurs : l’expert a réussi à contourner les mécanismes de protection de tous les principaux outils d’éditeurs tiers, y compris Kaspersky, Intego et Avira. . ===> Bref, l’utilisateur Mac n’est pas plus protégé qu’un utilisateur Windows. <=== . La seule différence, c’est que le nombre de malwares sur Mac est encore relativement faible. Mais ce n’est rassurant qu’à moitié. . En savoir plus / Learn more: . - http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
What was fixed?
The list of software components fixed in the various updates is extensive.
Rather than go into all the details, we'll just encourage you towards grabbing the updates by pointing out that the holes fixed include:
Remote code execution (RCE). Opening a booby-trapped file or browsing to a malicious web page could lead to implanted malware, stolen data and a hijacked computer. . Security bypasses. Files you might expect to be kept away from prying eyes might be visible; secrets useful for further attacks (such as memory addresses used by the operating system) might be revealed.
Denial of service. A crook could force your computer to shut down without warning. .
Data leakage. Passwords, private browsing data and application screenshots could be revealed. . Learn more:
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security
Apple diffuse une mise à jour pour son navigateur Safari. Elle permet de corriger plusieurs vulnérabilités de sécurité affectant le moteur de rendu WebKit.
Apple publie Safari 8.0.4, Safari 7.1.4 et Safari 6.2.4. Ces mises à jour pour le navigateur de la firme à la pomme sont à destination du système d'exploitation OS X Mountain Lion, Mavericks et Yosemite.
Ces mises à jour peuvent être obtenues depuis le menu Apple et le bouton " Mises à jour " ou depuis le Mac App Store. Elles ont pour but de corriger un total de dix-sept vulnérabilités de sécurité affectant le moteur de rendu WebKit.
En savoir plus / Learn more / Mehr erfahren:
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security
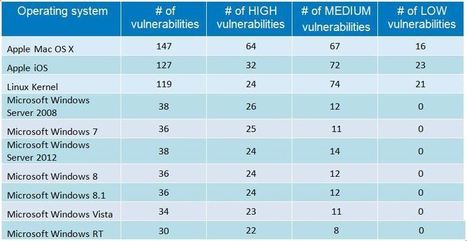
An average of 19 vulnerabilities per day were reported in 2014, according to the data from the National Vulnerability Database (NVD). In this article, I look at some of the trends and key findings for 2014 based on the NVD’s database. . #Mac OS X and #Linux had more #vulnerabilities in 2014 than ALL #Windows Versions in sum. .
Not surprisingly at all, web browsers continue to have the most security vulnerabilities because they are a popular gateway to access a server and to spread malware on the clients. Adobe free products and Java are the main challengers but web browsers have continuously topped the table for the last six years. Mozilla Firefox had the most vulnerabilities reported in 2009 and 2012; Google Chrome in 2010 and 2011; Internet Explorer was at the top for the last two years. To keep systems secure, it is critical that they are fully patched. IT admins should focus on (patch them first): - Operating systems (Windows, Linux, OS X)
- Web browsers
- Java
- Adobe free products (Flash Player, Reader, Shockwave Player, AIR).
. Learn more:

|
Scooped by
Gust MEES
|
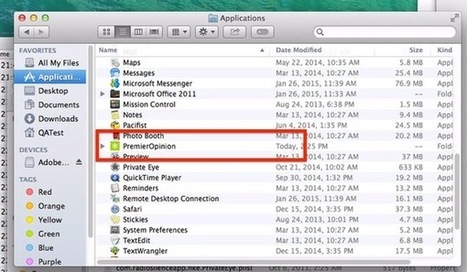
Almost five years ago, Intego security researchers warned about the OSX/OpinionSpy spyware infecting Mac computers, downloaded during the installation of innocent-sounding applications and screensavers distributed via well-known sites such as MacUpdate and VersionTracker.
Once compromised, infected Macs could leak data and open a backdoor for further abuse.
Now, sadly, a variant of OpinionSpy seems to be making something of a comeback.
Learn more:
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
Woburn, MA – February 10, 2015 - According to the Consumer Security Risk Survey conducted by Kaspersky Lab and B2B International, Apple users responded to have encountered cyber threats almost as often as the users of other platforms. The survey showed that 24 percent of Apple desktop users and 10 percent of Apple laptop users encountered malware during the year*, whereas the number of affected PC owners is slightly higher at 32 percent.
Although security experts have not, thus far, found as much harmful software for OS X as they have for other platforms like Windows, malware does still aim to attack Mac devices. Malware such as ransomware was reportedly faced by 13 percent of Mac users compared to 9 percent of Windows users. There is a similar situation with threats targeting financial data: these incidents were reported by 51 percent of OS X users and 43 percent of Windows users.
In addition the survey results showcased that Mac users are generally less aware of Internet threats than Windows users. For example, 39 percent of MacBook owners have never or hardly heard of ransomware, and 30 percent do not know about dangerous malicious programs that can exploit vulnerabilities in software. By comparison, among all respondents 33 percent know almost nothing about ransomware and 28 percent are unaware of exploits.
Learn more:
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
Adobe has released Flash Player 16.0.0.305, a new version that fixes the latest zero-day flaw (CVE-2015-0313) that is currently exploited in...

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
|

|
Scooped by
Gust MEES
|
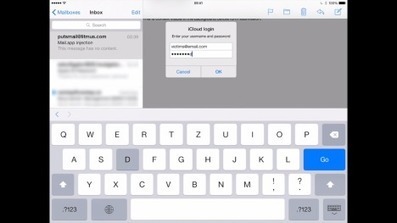
Der Sicherheitsexperte Jan Soucek hat einen äußerst gefährlichen Bug in der E-Mail-App von Apples iOS entdeckt. Ein Angreifer kann darüber eine Fake-Abfrage der Apple-ID einblenden - und so das Passwort abgreifen.
CHIP Online meint:
Auch wenn nicht jeder glücklich darüber sein dürfte, dass Soucek seinen Programm-Code mit der Veröffentlichung auch möglichen Angreifern bereitstellt, trifft die eigentliche Schuld Apple. Es ist eine äußerst fragwürdige Politik, eine Sicherheitslücke derartigen Ausmaßes einfach ein halbes Jahr zu ignorieren. Hier muss Apple nun unbedingt in kürzester Zeit nachbessern - spätestens mit der Veröffentlichung von iOS 8.4 Ende Juni.
Mehr erfahren/ Learn more:
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
A security firm has discovered a vulnerability in Apple’s Safari Browser that allows attackers to spoof legitimate websites and phish for user credentials.
Users are encouraged to watch out for spoofing attacks that redirect them to phishing schemes. To learn more about how to spot a phish, please click here.

|
Scooped by
Gust MEES
|
Vous vous souvenez de Rootpipe ? Cette vulnérabilité avait été signalée en fin d’année 2014 par un chercheur suédois qui avait découvert un moyen d’élever ses privilèges au niveau root depuis une session utilisateur. Rootpipe était restée une énigme jusqu’alors : Apple avait en effet annoncé que corriger cette vulnérabilité prendrait du temps et Emil Kvarnammar, le chercheur à l’origine de cette découverte, avait accepté d’attendre un patch avant de donner plus de détails. Le correctif était annoncé pour le début de l'année 2015, mais il aura fallu attendre encore un peu, Apple invoquant d'importants changements nécessaires afin de rectifier le tir.
En savoir plus / Learn more:
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security/?tag=RootPipe
Apple has released Security Update 2015-003 for OS X Yosemite v10.10.2 to address multiple vulnerabilities. Exploitation of one of these vulnerabilities may allow a remote attacker to take control of an affected system. US-CERT encourages users and administrators to review Apple Security Update 2015-003 and apply the necessary updates.
Learn more:
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
Five months on from the release of iOS 8, and following six rounds of bugfixes, Apple's flagship mobile platform that powers almost three out of four iPhone and iPads is still riddled with bugs.
I'm just going to come out and say it - this is a mess. If we were talking about cosmetic stuff like a badly laid out user interface or poor selection of wallpapers then I could overlook the issues, but they aren't. These are bugs relating to core systems such as Wi-Fi, cellular connectivity, Bluetooth, and stability and performance.
These are show-stopping bugs. These are bugs that quite frankly should have been sorted before iOS 8 was released, and definitely should have been pinned down after the first couple of updates.
But they aren't.
Learn more:
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
Major cyber security incidents continue to hit the headlines. Security and privacy are top concerns for IT and security professionals, especially after 2014’s highly publicized data breaches.
Companies around the globe were victim to malware, stolen data and exploited vulnerabilities. Big companies weren’t immune to this, with Target, JPMogan Chase, Home Depot and Sony Pictures suffering the painful sting of data breaches. Even celebrities were targeted, with compromised iCloud accounts.
It really isn’t surprising that almost everyone anticipates the need to prepare for security challenges in the coming months. According to a recent survey by Tech Pro Research, 84 percent of IT professionals are more concerned about security and privacy in 2015.

|
Scooped by
Gust MEES
|
Apple is pushing out a mandatory update for Adobe Flash in the wake of the recent disclosure of three zero-day vulnerabilities that are actively being exploited in the wild.
Mac OS X will find that Flash has been disabled on their devices and will see popup messages urging them to install the latest updates if they want to continue to use the software.
“If you’re using an out-of-date version of the Adobe Flash Player plug-in, you may see the message ‘Blocked plug-in’, ‘Flash Security Alert’ or ‘Flash out-of-date’ when attempting to view Flash content in Safari. To continue viewing Flash content, update to a later version of Adobe Flash Player. Click the Download Flash button. Safari opens the Adobe Flash Player page on the Adobe website,” the advisory from Apple stated.
Learn more:
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
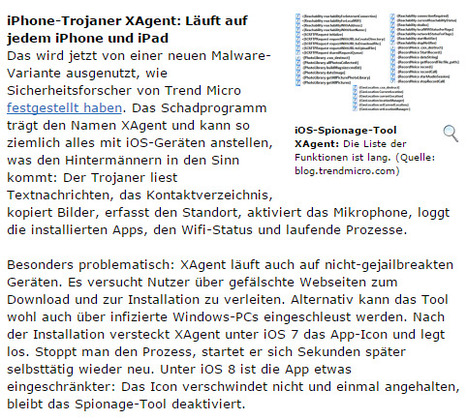
Kurz nachdem bekannt wurde, dass über Googles Play Store millionenfach Adware-Tools heruntergeladen wurden, erwischt es Apple-Nutzer: Sicherheitsforscher haben Spionagetools enttarnt, die iOS-User belauschen und ihre Daten kopieren. Eines der Programme läuft sogar auf vermeintliche sicheren iPhones, die nicht gejailbreakt wurden.
Learn more:
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
|



 Your new post is loading...
Your new post is loading...






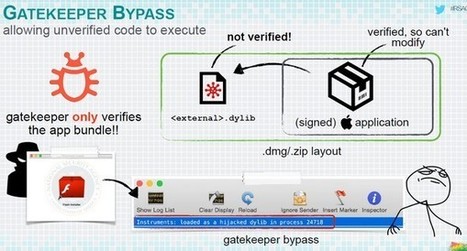
















Researchers at BAE just reported on a Mac bot known as OSX/Agent-ANTU that was allegedly distributed in a novel way.
The crooks used a security hole in a controversial Mac security and cleanup utility called MacKeeper.
MacKeeper quickly patched the hole after it became known, but until you received the update you were at risk of a Remote Code Execution (RCE) hole.
As long as you were unpatched, a crook could simply entice or redirect you to a poisoned website, and use a single line of JavaScript to send a command script to MacKeeper, which would then run it.
Unfortunately, according to BAE, some crooks struck while the iron was hot.
The crooks sent unpatched MacKeeper users to a web page that tricked their Macs into downloading the OSX/Agent-ANTU malware.
Here are some examples we've seen over the years where the Windows malware "playbook" has been followed, in some cases extremely effectively, on OS X:
2012: Java-based exploit. The Flashback malware was injected onto your Mac via an unpatched Java bug. Flashback was a bot, or zombie, meaning that crooks could remotely send it instructions to help them commit further cybercrime. Estimates suggest that more than 600,000 Macs ended up infected, supposedly including "274 from Cupertino."
2013: Word-based exploit. SophosLabs reported on attackers using an exploitable bug in Microsoft Word for Mac to target Chinese minority groups. If you opened a booby-trapped document, disguised as some sort of political commentary, the crooks got control of your Mac via zombie malware called OSX/Agent-AADL.
2014: Fake "undelivered item" documents. If you opened the bogus PDF file, really an application in disguise, you could end up infected with a data-stealing Trojan called OSX/LaoShu-A. Amongst other things, this one would find files such as documents, spreadsheets, presentations and archives...and send them to the crooks.
So, if you haven't yet crossed the bridge and become a Mac anti-virus user, now would be a good time to give it a go.
Learn more:
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security