New report on what researchers call one of the 'most sophisticated mobile botnets online' shows how profitable mobile malware has become.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Botnet
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Mobile+Botnet



 Your new post is loading...
Your new post is loading...







![BYOD Security Issues [Infographic] | ICT Security-Sécurité PC et Internet | Scoop.it](https://img.scoop.it/CaiNaHRcRGZDVZM2V3tufTl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)












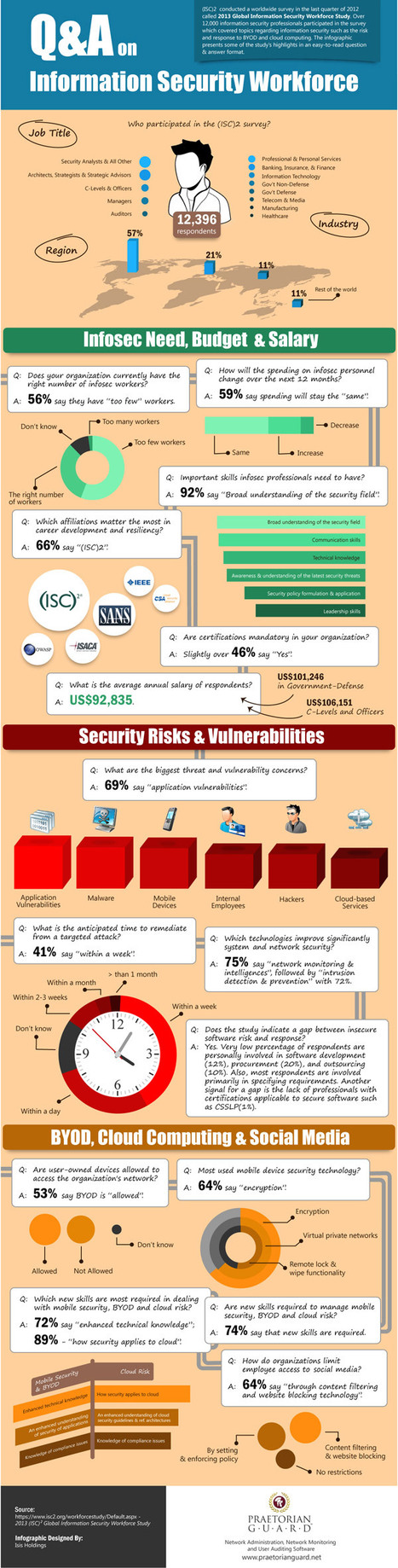







Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Botnet
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Mobile+Botnet